In this post, Wade Woolwine, managed services director of technology at Rapid7, details our approach to managed detection and response: visibility, analytics, and arming our analysts with smart, customizable automation.
Defending the modern enterprise is hard work. Between the need for round-the-clock coverage, technology to provide full visibility across the expanding enterprise, a highly skilled and experienced team, and the business level pressure to “prevent a breach,” there is little wonder why we are losing more than we are winning. As a result, organizations that understand the need for threat detection and response, but lack the capital or available headcount to do it themselves, are turning to Managed Detection and Response (MDR) service providers such as Rapid7.
MDR offers people and technology as a bundled package, with the expectation that the provider extend beyond traditional Managed Security Services to directly relieve major pain points: (1) detect compromise as it happens, (2) provide response expertise for any escalated incidents, and (3) help customers identify risk so they can proactively improve security posture. With such a promise, it’s essential to choose a vendor that can actually deliver.
Each provider has a different strategy or scope of data collection, whether it be endpoint detection and response (EDR), network detection, log correlation, or a “proprietary black-box AI.” Further, each provider has a different engagement model, different fine print in the level of services received, and ultimately a different customer experience. While the various bells and whistles can help improve your overall experience, the worst possible outcome is if that provider doesn’t identify a threat in time and the business suffers financial or reputation impact.
What Threats Can You Detect With Your Data?
If you’re in the market for a managed threat detection and response provider, how can you evaluate a vendor’s ability to identify threats? The most basic factor is visibility. Smart people can’t find what they can’t see. If your MDR provider is focused only on logs, or the network, or the endpoint, they may lack visibility to protect what matters to you the most. First, consider the following:
- Where does my most valuable data reside?
- What would cause the worst reputation impact to my business?
Then, ask this of a potential provider:
- Will you collect logs from my most critical systems/applications? (This includes systems and applications outside of the traditional network, e.g. cloud services)
- Can you analyze endpoint events from my critical systems?
- Are you able to monitor if an attacker impersonates as one of my employees?
- Can you centralize and analyze events from my existing security technology?
- Can you demonstrate how you detect malicious tools, tactics, and procedures across the entire attack lifecycle?
Using Rapid7’s InsightIDR technology, our MDR service has full visibility into (1) logs, (2) existing IT and security investments, (3) your user authentication and authorizations, (4) your endpoints, and (5) cloud-based services.
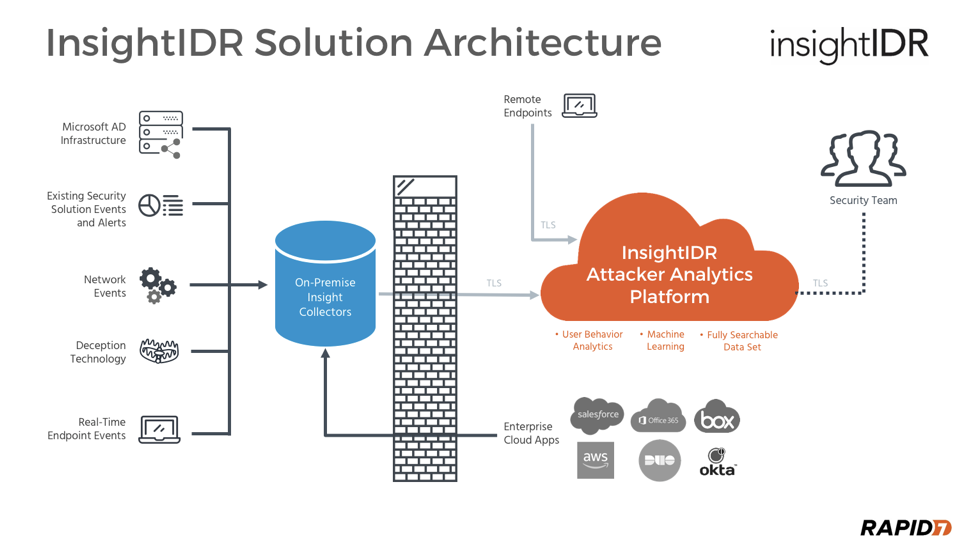
With this visibility backed by a cloud-based, fully scalable data collection model, we can begin to apply layered detection methodologies across your entire environment to maximize our ability to detect threats—before financial or reputational damage occurs.
Data Analytics, Investigation, and Response
Once you’re satisfied with the scope of your provider’s data collection, validate their approach to detecting threats. At its most basic, there are three types of threats:
Common Threats
These threats don’t specifically target your organization, but take advantage of common weaknesses in technology environments (which can include people), and use automation to spread. The motivations are typically to gain a small amount of money from a large group of affected systems and people. Some examples include crypto-based threats (where data is held hostage for ransom), viruses that steal banking or social credentials, or botnets that are rented to perpetrate other attacks like distributed denial of service (DDoS) or bitcoin mining. Generally speaking, these types of threats can be prevented using technology such as A/V, IPS, web proxies, and other specialized tools that leverage threat intelligence and trained machine learning.
Targeted Threats
These threats target a specific person, organization, government, or industry with very specific missions. These threat actors are usually professionals who perform these acts for financial compensation, political agenda advancement, or nationalism. These are the threats you hear about in the news. These are the threats that not only cause severe financial impact to your customers and the business, but can also cause loss of competitive advantage in your industry and reputation damage. Generally speaking, these types of threats need to be detected by a combination of skilled and experienced people coupled with the right technology.
Insider Threats
These threats are the hardest to manage. Business insiders use their privileged access as a trusted employee to steal and sell data to competitors or other interested parties. Generally speaking, identifying insider threats requires a strong partnership between human resources and the security department, coupled with highly specialized behavior analysis tools and people. Because insiders already have access, but aren’t always stealing data, looking for unusual behaviors in the data access and data exfiltration steps of the attack chain is critical.
With a basic understanding of threat types, you can ask a provider how they will protect your various systems, applications, data, and users from each type. For Rapid7’s managed threat detection and response services, we apply four threat detection methodologies against data from your network, endpoints, users, logs, cloud applications and services, and existing security technology:
Traditional threat intelligence: Using this methodology, IP addresses, domains, and file hashes are matched against Rapid7’s threat intelligence curated by Rebekah Brown and the Threat Intelligence Team, Mike Scutt and the MDR SOC analysts, Tim Stiller and the Incident Response Team, and the various projects from the Rapid7 Labs team including Project Sonar and Project Heisenberg. Additionally, we are proud, good standing members and on the board of directors for the Cyber Threat Alliance and have established public, commercial, and private partnerships for intelligence sharing. This enables Rapid7 MDR to detect and validate common threats across the traditional and modern enterprise network.
Attacker Behavior Analytics (ABA): Complementing MDR’s ability to detect known tools and threats, our analysts and researchers also strive to detect behaviors associated with attacks and attackers. Our premise is that the tools change often, but the behaviors largely remain the same. During threat validation and incident response, analysts research the events and evidence leading up to the threat or discovered breach. Our SOC analysts and threat intel teams then create detections that look for specific events and evidence that match these specific behaviors. This partnership between our SOCs and InsightIDR engineering teams has led to a data collection and analysis engine that is specifically built for attacker behavior detection. Using this methodology, Rapid7 MDR detects 0-day common threats, targeted threats in all stages of the attack lifecycle, and certain insider threats across the traditional and modern network enterprise network. Learn more about Rapid7’s attacker behavior analytics solution.
User Behavior Analytics (UBA): According to the 2018 Verizon DBIR, the use of stolen credentials and phishing are the first and third most common actions behind confirmed breaches (RAM scrapers came in number two). Understanding typical user behavior and asset relationships is critical when detecting threats in the reconnaissance, lateral movement, and persistence phases of the attack lifecycle. Rapid7’s InsightIDR has the leading user behavior analytics engine to establish a healthy baseline and alert on signs indicative of compromise. Using this methodology, Rapid7 MDR detects destructive common malware (such as worms and crypto-malware), targeted attacks in specific phases of the attack lifecycle, and most insider threats.
Monthly threat hunts: This is the safety net methodology. On a monthly basis, MDR SOC analysts perform a human driven, in-depth threat hunt across forensics artifacts generated from the traditional and modern enterprise network. The visibility provided by the data collection abilities of InsightIDR, data analysis techniques such as frequency analysis, and a purpose-built threat hunting user interface give the MDR SOC analysts the ability to hunt for threats that may have evaded our other three detection methodologies. Using this methodology, Rapid7 MDR detects 0-day common threats, targeted threats at all stages of the attack lifecycle, and identifies potential avenues for insider threats to steal and exfiltrate your data.
By getting 100% visibility across your network with our purpose built SIEM, deep visibility into your endpoints, a focus on the user as a key element behind successful breaches, and a layered, overlapping application of multiple threat detection methodologies, Rapid7 Managed Threat Detection and Response Services provides your team with effective, partnership-driven detection and response capabilities.