When you think about vulnerability management, what comes to mind? If you’re like most companies, you think only about technology and tools. Unfortunately, this is where most get it wrong. Here at Rapid7, we have worked with companies of all shapes and sizes and witnessed firsthand their struggles when it comes to vulnerability management. If you are having difficulties in this area, you are not alone.
In our latest webcast, we explain why most vulnerability management programs fail and what you can do to avoid the same fate. Access the full webcast training for the steps you need to take to improve your program, and see our brief recap below:
[Webcast] Why Vulnerability Management Programs Fail and What You Can Do About It.
Watch NowBack to basics
First things first, the purpose of a vulnerability management program is to reduce risk within your environment. You cannot fix what you don’t know is present, and by properly identifying risk, you can get a better hold on your security posture. Vulnerability management is so important today that it was actually moved up to CIS Version 7 Control 3 to ensure organizations address it early on.
It is important to begin your vulnerability management program by conducting a baseline assessment to understand your current risk level. It’s equally vital to understand your organization’s risk appetite. Leadership should be involved here to help determine the level of risk your company is and isn’t willing to accept so you can tailor your vulnerability management program accordingly.
What a successful vulnerability management program is—and isn’t
A successful vulnerability management program isn’t just about having [the best vulnerability management tool] or service in place. While tooling is important, solely conducting [vulnerability scans] doesn’t mean you have a true program in place. Not nearly enough organizations take the time to carefully plan for what to scan, which leaves gaping holes in vulnerability identification. This often comes from a lack of understanding what needs to be scanned.
Running an effective vulnerability assessment program also means having leadership on board and the resources you need. If you do not have leadership on your side or the necessary resources, you need to find out why. Is it a budget problem, or do you lack the support of your C-suite or board of directors? Without leadership support, security initiatives can fall flat, which leaves little incentive for the rest of the organization to prioritize security. This can also lead to issues between IT and security teams. If the security team runs the vulnerability management program and is sending issues to IT without leadership support, it can be difficult to get IT to take the program seriously.
Additionally, without resources, it’s going to be next to impossible to identify vulnerabilities, assess their impact, then remediate them through patching and configurations. Identifying the vulnerabilities is often the easy part, while finding the time and resources to fix them can be much more challenging and time-consuming.
Vulnerability management as a security best practice
In many ways, vulnerability management is a foundational element of any security program. The goal is to reduce risk, which will benefit every security initiative.
In the webcast, we dive into the vulnerability management lifecycle, detailing where companies go wrong at each of the 10 steps and what you can do to fix it.
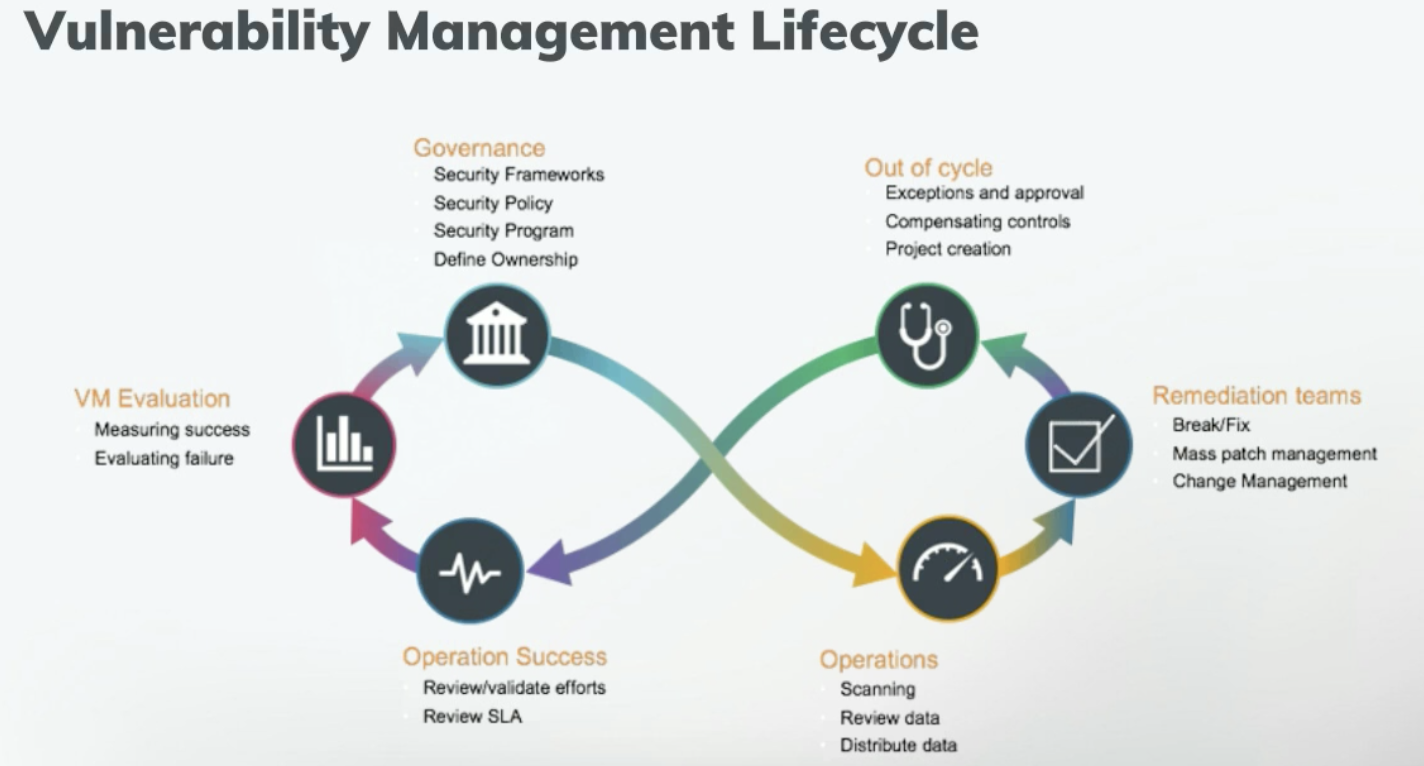
Specifically, we explain how to overcome the most common missteps in the following areas:
- Governance
- Operations
- Asset management
- Scanning accounts
- Scope definition
- Classification and prioritization
- Change management
- Remediation
- Verification
- Reporting
These 10 steps lay the foundation for success in any well-rounded program. They establish the right tooling to scan and patch vulnerabilities, aid in handling exceptions, define remediation strategies, and measure progress, among other tasks. The rest of the chain of events can fall apart if any one of these is done haphazardly or without oversight.
When you view vulnerability management as more than just a scanning or patching tool and actually take the time to build a successful foundation that involves policies, procedures, change management, and so on, you not only set up your vulnerability management program for success, but also your entire security program.
