Many thanks to Jon Hart, who collaborated on this research.
What we know about the Cisco® router vulnerability (CVE-2019-1663)
This week, Cisco® released an advisory and patch for a remote code execution flaw in small-business routers used for wireless connectivity in small offices and home offices. If the web-based interface is enabled on these devices, attackers can execute arbitrary code on the underlying operating system of the affected device as a high-privilege user.
Organizations are encouraged to apply this patch to all affected devices as soon as possible given the severity of the vulnerability and especially if they expose the web admin page to the internet.
What is the impact of the Cisco® router vulnerability?
Rapid7 Labs was again able to determine the possible extent of the exposure without resorting to configuring a new Project Sonar scan, since Cisco® provides SSL certificates for these devices, and they are all self-signed SSL certificates with the subject serialNumber field containing both the model type along with the device serial number:
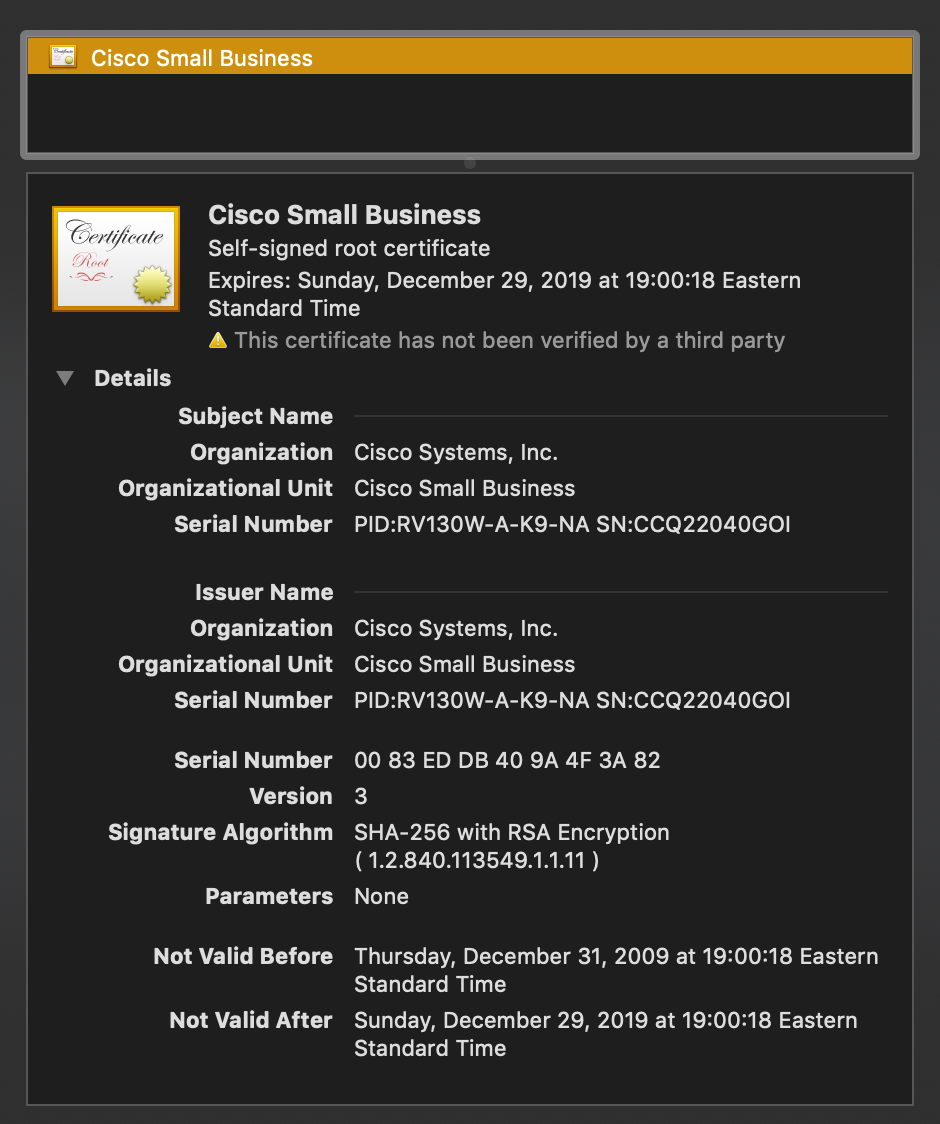
Interestingly enough, according to RFC 5280, the serialNumber field technically:
MUST be a positive integer assigned by the CA to each certificate. It MUST be unique for each certificate issued by a given CA (i.e., the issuer name and serial number identify a unique certificate). CAs MUST force the serialNumber to be a non-negative integer.
This just begs for a Princess Bride reference: "You keep using that word. I do not think it means what you think it means."
Rapid7 Labs has been able to determine that there are just shy of 12,000 exposed devices on the internet:
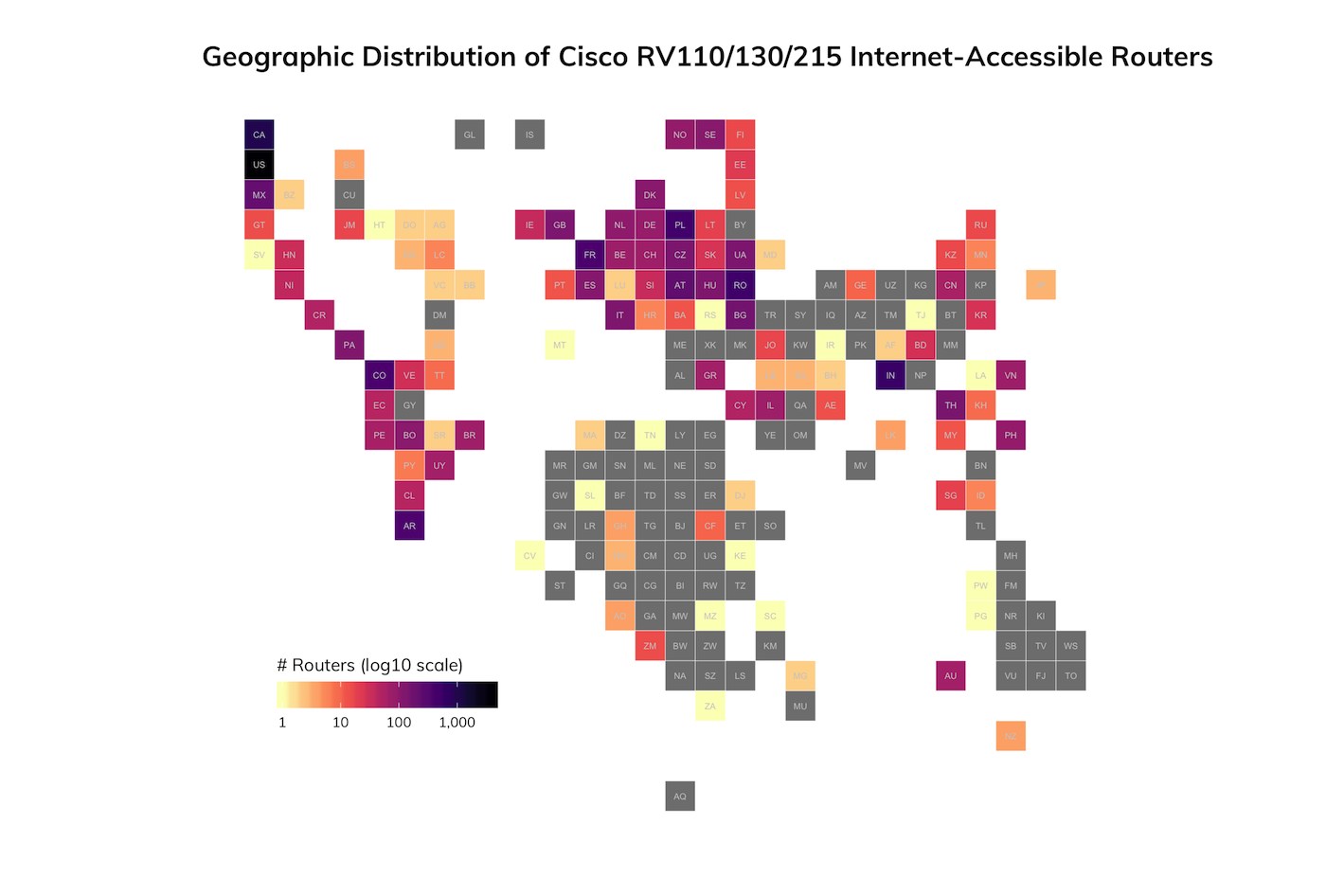
Once again, these routers are mostly found on residential or small-business ISP networks, which is to be expected given the use case for these wireless routers. Nearly all of the exposed devices were found listening on the default HTTPS port, 443/TCP, or common alternate HTTPS ports such as 8443/TCP + 9443/TCP, and a handful of other ports.
Every single one of these routers is vulnerable to the RCE attack unless they apply the available patch.
Rapid7 Labs will be monitoring our Project Lorelei honeypots for signs of attackers looking to exploit this critical vulnerability.
Cisco® is a registered trademark of Cisco Systems, Inc. and/or its affiliates in the United States and certain other countries.
