Have you ever tried to figure out why a vulnerability or policy scan isn’t showing you the results you expect, even though you’ve provided credentials? If so, you’ll be pleased to hear that the November 3rd release of Nexpose and InsightVM (version 6.6.112) will introduce a new check category designed to help troubleshoot issues with credentialed scanning: Scan Diagnostics.
No more combing through scan logs to get answers! These checks will be disabled by default, but you can configure them to run by adjusting your scan templates. When enabled, Scan Diagnostics checks will report a “vulnerable” result against assets when the Scan Engine is supplied with credentials but unable to gather local information.
The challenge of finding the right fix
For complete and accurate coverage, the InsightVM Scan Engine requires local access to systems being scanned. Most Microsoft checks are based on values found in the Windows Registry. Checks for Linux distributions typically require access to the package manager, which is important for vulnerability correlation (cutting down on noise due to backported fixes).
This means that for many types of scans, you need to tell the engine how it should authenticate by configuring credentials. When things go smoothly, the engine will collect all the data it needs for vulnerability or policy assessments. But when results aren’t as expected, it can be challenging to understand what went wrong.
The way the Security Console currently indicates authentication status results is rather coarse-grained. Credential Success means it’s all good, but a Credential Failure (or the puzzling “Partial Credential Success”) can often leave a VM analyst scratching their head about how to fix things.
Bringing greater visibility to your scanning environment
Our new Scan Diagnostics checks provide more detailed visibility into where things fell apart. Because the results are written as vulnerability checks, you’ll be able to use a lot of familiar product functionality to work with them. They can be enabled or disabled via scan templates, and you can report on them like any other category. We’ll also be providing solution information to make it easier to resolve issues, and you can look at the proof the scanner provides to get additional context.
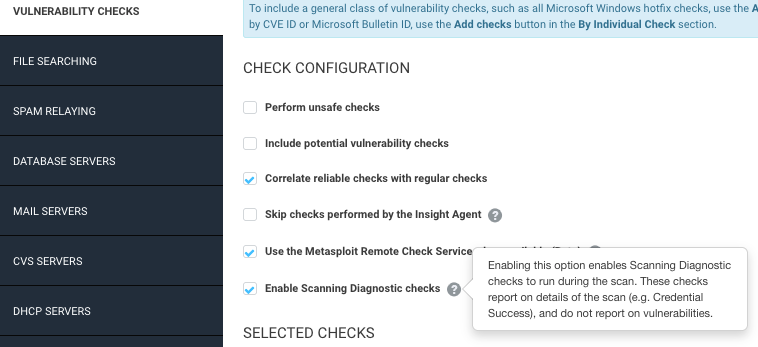
Another advantage of using check results for Scan Diagnostics is that they are built atop the expert system at the core of the scanner. This helps Scan Diagnostics target the most precise cause of an error and provide guidance accordingly. No more going through a laundry list of checkboxes to make sure your sites and assets are configured correctly.
Here is the initial set of Scan Diagnostics we’ll be releasing:
| Credential Type | Check ID | Summary |
|---|---|---|
| AS400 | rapid7-diagnostics-as400-service-usable | No usable AS400 service |
| SNMP | rapid7-diagnostics-snmp-service-usable | No usable SNMP service |
| Telnet | rapid7-diagnostics-telnet-service-usable | No usable Telnet service |
| SSH | rapid7-diagnostics-privilege-elevation-failed-cisco | Cisco SSH privilege elevation failed for the scan |
| rapid7-diagnostics-privilege-elevation-failed-unix | Unix SSH privilege elevation failed for the scan | |
| rapid7-diagnostics-ssh-algorithm-compatibility | SSH algorithm mismatch between scan engine and target | |
| rapid7-diagnostics-unix-privilege-elevation-root | SSH credential is configured to elevate to a non-root user | |
| rapid7-diagnostics-unix-variant-authenticated-with-non-root-account | No SSH credentials with root privileges configured | |
| CIFS | rapid7-diagnostics-cifs-read-access-errors | Access errors while attempting to read from the file system |
| rapid7-diagnostics-cifs-sam-access-errors | Unable to access the remote Security Account Manager | |
| rapid7-diagnostics-cifs-sam-unknown-error | Unknown error while trying to access the remote Security Account Manager | |
| rapid7-diagnostics-cifs-write-access-errors | Access errors while attempting to write to the file system | |
| rapid7-diagnostics-smb2-share-access | Unable to obtain access to SMB2 shares | |
| rapid7-diagnostics-windows-registry-access-issues | Access issues interacting with the Windows Registry | |
| rapid7-diagnostics-windows-registry-enable-services-template | Windows Services not enabled in template | |
| rapid7-diagnostics-windows-registry-failed-to-enable-services | Failed to enable Windows Services | |
| rapid7-diagnostics-windows-registry-unexpected-error | Failed to connect to the Remote Registry Service | |
| rapid7-diagnostics-wmi-connection-error | Unable to connect to the WMI Service | |
| rapid7-diagnostics-wmi-dcom-port-error | Error when connecting to DCOM Ports (required for WMI) | |
| rapid7-diagnostics-wmi-permission-error | Permission error when connecting to the WMI Service | |
| rapid7-diagnostics-wmi-read-access-errors | Access errors encountered in attempts to read over WMI | |
| rapid7-diagnostics-wmi-unknown-error | Unknown error occurred trying to connect to the WMI Service | |
| rapid7-diagnostics-winrm-authentication-error | Authentication error when connecting to the WMI Service | |
| rapid7-diagnostics-winrm-listener-error | The WinRM listener on the target appears to be blocking the scan engine from connecting | |
| rapid7-diagnostics-winrm-unknown-error | Unknown error occurred trying to connect to the WinRM Service | |
| rapid7-diagnostics-winrm-unencrypted | The WinRM service is operating over an unencrypted protocol, potentially leaking valuable data |
Note that these “vulnerabilities” carry the lowest possible severity and will not increase your risk score. However, they may increase overall vulnerability counts, so we’re leaving them turned off by default for now. If you do scan with them, you can adjust the scope of generated reports to exclude these results if you don’t want them to get passed through to remediation teams.
The existing status shown in the Authentication column of Scan Results and Node pages will remain the same for the time being, so that it is available regardless of whether this new Scan Diagnostics check type is enabled and won’t adjust anything on the corresponding dashboard card.
We’d love to hear any feedback on this new feature! Please reach out to your Customer Success Manager to let them know how it’s working out in your scans.
NEVER MISS A BLOG
Get the latest stories, expertise, and news about security today.
Subscribe