Rapid7 Research
2020: Q1 Threat Report
By Bob Rudis, Senior Director, Chief Security Data Scientist at Rapid7
Wade Woolwine, Principal Threat Intelligence Researcher at Rapid7
Kwan Lin, Principal Data Scientist at Rapid7
June 3, 2020
What is a threat?
When there is an adversary with the intent,
capability, and opportunity, a threat exists.
When two or more of these elements are
present (e.g., intent and capability, but no
opportunity), we call it an impending threat,
because there is just one missing piece before
it becomes a true threat.
When there is just one element present
(e.g., an opportunity in the form of a software
vulnerability), we call it a potential threat. There
is the potential for it to turn into a true threat,
although there are additional components that
need to come to fruition before it has a real
impact to most organizations.
Introduction
We hope this edition of Rapid7’s quarterly threat readout finds you safe (at least from poorly crafted pandemic-themed marketing emails). There is no doubt that the key theme for the first quarter of 2020 is “the new normal” in our lives and in our workplaces. It has been a time of change, adaptation, confusion, and fear. In other words, the perfect recipe for attackers. For this quarterly report, we have decided to focus on threats originating from COVID-19 or the changes to our lifestyles, workstyles, and the threat landscape.
Our “Focus on Threat Telemetry” explores the most severe vulnerabilities of the quarter and authentication abuse against key business services. This quarter, enterprise applications are vulnerable and under attack. From remote access technology, to Microsoft Exchange and VMWare vCenter, critical applications go unpatched and are targeted by attackers. Rapid7’s Managed Detection and Response (MDR) incident response team responded to nine incidents involving the exploitation of publicly facing vulnerabilities.
Our “Focus on Detection Telemetry” explores spear-phishing and the impact of credential theft. This quarter, single third-party data breach disclosures impacted 80 MDR customers and 286 credentials, highlighting the need for user education on approved use of business credentials. Fifty-five percent of malware threats reported by the MDR SOC were not detected by traditional threat prevention software. To gain visibility into the threats security teams are missing, organizations must invest in technology and security analyst training for user behavior anomalies, attacker behavior detection, process behavior anomalies, and next-gen threat protection.
Our “Focus on Recommendations” section explores best practices to secure the remote asset in the home network and prepare the enterprise security program for a recession. Business users in their homes must ensure their networks and devices aren’t introducing threats through outdated router firmware and pre-existing infections. Enterprise security teams need tools that enable the monitoring and remediation of threats on the remote endpoints. Security leaders can begin to lay down a strategy for how the security program can survive in the face of layoffs and budget cuts.
Focus on Threat Telemetry
Now, more than ever, it seems like Rapid7’s Emergent Response team has been working overtime. This team comes together to evaluate, build content for, and disseminate notifications about new threats and vulnerabilities to our customers and the community. We’re not sure what the vulnerability researchers are putting in their coffee, but it didn’t seem like a week went by without another major enterprise vulnerability. As such, this quarter we’ve chosen to highlight some of the most impactful ones.
Remote Access Under Attack
Back in January, Rapid7 Labs provided guidance on a remote code execution weakness in Citrix NetScaler devices due to the critical nature of the vulnerabilities and evidence of attacker reconnaissance and compromise activity. We’ve continued to see internet-wide scans looking for this vulnerability in January, February, and March, but none in April. There could be many reasons for this, paramount of which is that the vulnerable targets are now fairly established.
The community on AttackerKB.com—a new resource that highlights the diverse perspectives of security community members on which vulnerabilities make the most appealing targets for attackers—has provided five assessments rating this vulnerability as VERY HIGH for both attacker value and exploitability.
However, Citrix has not been the only target:
Pulse Secure
- Arbitrary file reading vulnerability with two AttackerKB.com assessments rating this vulnerability as VERY HIGH in both attacker value and exploitability
- Arbitrary command execution with one AttackerKB.com assessment rating this vulnerability as LOW in attacker value and VERY HIGH in exploitability
Fortinet
- Arbitrary file reading vulnerability with one AttackerKB.com assessment rating this vulnerability as VERY HIGH in both attacker value and exploitability
- Unauthenticated user password modification with one AttackerKB.com assessment rating this vulnerability as MEDIUM in both attacker value and exploitability
- Unauthenticated web service DoS with one AttackerKB.com assessment rating this vulnerability as LOW in both attacker value and exploitability
Cisco
- Arbitrary file read and delete with one AttackerKB.com assessment rating this vulnerability as MEDIUM attacker value and VERY HIGH exploitability
- Memory content disclosure with one AttackerKB.com assessment rating this vulnerability as VERY HIGH attacker value and HIGH exploitability
Palo Alto has an unauthenticated remote code execution vulnerability (be the first to rate it on AttackerKB.com!)
As you will read in the “Focus on Detection Telemetry” section of the report, Rapid7’s MDR incident response team investigated nine breaches resulting from the successful exploitation of the NetScaler issue. Attackers are actively exploiting these vulnerabilities.
Microsoft Exchange Outlook Web Application (OWA)
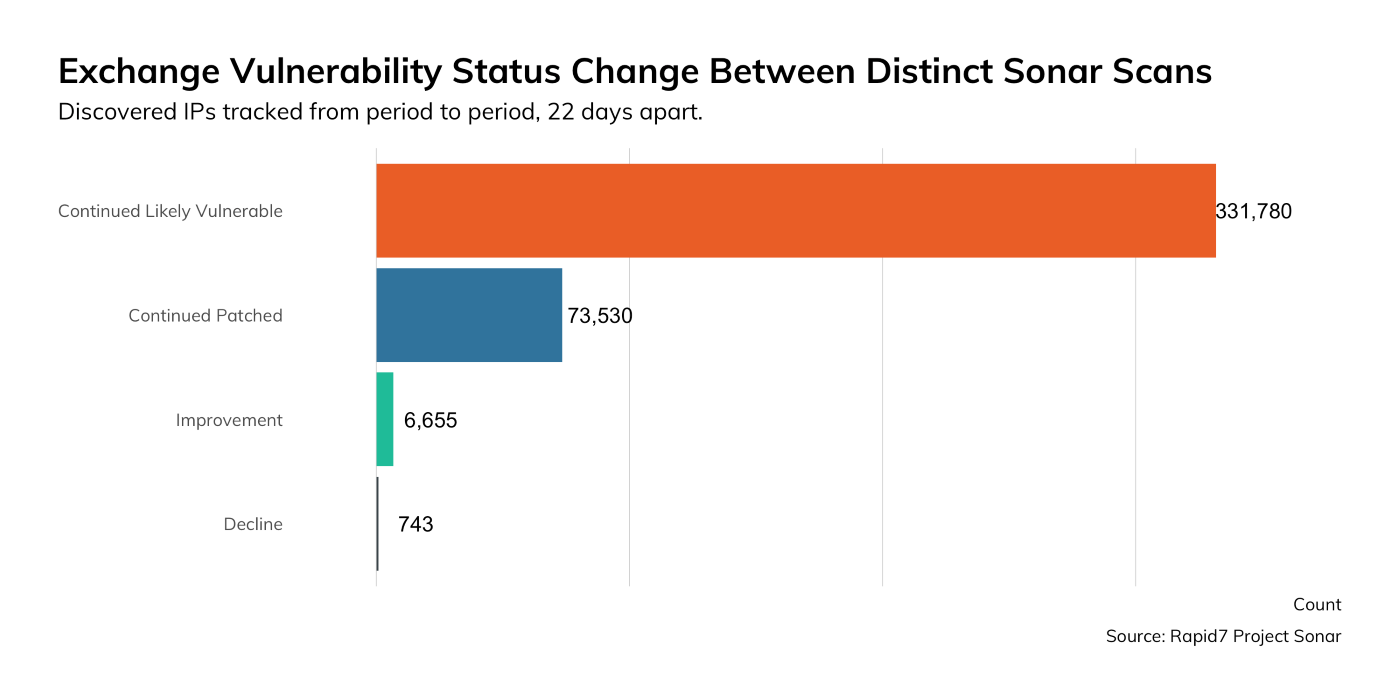
On Feb. 11, 2020, Microsoft released security updates to address a vulnerability in Microsoft Exchange (CVE-2020-0688) that would allow an attacker to turn any stolen Exchange user account into a complete system compromise. This vulnerability, coupled with the insights on credential compromises from the Detection Telemetry section of this report, highlights the importance of a quick turnaround for this patch. Alas, while we have seen some patching, we have actually seen an additional increase in the total number of vulnerable servers in the data.
To summarize our findings:
- Over 350,000 Microsoft Exchange servers on the internet exposing a vulnerable version
- This equates to approximately 82% of the total population of approximately 426,000 Microsoft Exchange servers surveyed
- We have identified log artifacts that potential victims can use to establish if they have been compromised
- As of this writing, we've seen under 7,000 newly patched systems between the original study in late March and the most recent studies in late April.
To read the full findings, check out our blog post.
This vulnerability really terrifies us (and if you've seen one of our author's Halloween decorations, you'll know, that's saying something). The sensitive data that is exchanged over email, and the ease with which an attacker can social engineer their way into valid credentials, combined with the limitless impact of owning access to executive mailboxes makes this worthy of a critical priority, drop-everything-else-now patch.
Even the community over at AttackerKB.com offered nine assessments rating the vulnerability between HIGH and VERY HIGH for attacker value and HIGH for exploitability.
VMWare vCenter
While we don't typically cover vulnerabilities in the Threat Report unless there is significant exposure, this next one is an exception to remind us that our attack surface isn't just what attackers see outside, but what malicious insiders can see inside. On April 9, 2020, VMware notified customers of an information disclosure vulnerability in the`vmdir` directory service (their fancy term for an LDAP server). While the vulnerability was technically disclosed in April, the Rapid7 Labs team has added it to this Q1 2020 synopsis since the issue is far greater than a mere information disclosure and there appears to be a non-insubstantial vCenter `vmdir` presence on the internet.
Unfortunately for vCenter users, this vulnerability also allows anyone with unauthenticated network access to create arbitrary users in vCenter, allowing for full unauthorized access to the vCenter environment and the virtual machines within. This means all those instances of vCenter hanging off of flat or open access internal networks are also at risk from any attacker who manages to gain initial access from a successful phishing attack or any internal, trusted user who may go rogue.
As it turns out, the community over at AttackerKB.com has provided five evaluations rating this vulnerability as VERY HIGH for both attacker value and exploitability.
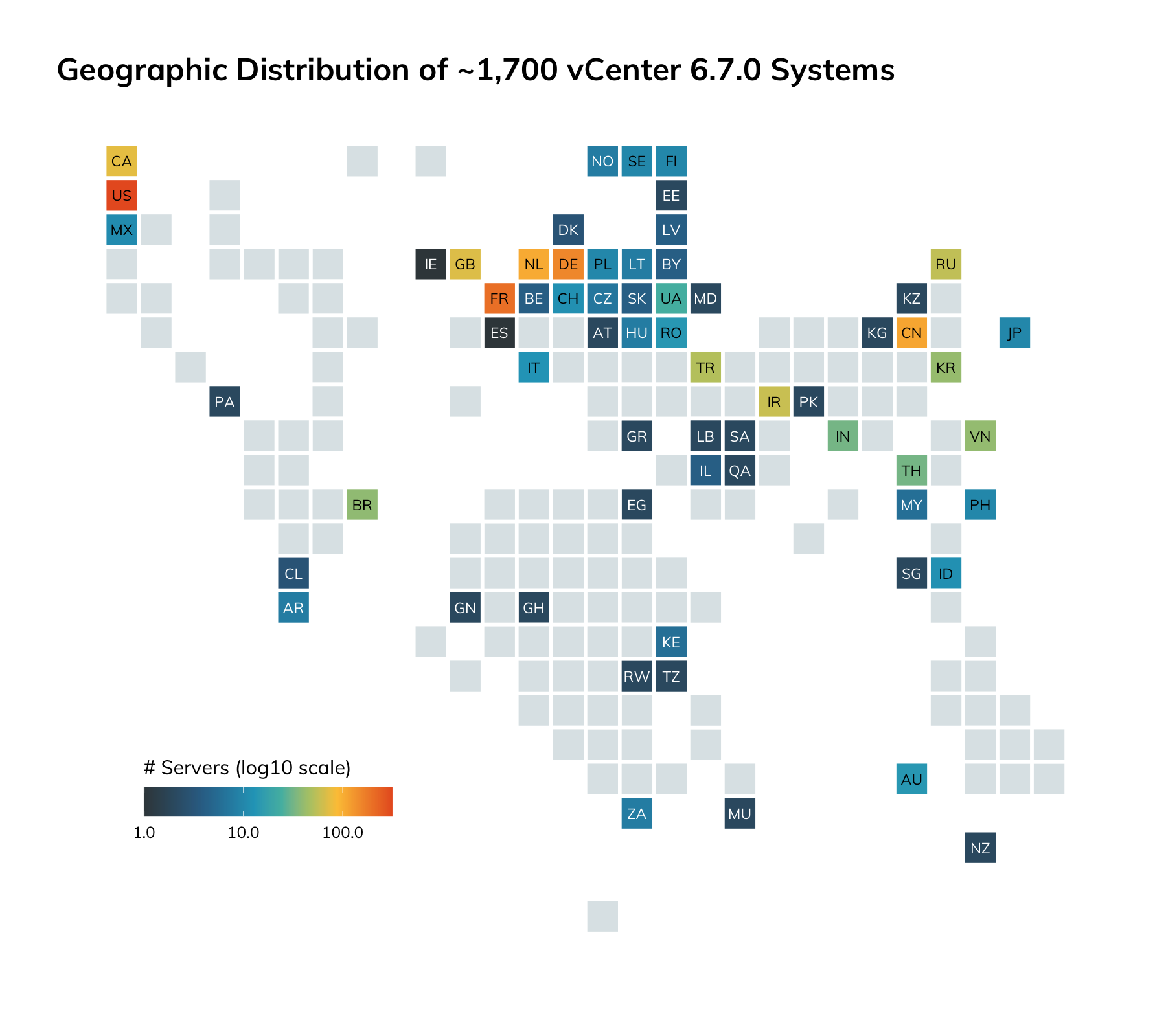
While our telemetry data only shows about 1,700 instances exposed to the internet, this vulnerability is perfect for any attacker or unauthorized user who wants to gain access to the data or computer power within vCenter.
If you happen to be one of the 900 exposing vCenter to the internet, please fix that. For everyone else with vCenter, in addition to patching, consider network-based controls to only allow access to vCenter from approved addresses or networks.
Key Takeaways
In these challenging times, remote access, email, and virtualization are all critical services that can no longer be treated as also-rans. The Labs team is in regular contact with organizations of all shapes and sizes, and we’ve noticed some of them have “streamlined operations,” which is a nice way of saying they’ve relaxed controls and restricted changes to systems since there’s no human to go over and press the big red on/off button when there’s an issue. Critical vulnerabilities are, well, critical, and need to be treated as such.
- Subscribe to all vendor security notifications, especially for internet-facing applications and components of those applications.
- Patch your remote access/collaboration services with a vengeance.
- Monitor CISA (USA🇺🇸), NCSC (GBR🇬🇧), CCS (CAN🇨🇦), ACSC (AUS🇦🇺), NCSC (NZL🇳🇿) and other country-level agency cybersecurity alerts as they are low-noise, high-fidelity updates that focus on either active exploitation or critical vulnerabilities, and such bulletins are sometimes winking at privileged, insider information.
- Perform enhanced monitoring on all internet-facing systems—especially remote access solutions—and patch or mitigate known weaknesses as soon as possible.
- Did we mention you should patch ASAP? As you know, many organizations are struggling with timely patching even in the best of times, but attackers know when your internet-facing systems aren't patched and you may need to put other IT operations tasks on the back burner to ensure these highly targeted and vital components are in a safe configuration.
Focus on Detection Telemetry
For this quarter, the focus on detections telemetry is spent in three key areas: the threats to the user, the impact to credentials, and the impact to the endpoint. Between Threat Reports, we were able to refine our data-gathering methodology and technology to leverage new context sources that help us better understand threats and impacts.
Starting with a very broad analysis of the data, we see that the Financial, Professional, and Manufacturing sectors were most targeted in the first quarter. The end user continues to be the favorite prey for attackers: 96% of Rapid7's MDR Findings Reports describing end user compromises, with 74% identifying compromised credentials. Fifty-one percent of the Findings Reports that did not involve credential compromises identified malware compromises. The top malware families identified were ursnif, Emotet, Cryxos, Trickbot, and Rontobro. Percentages in the table below are the fraction of incidents involving malware.
It should be noted that we typically exclude data breach disclosure-related alerts in our quarterly Threat Report, however we've observed increased targeting of user accounts as a result of the rapid shift to remote work for most organizations.
| Malware Family | % of Incidents |
| ursnif | 25.0% |
| Emotet | 15.0% |
| Cryxos | 7.9% |
| TrickBot | 6.4% |
| Rontobro | 2.1% |
We've observed increased targeting of user accounts as a result of the rapid shift to remote work for most organizations.
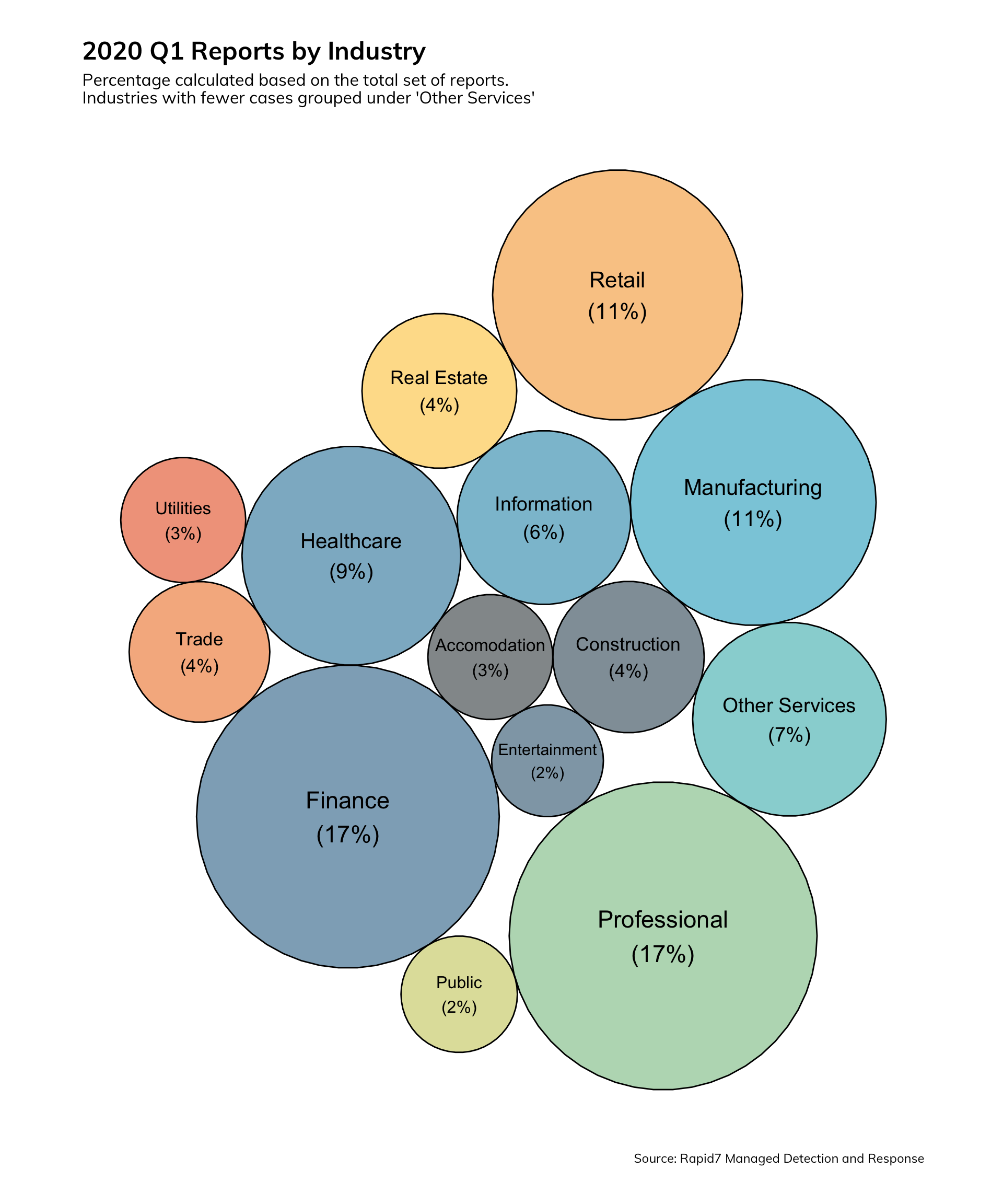
We continue to see the Financial, Professional, Manufacturing, and Retail sectors as the favored targets due to the lure of money and access to data. The Healthcare sector is, unfortunately, an obvious target moving up in Q1.
There were 17 breaches that required incident response for MDR customers:
- Three are classified as HIGH severity and impact.
- Seven are classified as MODERATE severity and impact.
- Six are classified as LOW severity and impact.
- One was a pentester.
- Nine were as a result of exploited externally facing vulnerabilities.
- Two were cloud-based business email compromises resulting in data exfiltration.
- Two lead to domain controller compromises.
- One resulted in ransomware.
- Four were malware with no impact outside of the infection.
- All but two of these Q1 investigations involved hands-on-keyboard attackers as opposed to unattended, automated attacks.
It is relatively unusual for us to see such a high number of incidents resulting from public-facing vulnerabilities.
This is not normal; it is relatively unusual for us to see such a high number of incidents resulting from public-facing vulnerabilities. We're attributing this occurrence to the severity and potential impact of some of the vulnerabilities from Q1. Nonetheless, this highlights the importance of ensuring that critical patches can be evaluated and deployed quickly, especially when it involves critical systems and infrastructure.
Threats to the User and the Impact to Credentials
To begin our focus on the threats to the user and the impact to credentials with a bang: a whopping 96% of all MDR incidents involve stolen credentials. The industries most impacted by stolen credentials are Finance (19%), Professional (17%), and Healthcare (9%). One oft-forgotten aspect of attack surface management is monitoring the criminal digital marketplace for indications that data either belongs to your organization or is describing your organization. Rapid7's MDR offers this service to our customers in the form of monitoring for stolen user credentials. In the first quarter, accounts associated with the MyHeritage.com compromise resulted in notifications to 80 organizations for a total of 286 compromised user accounts.
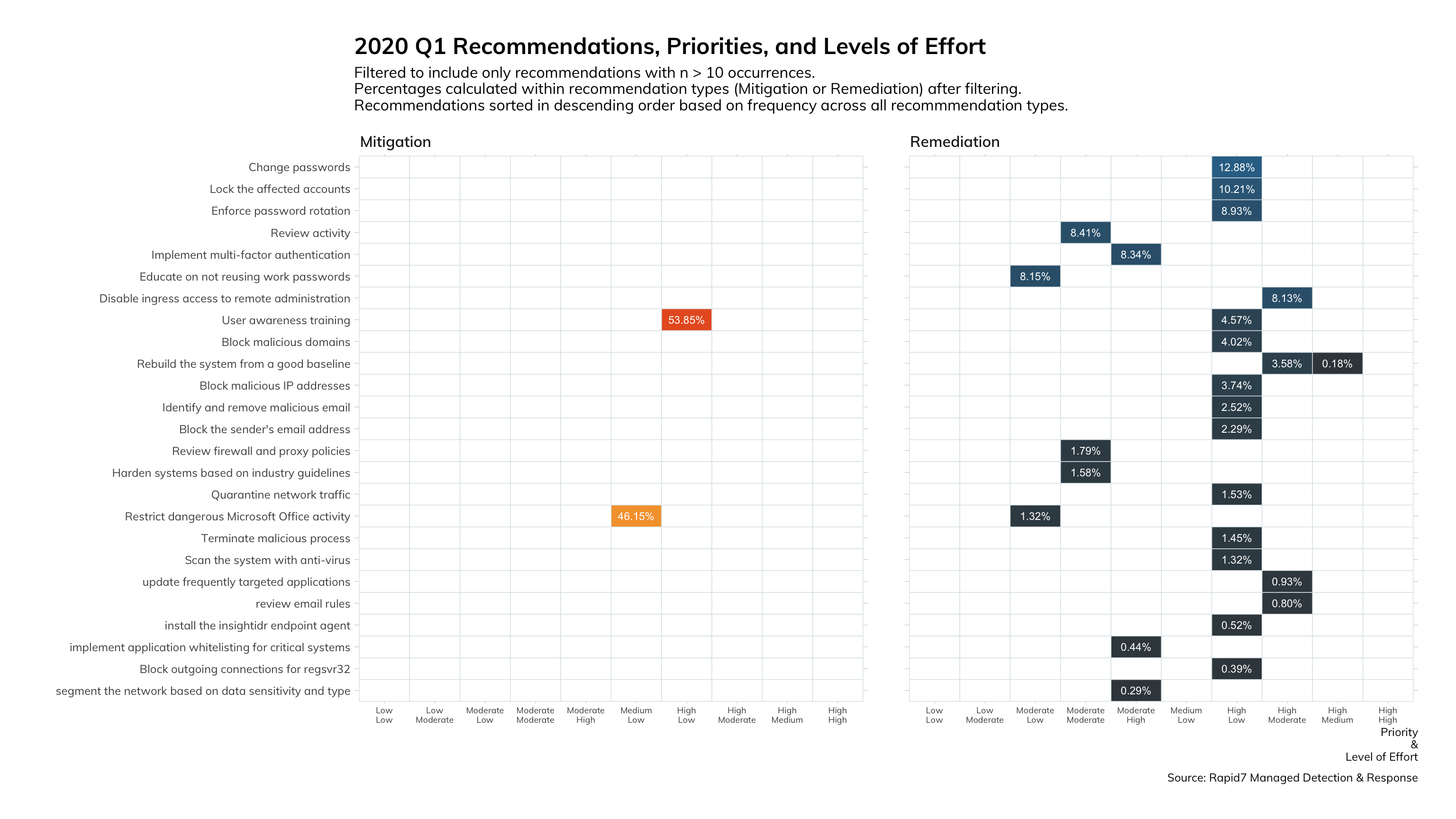
Now, the risk associated with business credential disclosure in non-business related data breach disclosures is easily mitigated with multi-factor authentication (MFA). However, the reason we decided to surface this data in our quarterly Threat Report is to highlight the magnitude of the issue to justify some additional investment in user education. Most security training we’ve attended does cover appropriate use of business credentials and prohibits password reuse. Anecdotally, we know a pretty sizable proportion of business users are, in fact, breaking the no-reuse rule. This data proves out these anecdotes. I have always been an advocate of helping users understand the value of the data they have (and have access to) in the eyes of the attacker. As meaningless as the business credential is, why would we want to give data away without a fight? To further reinforce the need for user education, the following graphic shows that in 53% of cases, Rapid7’s MDR team recommends user education as an effective prevention against a host of threats.
Honing in on spear-phishing and excluding the data from data breach disclosures, we observed 49 successful lure attempts. Amongst those, 41% contained links impersonating cloud and enterprise authentication pages intended to steal valid credentials. The most targeted industries include Finance (22%), Retail (14%), and Manufacturing (10%). As far as impact, 53% resulted in compromised credentials, 30% involved malware, 16% resulted in system level compromise, and two involved exploit kits.
With our partners at the Cyber Threat Alliance, we have tracked several campaigns across our combined data set exploiting fears over COVID-19 and how society and business have responded.
With the shift of the modern enterprise away from traditional business applications to embrace SaaS, we also see the shift in motivation behind spear-phishing attempts. Further, with our partners at the Cyber Threat Alliance, we have tracked several campaigns across our combined data set exploiting fears over COVID-19 and how society and business have responded. In February, we saw a campaign spreading the HEUR.ADVMLC.C malware using several deception techniques, including claiming a cure for COVID-19, impersonating World Health Organization official communications, impersonating official government relief and stimulus communications, and impersonating workplace survey and business continuity communications. In March we observed a COVID-19 themed Trickbot malware campaign targeting Italy and focused on the Italian government response.
As we've observed in past significant events, attackers are unscrupulous when it comes to the lows they will sink to to incite users to fall victim to their lures. Further, the simplicity with which lures can appear and disappear makes actively defending against them impossible. While we shouldn't give up on our technical means of countering spear-phishing, user education and expectation setting around business communications are our most effective tools.
To further illustrate how quickly and ravenously attackers sought to leverage COVID-19 related lures, the following chart illustrates the COVID-19 themed domain registrations for the first fourth months of 2020, coinciding with the time that Europe, then the United States, became epicenters of the global pandemic.
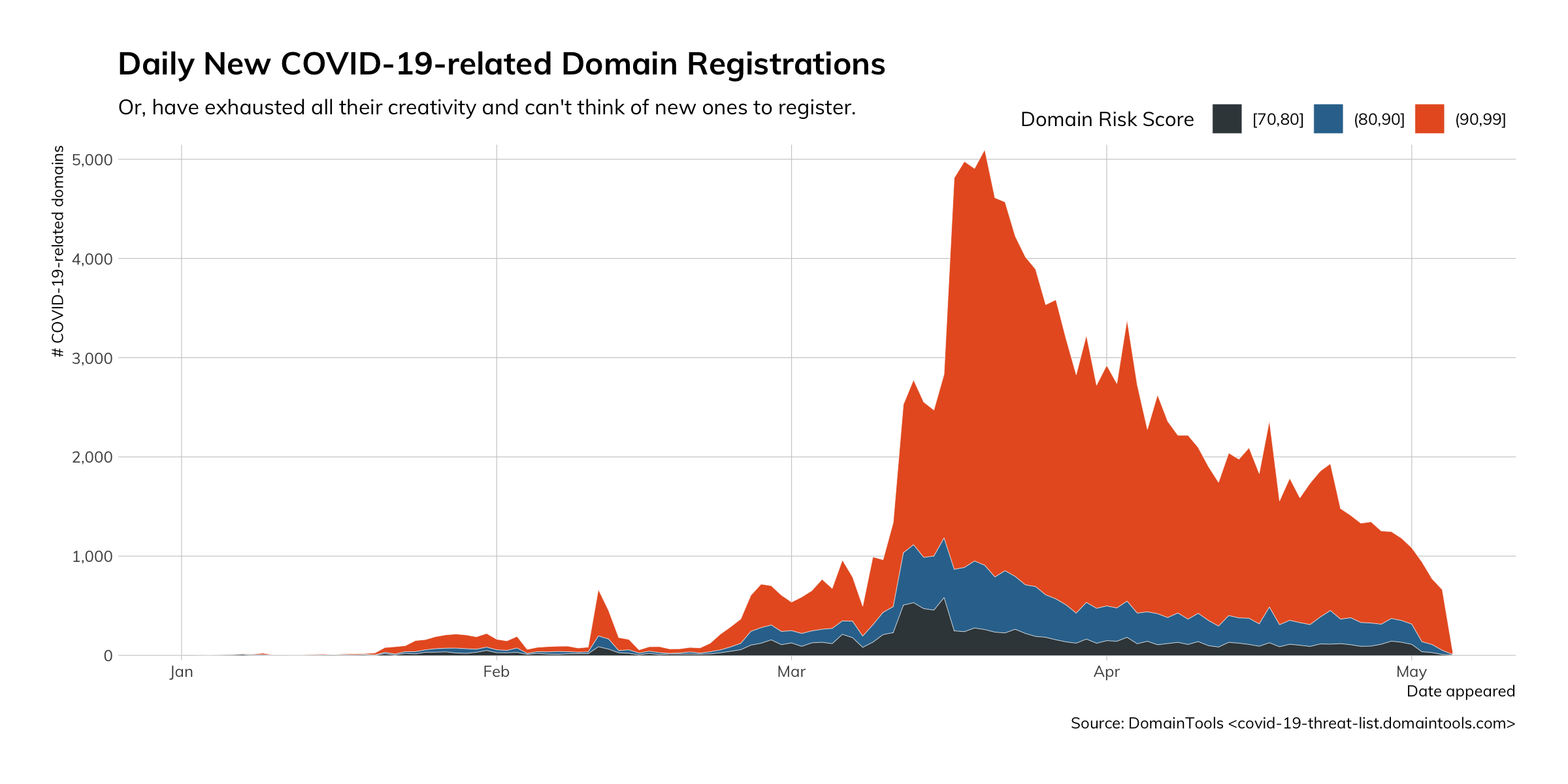
Tactically, the Threat Intelligence Coalition has offered a free threat indicator feed for COVID-19 related threats that we recommend all organizations implement into their threat detection technology.
Threats to the Endpoint
Shifting our focus to the impact to the endpoint, there were 98 MDR Findings Reports identifying the presence of malware. Of those, 45% were attributed to known indicators of compromise (IoCs). Fourteen percent attributed the initial access vector as phishing. Thirteen percent were multi-stage droppers capable of loading different malware families. Two involved exploit kits.
To better understand the implications, the MDR SOC typically detects threats that network and endpoint threat prevention technology has missed (or threat prevention technology didn't have visibility). Even with the prevention layer, 45% of known threats are still getting through. Worse, 55% of malware threats do not match known threat indicators. This unknown threat metric speaks to the need for multiple methodologies for detecting threats.
Within the unknown malware data set, we found that the top three MITRE ATT&CK™ techniques include Masquerading (24%), PowerShell/Scripting (22%), and User Execution (14%). To explore this data, we focused on the detections that were effective in identifying these threats. We found three main categories of detections:
- PowerShell: matching powershell.exe command line options against known attacker techniques, such as hidden window execution, concatenation of strings, and character obfuscation.
- Scripting (other than PowerShell): evaluating child processes of known script interpreters, scripting interpreters running files from within an archive, scripting interpreters reading from HKCU registry keys.
- Attacker commands: determining IP address via command line, RegSvr32 usage via command line, control.exe usage via command line, DNS/IP configuration lookup output to file via command line, Scheduled Tasks via command line, and cmstp.exe via command line.
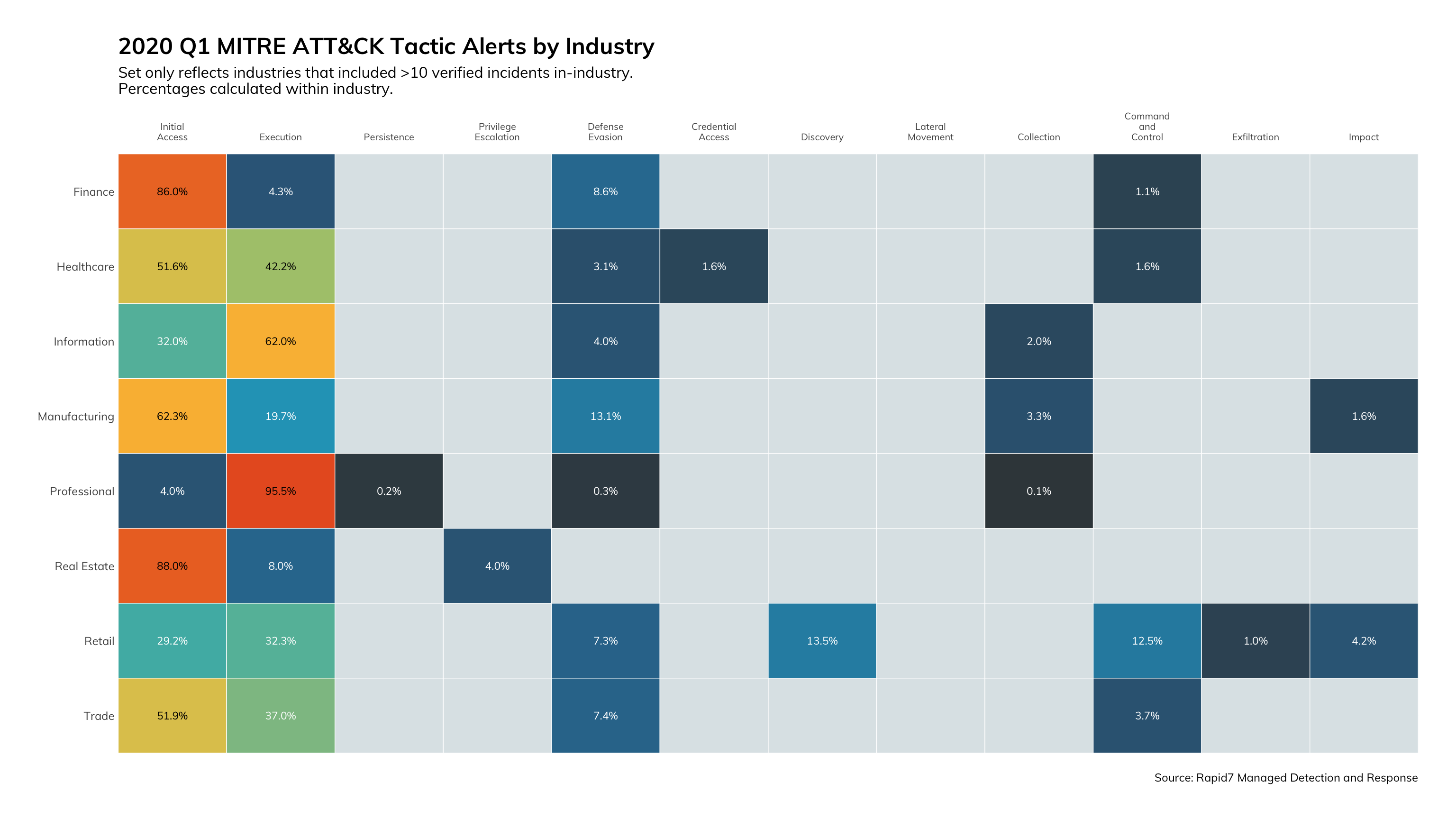
Taking a step back and focusing on the MITRE ATT&CK classification, we're seeing a slight shift of the detections to the left in "Initial Access" and "Execution". The Finance, Professional, and Real Estate industries are detecting over 90% of their breaches within the first two phases of the attack lifecycle. That's pretty good!
In closing, there haven't really been any significant shifts in the threat landscape other than attackers opportunistically using COVID-19 related lures, and even those are starting to drop off, since major email handlers like Google Apps and Microsoft 365 have gotten pretty great at telling the difference between legitimate COVID-19 communications and spam or malicious messages.
Key Takeaways
- We have observed an increase in the targeting of user accounts and the disclosure of business credentials leaked as a result of third-party notifications. In response, we recommend that organizations prioritize investments in multi-factor authentication for access to internal networks, cloud-based services, sensitive business applications, and sensitive data stores. Further, we believe that end user education needs to change. Annual compliance training isn’t getting it done. Aggressive spear-phishing testing isn’t getting it done. Zoom-bombing other team meetings with horribly crafted, poorly acted zombie-apocalypse anti-phishing skits isn’t getting it done. In addition to your core values, guiding principles, mottos, and beliefs, your culture must promote the constant vigilance to guard yourselves, customers, and partners from damaging data disclosures. This includes keeping business and non-business hardware, credentials, and data for separate purposes.
- Rapid7’s MDR and IR teams investigated nine breaches that occurred as a result of public-facing vulnerabilities in critical assets—that’s much higher than prior quarters. While this increase is largely attributable to the severity and impact of the vulnerabilities in the first quarter of 2020, this does serve to highlight the importance of having a vulnerability management program that defines change control exceptions and strict SLAs for patching severe vulnerabilities in public-facing assets.
- Rapid7 and our partners at the Cyber Threat Alliance have seen a number of spear-phishing campaigns aimed at exploiting the fears surrounding COVID-19 and impersonating various official government and business communications. While not specific to COVID-19 or the current environment, we know that attackers often theme their lures around significant events. This highlights the need for security teams to proactively monitor the threat landscape and routinely inform organizations on how attackers are targeting their victims. Further, organizations should establish several defined processes and vehicles for communicating critical business continuity and enterprise-wide communications so that colleagues can quickly identify true business communications from sophisticated, filter-evading lures.
- Only 45% of malware threats reported by Rapid7’s MDR are detectable using traditional antivirus software. Several additional layers including next-gen AV, User Behavior Analytics (UBA), Attacker Behavior Analytics (ABA), and process behavior analytics are required to detect the breadth of threats to the endpoint.
Focus on Recommendations
There have not been any significant shifts in the remediation and mitigation statistics from the MDR reports, however we did want to bring back this image from the 2020 Threat Report to reinforce the importance of effective and rapid threat response. If your teams are not ready to quickly perform the remediation tasks in Figure 7, then the breach’s impact to the organization is sure to increase.
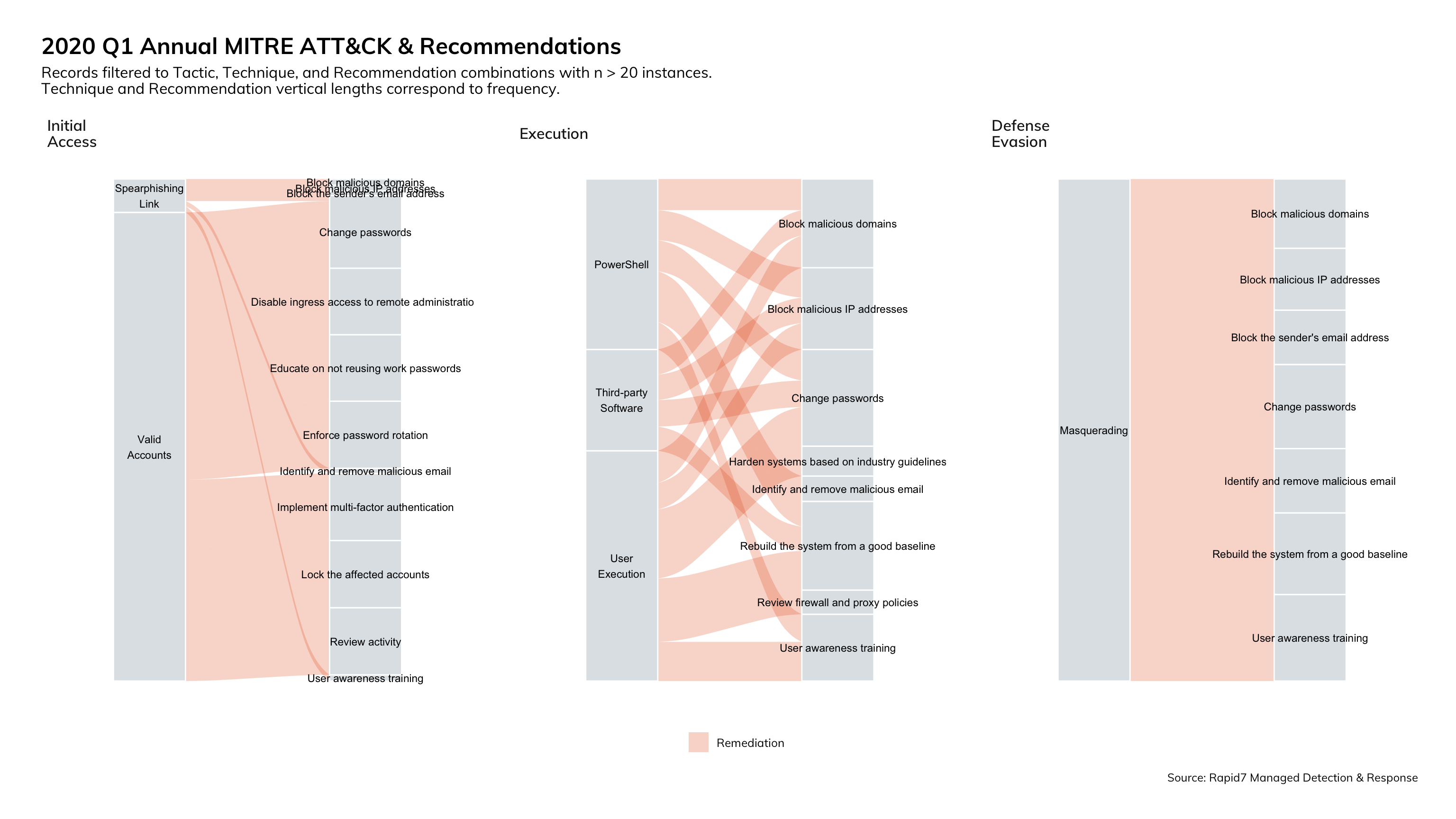
In keeping with the theme of focusing on remote workers’ business impact, this quarter we explore attack surface management and detection and response recommendations for the endpoint that lives outside the traditional enterprise IT environment.
First, let’s review some of the expert opinions from the Rapid7 blog starting with enterprise considerations when expanding remote workforce capacity. In his post, Darragh Delaney explores the challenges and pitfalls associated with hasty network configuration changes and how to maintain visibility. External footprint monitoring and analysis, network change control and validation, SIEM/logs, and Network Traffic Analysis are key capabilities and telemetry that security teams need to deploy defenses against threats.
While not threat-specific, we know that many organizations and security teams will be impacted by the economic recession associated with worldwide physical distancing efforts. In his post, Scott King covers several areas for security leadership to focus short- and medium-term efforts to strengthen the organizational security posture and resilience to change. He also offers guidance on security awareness and enterprise security communications to help educate users on their part in protecting customers, partners, and co-workers.
Additionally, Tod Beardsley offers guidance for your co-workers to secure their home Wi-Fi environments, including changing default passwords, effective encryption, and how to handle IoT devices on your network. With the work from home orders being extended in many locations, security programs must evolve their education program to account for new work habits.
Taking a step back to look at the trends we’ve observed here, a few themes emerge that are worthy of investment:
Measuring the effectiveness of your vulnerability management program
- Instead of another blanket recommendation to PATCH, PATCH, PATCH! We’re going to recommend you measure how long it takes to patch high and critical vulnerabilities on internet-facing assets. If it is less than 24 hours to begin the rollout, set that as a measured goal reported to the executive team.
Level up asset and identity management, data classification, authentication, and authorization
- In many cases, you already have the tools at your disposal to better understand where your critical data resides (data classification and asset management), who has access to it (authorization), and how they access it (asset management and authentication). This investment allows you to maximize your existing investments and better align future investments to best protect critical data.
Endpoint security and configuration management is now a hard requirement for any security program
- Endpoint agents are no longer optional in security programs. The workforce, workplace, and enterprise technology ecosystem is completely decentralized. Security programs must be able to reach into any endpoint at any time to be effective against threats. Endpoint agents should have EDR capabilities recording key system events, real-time investigative data acquisition, next-gen AV terminating threats based on behaviors, active threat prevention, and on-demand mitigation and remediation capabilities.
End user education must change
- End user education must be in your security program’s top three areas of investment—or, ideally, top one. The dollar cost of end user security education is tiny in comparison to the cost of technology, headcount, and the costs associated with a breach. Yet almost every security program (and therefore its employees) we’ve observed treats education as a begrudged checkbox. Checkbox education means checkbox decision-making when there's a real threat.
Checkbox education means checkbox decision-making when there's a real threat.
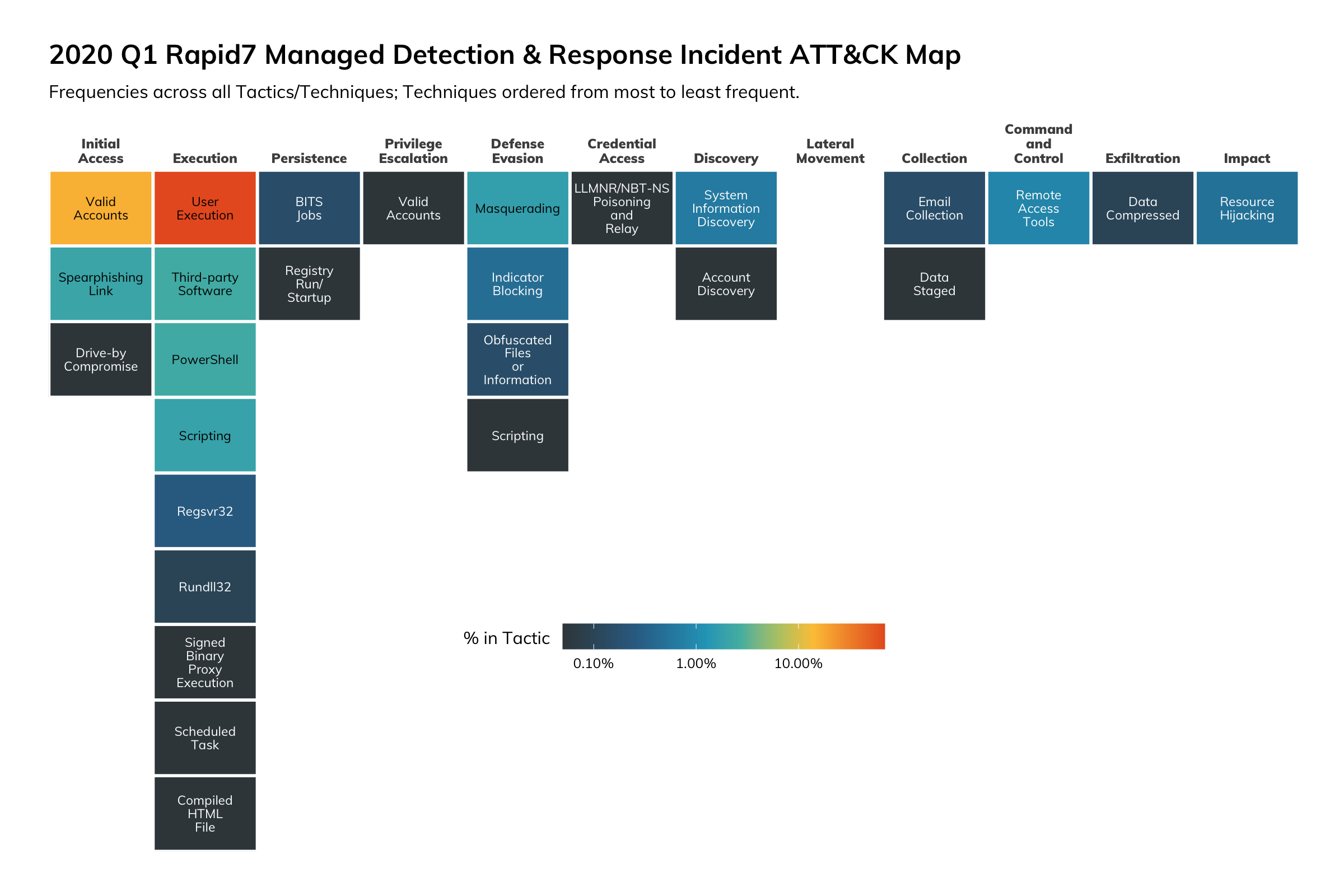
Appendix ATT&CK
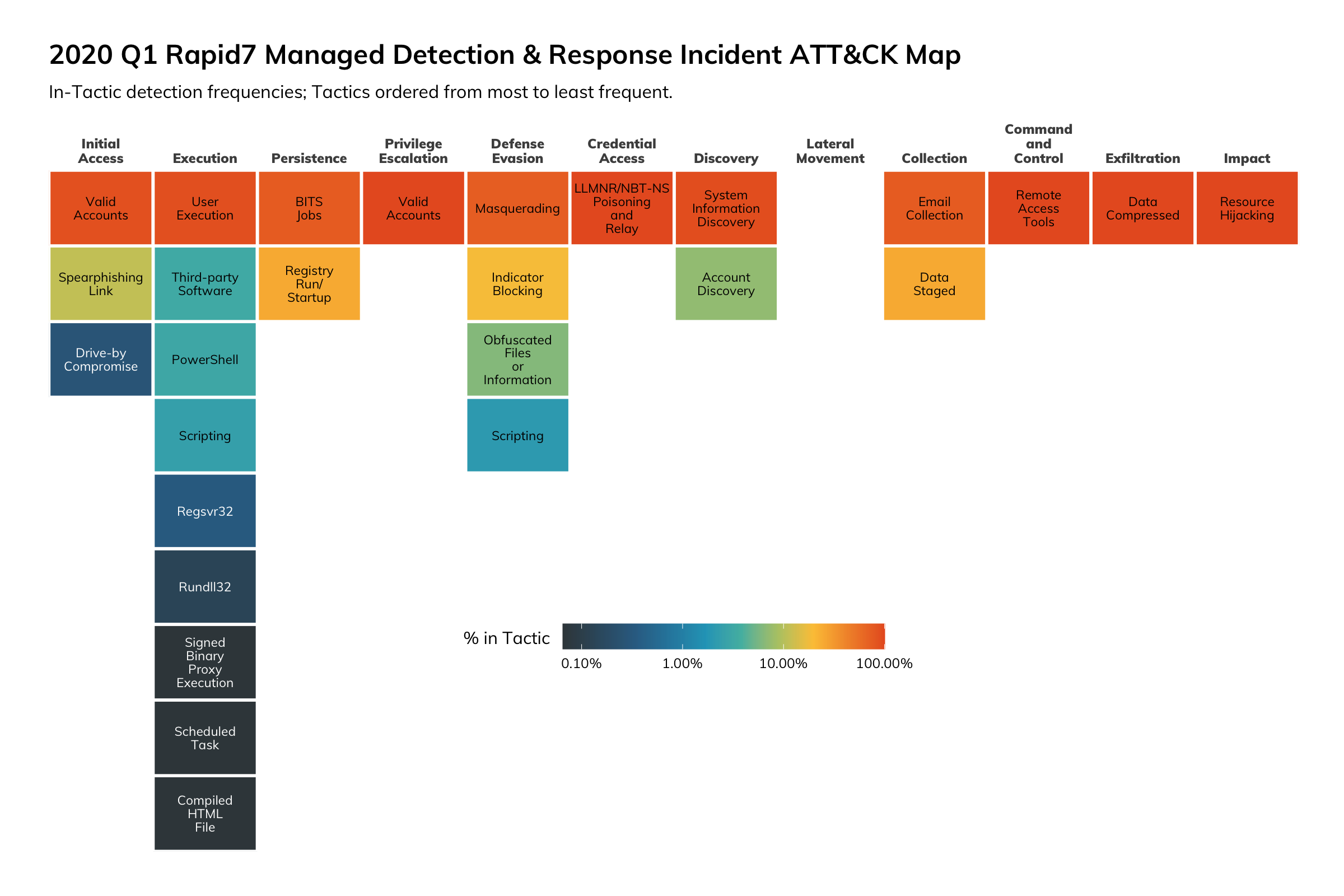
To help other organizations compare Rapid7’s 2020 Q1 incident corpus with their own incidents or other vendor reports, the complete incident MITRE ATT&CK map is presented below, showing in-Tactic frequency of detections, with tactics ordered by most frequent to least frequent, followed by the same ATT&CK map with overall frequencies.
Reach out to research@rapid7.com for more information on our ATT&CK mappings.
About Rapid7
Rapid7 (Nasdaq: RPD) is advancing security with visibility, analytics, and automation delivered through our Insight cloud. Our solutions simplify the complex, allowing security teams to work more effectively with IT and development to reduce vulnerabilities, monitor for malicious behavior, investigate and shut down attacks, and automate routine tasks. Customers around the globe rely on Rapid7 technology, services, and research to improve security outcomes and securely advance their organizations.