Even when offensive security techniques have been publicly discussed at conferences and proof of concept code or open source tools are available, using them in your projects can be very time consuming and may even require custom development. Metasploit Pro 4.7 now introduces MetaModules, a unique new way to simplify and operationalize security testing for IT security professionals.
MetaModules automate common yet complicated security tests that provide under-resourced security departments a more efficient way to get the job done. The current release includes six MetaModules for security controls testing and penetration testing, which supply common functionality such as validating which outbound firewall ports are open, testing for default credentials or stealthily discovering hosts on the network.
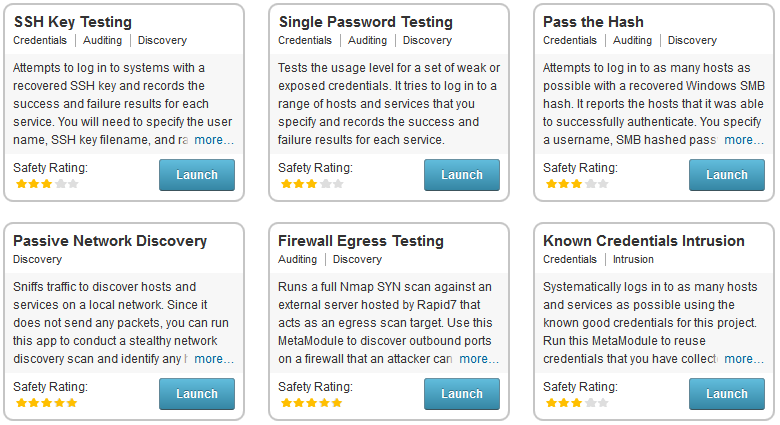
Here's an overview of the new MetaModules:
- Firewall Egress Testing: Validate which outbound firewall ports are open to audit your firewall egress. This MetaModule contacts a Rapid7-hosted server to test open ports and delivers the results in one easy report.
- Passive Network Discovery: Stealthily discover hosts and services on the network without sending a single packet. Some penetration tests place value on breaching the network without triggering alarms. This MetaModule sniffs the network traffic and maps out hosts and services as a first step in a network - without risking the chance of detection. All data is automatically available in the Metasploit Pro project so you can plan your attack.
- Single Credentials Testing: These three MetaModules can help you test where certain passwords, hashes, or SSH keys can be used. In enterprise IT environments, you can test, for example, whether development credentials are mistakenly used on production systems. As part of a penetration test, you can try out credentials on thousands of hosts at a time without using a payload to reduce the likelihood of detection. These MetaModules attempt to log on to several service types and reports the results. There are three MetaModules in this category: Single Password Testing consumes user/password combinations; Pass the Hash consumes password hashes; and SSH Key Testing validates which systems a particular SSH private key grants access to.
- Known Credentials Intrusion: Compromise machines on the network using verified credentials. After having determined which credential works on which machine, use this easy MetaModule to compromise a machine and create a session.
MetaModules are based on a unique architecture that will enable development of more packaged security testing. MetaModules are another example of Rapid7's commitment to operationalizing security controls testing, the best practice of verifying that your defensive solutions are effective in keeping attackers out.
While the new MetaModules are exclusive to the Metasploit Pro Edition, Rapid7 continues to deliver regular updates to Metasploit Framework, such as new exploits and other modules, as they become available.
We will be hosting a Metasploit 4.7 webcast on Tuesday, July 23 at 2pm ET that will discuss MetaModules in detail and show you how to use them.
New Modules since 4.6.0
Of course, the Metasploit exploit development community has been chugging along since 4.6.0 was released, so we've got a ton of new vulnerability content in this release as well, which are available in both the commercial and free editions. From the recent IPMI modules, to the SAP scanners, to the embedded device exploits for pretty much every home access point manufacturer, we've got more than enough to keep you busy on your next penetration testing engagement. Below is the list of the 91 new modules in all; 54 exploits, 34 auxiliary modules, and 3 post modules, all new since Metasploit 4.6.0.
Exploits
- FreeBSD 9 Address Space Manipulation Privilege Escalation by sinn3r, Alan Cox, Hunger, and Konstantin Belousov exploits CVE-2013-2171
- DLink DIR-645 / DIR-815 diagnostic.php Command Execution by juan vazquez and Michael Messner exploits OSVDB-92144
- D-Link DIR615h OS Command Injection by juan vazquez and Michael Messner exploits OSVDB-90174
- GroundWork monarch_scan.cgi OS Command Injection by juan vazquez and Johannes Greil exploits CVE-2013-3502
- Linksys WRT160nv2 apply.cgi Remote Command Injection by juan vazquez and Michael Messner
- Linksys WRT54GL apply.cgi Command Execution by juan vazquez and Michael Messner
- Mutiny 5 Arbitrary File Upload by juan vazquez exploits CVE-2013-0136
- Netgear DGN2200B pppoe.cgi Remote Command Execution by juan vazquez and Michael Messner exploits OSVDB-90320
- Nginx HTTP Server 1.3.9-1.4.0 Chunked Encoding Stack Buffer Overflow by Greg MacManus, hal, and saelo exploits CVE-2013-2028
- HP System Management Homepage Local Privilege Escalation by agix exploits OSVDB-91990
- Kloxo Local Privilege Escalation by juan vazquez and HTP exploits OSVDB-93287
- ZPanel zsudo Local Privilege Escalation Exploit by sinn3r and juan vazquez
- Nagios Remote Plugin Executor Arbitrary Command Execution by Rudolph Pereir and jwpari exploits CVE-2013-1362
- Exim and Dovecot Insecure Configuration Command Injection by juan vazquez, Unknown, and eKKiM exploits OSVDB-93004
- MiniUPnPd 1.0 Stack Buffer Overflow Remote Code Execution by hdm and Dejan Lukan exploits CVE-2013-0230
- Firefox 17.0.1 Flash Privileged Code Injection by sinn3r, Marius Mlynski, and joev exploits CVE-2013-0757
- Java Applet Driver Manager Privileged toString() Remote Code Execution by juan vazquez and James Forshaw exploits ZDI-13-076
- Java Applet ProviderSkeleton Insecure Invoke Method by Adam Gowdiak and Matthias Kaiser exploits CVE-2013-2460
- Java Applet Reflection Type Confusion Remote Code Execution by juan vazquez and Jeroen Frijters exploits CVE-2013-2423
- phpMyAdmin Authenticated Remote Code Execution via preg_replace() by Ben Campbell and Janek "waraxe" Vind exploits CVE-2013-3238
- Apache Struts includeParams Remote Code Execution by Douglas Rodrigues, Eric Kobrin, and Richard Hicks exploits CVE-2013-1966
- SAP Management Console OSExecute Payload Execution by juan vazquez and Chris John Riley
- SAP SOAP RFC SXPG_CALL_SYSTEM Remote Command Execution by nmonkee exploits OSVDB-93537
- SAP SOAP RFC SXPG_COMMAND_EXECUTE Remote Command Execution by nmonkee
- SSH User Code Execution by Brandon Knight and Spencer McIntyre exploits CVE-1999-0502
- Carberp Web Panel C2 Backdoor Remote PHP Code Execution by Steven K, bwall(Brian Wallace), and connection(Luis Santana)
- Havalite CMS Arbitary File Upload Vulnerability by sinn3r and CWH exploits OSVDB-94405
- InstantCMS 1.6 Remote PHP Code Execution by juan vazquez, AkaStep, and Ricardo Jorge Borges de Almeida exploits BID-60816
- LibrettoCMS File Manager Arbitary File Upload Vulnerability by sinn3r and CWH exploits OSVDB-94391
- >MoinMoin twikidraw Action Traversal File Upload by juan vazquez, HTP, and Unknown exploits CVE-2012-6081
- >Wordpress W3 Total Cache PHP Code Execution by juan vazquez, hdm, Christian Mehlmauer, and Unknown exploits CVE-2013-2010
- ZPanel 10.0.0.2 htpasswd Module Username Command Execution by sinn3r and shachibista exploits OSVDB-94038
- IBM SPSS SamplePower C1Tab ActiveX Heap Overflow by juan vazquez and Alexander Gavrun exploits ZDI-13-100
- MS13-038 Microsoft Internet Explorer CGenericElement Object Use-After-Free Vulnerability by sinn3r, juan vazquez, EMH, and Unknown exploits MS13-038
- Sun Java Web Start Double Quote Injection by Rh0 exploits CVE-2012-1533
- MS13-037 Microsoft Internet Explorer COALineDashStyleArray Integer Overflow by juan vazquez, 4B5F5F4B, and Nicolas Joly exploits MS13-037
- Oracle WebCenter Content CheckOutAndOpen.dll ActiveX Remote Code Execution by juan vazquez and rgod exploits ZDI-13-094
- Synactis PDF In-The-Box ConnectToSynactic Stack Buffer Overflow by sinn3r and h1ch4m exploits OSVDB-93754
- ABBS Audio Media Player .LST Buffer Overflow by Julian Ahrens and modpr0be exploits OSVDB-75096
- AudioCoder .M3U Buffer Overflow by juan vazquez and metacom exploits OSVDB-92939
- Corel PDF Fusion Stack Buffer Overflow by juan vazquez and Kaveh Ghaemmaghami exploits CVE-2013-3248
- ERS Viewer 2011 ERS File Handling Buffer Overflow by juan vazquez and Parvez Anwar exploits CVE-2013-0726
- ERS Viewer 2013 ERS File Handling Buffer Overflow by juan vazquez and James Fitts exploits CVE-2013-3482
- >MediaCoder .M3U Buffer Overflow by metacom, modpr0be, and otoy exploits OSVDB-94522
- Free Float FTP Server USER Command Buffer Overflow by D35m0nd142 and Doug Prostko exploits OSVDB-69621
- HP System Management Homepage JustGetSNMPQueue Command Injection by sinn3r and Markus Wulftange exploits CVE-2013-3576
- Novell Zenworks Mobile Managment MDM.php Local File Inclusion Vulnerability by Andrea Micalizzi (aka rgod) and steponequit exploits ZDI-13-087
- SAP ConfigServlet Remote Code Execution by Andras Kabai and Dmitry Chastuhin exploits OSVDB-92704
- AdobeCollabSync Buffer Overflow Adobe Reader X Sandbox Bypass by juan vazquez and Felipe Andres Manzano exploits CVE-2013-2730
- Novell Client 2 SP3 nicm.sys Local Privilege Escalation by juan vazquez and Unknown exploits OSVDB-93718
- Novell Client 4.91 SP4 nwfs.sys Local Privilege Escalation by juan vazquez and Ruben Santamarta exploits OSVDB-46578
- Windows EPATHOBJ::pprFlattenRec Local Privilege Escalation by sinn3r, juan vazquez, egyp7, Keebie4e, Meatballs, Tavis Ormandy, and progmboy exploits CVE-2013-3660
- Lianja SQL 1.0.0RC5.1 db_netserver Stack Buffer Overflow by Spencer McIntyre exploits CVE-2013-3563
- Microsoft Windows Authenticated Powershell Command Execution by RageLtMan and Royce @R3dy__ Davis exploits CVE-1999-0504
Auxiliary
- DLink DSL 320B Password Extractor by Michael Messner exploits OSVDB-93013
- Mutiny 5 Arbitrary File Read and Delete by juan vazquez exploits CVE-2013-0136
- SAP ConfigServlet OS Command Execution by Andras Kabai and Dmitry Chastuhin exploits OSVDB-92704
- Canon Wireless Printer Denial Of Service by Matt "hostess" Andreko exploits CVE-2013-4615
- Monkey HTTPD Header Parsing Denial of Service (DoS) by Doug Prostko exploits CVE-2013-3843
- Memcached Remote Denial of Service by Gregory Man exploits CVE-2011-4971
- SAP SOAP EPS_DELETE_FILE File Deletion by Alexey Sintsov and nmonkee exploits OSVDB-74780
- >MiniUPnPd 1.4 Denial of Service (DoS) Exploit by hdm and Dejan Lukan exploits CVE-2013-0229
- Sysax Multi-Server 6.10 SSHD Key Exchange Denial of Service by Matt "hostess" Andreko exploits OSVDB-92081
- Apache Rave Users Information Disclosure by juan vazquez and Andreas Guth exploits CVE-2013-1814
- Apple Safari .webarchive File Format UXSS by joev
- ColdFusion 'password.properties' Hash Extraction by sinn3r, HTP, and nebulus exploits OSVDB-93114
- CouchDB Enum Utility by espreto
- CouchDB Login Utility by espreto
- Canon Printer Wireless Configuration Disclosure by Matt "hostess" Andreko exploits CVE-2013-4614
- HP Intelligent Management FaultDownloadServlet Directory Traversal by juan vazquez and rgod exploits ZDI-13-051
- HP Intelligent Management IctDownloadServlet Directory Traversal by juan vazquez and rgod exploits ZDI-13-053
- HP Intelligent Management ReportImgServlt Directory Traversal by juan vazquez and rgod exploits ZDI-13-052
- HP System Management Homepage Login Utility by sinn3r
- InfoVista VistaPortal Application Bruteforce Login Utility by Karn Ganeshen
- >MediaWiki SVG XML Entity Expansion Remote File Access by juan vazquez, Christian Mehlmauer, and Daniel Franke exploits OSVDB-92490
- Novell Zenworks Mobile Device Managment Admin Credentials by Andrea Micalizzi (aka rgod) and steponequit exploits CVE-2013-1081
- RFCode Reader Web Interface Login / Bruteforce Utility by Karn Ganeshen
- SevOne Network Performance Management Application Brute Force Login Utility by Karn Ganeshen
- IPMI 2.0 RAKP Cipher Zero Authentication Bypass Scanner by hdm and Dan Farmer exploits OSVDB-93040
- IPMI 2.0 RAKP Remote SHA1 Password Hash Retreival by hdm and Dan Farmer
- IPMI Information Discovery by hdm and Dan Farmer
- SAP CTC Service Verb Tampering User Management by Alexandr Polyakov and nmonkee
- SAPRouter Port Scanner by Bruno Morisson and nmonkee
- SAP SOAP RFC EPS_GET_DIRECTORY_LISTING Directories Information Disclosure by nmonkee
- SAP SOAP RFC PFL_CHECK_OS_FILE_EXISTENCE File Existence Check by lexey Tyurin and nmonkee exploits OSVDB-78537
- SAP SOAP RFC RZL_READ_DIR_LOCAL Directory Contents Listing by Alexey Tyurin and nmonkee exploits OSVDB-92732
- SMTP Open Relay Detection by Campbell Murray
Post
- Windows Gather Deleted Files Enumeration and Recovering by Borja Merino
- Windows Manage Trojanize Support Account by salcho
- Windows Manage Remote Point-to-Point Tunneling Protocol by Borja Merino
Availability
If you're new to Metasploit, you can get started by downloading Metasploit for Linux or Windows. If you're already tracking the bleeding-edge of Metasploit development, then these modules are but an msfupdate command away. For readers who prefer the packaged updates for Metasploit Community and Metasploit Pro, you'll be able to install the new hotness today when you check for updates through the Software Updates menu under Administration.
For additional details on what's changed and what's current, please see Brandont's most excellent release notes.