This 3-part series explores the critical role logs play in maintaining regulatory compliances and provides specific examples of known events to look for an how to evaluate different compliance tools.

When it comes to PCI Compliance, simply collecting and storing your logs isn’t enough. PCI DSS Compliance requires to someone regularly reviews the logs for known events that could be indicators of compromise. One such event is changes to account privileges.
Changes to account privileges, especially when made by the user whose permissions are being elevated, could be an indication that a user’s credentials have been compromised. Since identifying compromised credentials can be particularly difficult, logging, alerting on and reviewing these changes is critical to maintaining PCI compliance.
Below is an excerpt from our latest white paper that explores guidelines for securely retaining log data.
Privileged Account Activity
An event type that is of particular interest across all compliance standards is actions taken by a user with elevated privileges on a protected system. The example below is of an event for a session on a system in which a uniquely identified user with normal access logged in and elevated their privileges to root.
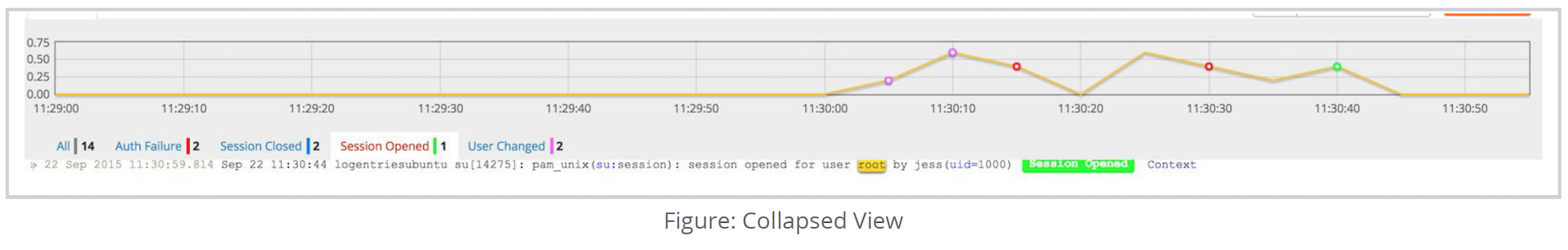
On first glance this looks like normal behavior. Upon expanding the context of the entry, however, it can be seen that there were more interesting actions taken prior to the privilege escalation. There are a series of remote authentication failures, followed by an eventual success. From there, the user was able to immediately and successfully elevate their privileges and open a session as root.
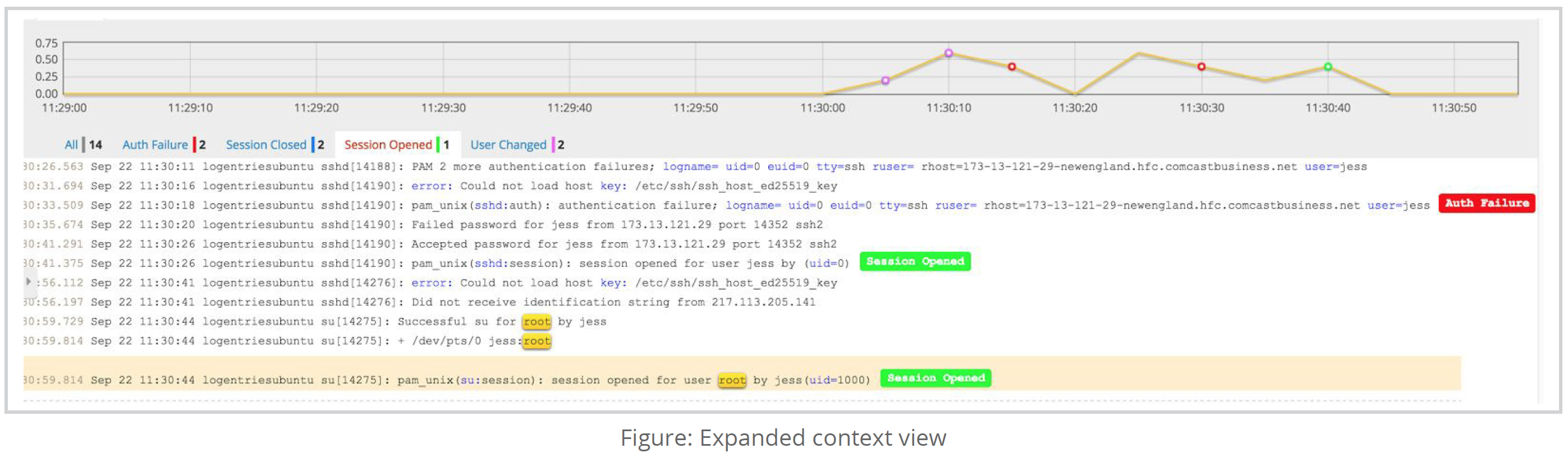
While this might be an innocent case of a user entering in the incorrect password a few times, it could also be evidence of a malicious outsider gaining access and compromising the system. This level of comprehensive visibility allows for a better understanding of a chain of events.
Taking this event into consideration, another log analysis technique is to look at failed authentication in general. This provides a view of which user accounts are misconfigured or are potentially subject to brute force attacks. One way to do this is by querying for invalid users that have failed logon.
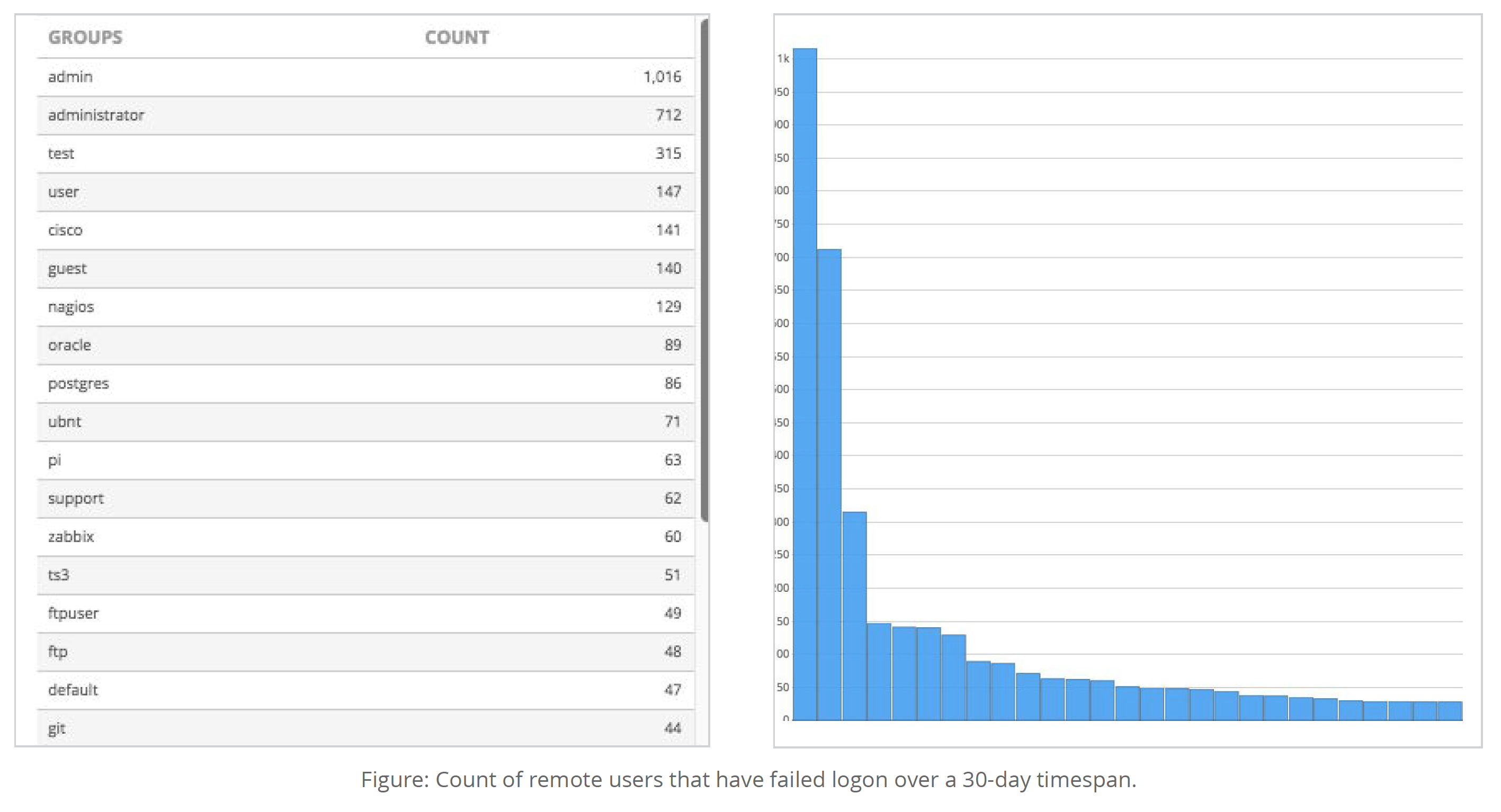
This information shows that the username “admin” and “administrator” have the most failed login attempts. If this volume of failed logins for any accounts are significantly higher than expected, it could indicate a misconfiguration or attack.