You have the tools to detect and notify your team about security threats. You’ve hired the best security practitioners who know what an effective security posture looks like. You’re all set to stop attackers from compromising your systems.
Just one more thing: How can you maximize the value of these resources, especially in the face of complex threats and a huge volume of alerts?
While processes can go a long way in harmonizing your tools and personnel to accelerate tedious tasks such as alert investigations, connecting your tools and automating security processes can save up to 83 percent of the time spent manually fetching data and other triage and incident response tasks.
Let’s take a look at the traditional alert investigation process and how to layer on automation for speed, efficiency, and accuracy in modern-day security operations.
Manual Investigation Processes Are Broken
You’re likely no stranger to tedious manual investigatory tasks. So you know that dealing with alerts takes up a ton of time and much of that time is wasted on false positives. In fact, organizations surveyed by Ponemon said they receive an average of 17,000 malware alerts per week. Of these, only 19 percent are considered reliable (i.e. real) alerts, but even then, only four percent are actually investigated. The average cost of time wasted on these alerts? $1.27 million annually.
Security teams use a variety of systems and tools to detect, investigate, and escalate security alerts. In practice, this involves jumping from system to system, scrambling to piece together disparate data points in order to form a conclusion. Not only do tools report data differently, but when under a tight time deadline, decisions are often made with not nearly enough contextual information.
The result: too many alerts, too little time, and too high a margin of error.
When it comes to high-impact threats such as phishing, host privilege escalation, and, of course, any zero-day attack, manual processes are a serious hindrance, slowing time-to-response. Security threats move fast, and so, too, should our defenses. Let’s take a look at how automation can offer a much faster way.
How to Streamline Alert Investigation with Security Automation
Adding an automation layer can streamline a big chunk of the investigation process. A typical incident response process involves these five phases:
- Detection
- Alerting
- Triage
- Notification
- Response
Security automation can accelerate the most tedious phases: triage, notification, and response.
Using orchestration and automation, your security team can connect all your tools (including the ones that detect and alert on security events) and create machine-to-machine automation that does the rest of the work for you — correlating and analyzing data and aiding in the response process, while also leaving room for strategic human decision points.
The moment an anomalous behavior is detected within your environment and your team is alerted, automation jumps into action, saving your team from:
- Extensive data collection (triage)
- Communicating the status of the investigation, often requiring more context from stakeholders (notification)
- Taking action based on the information available (response)
By automating these tedious and time-consuming tasks, security teams can gain a large chunk of their time back — 83 percent by our estimates. Here’s the breakdown:
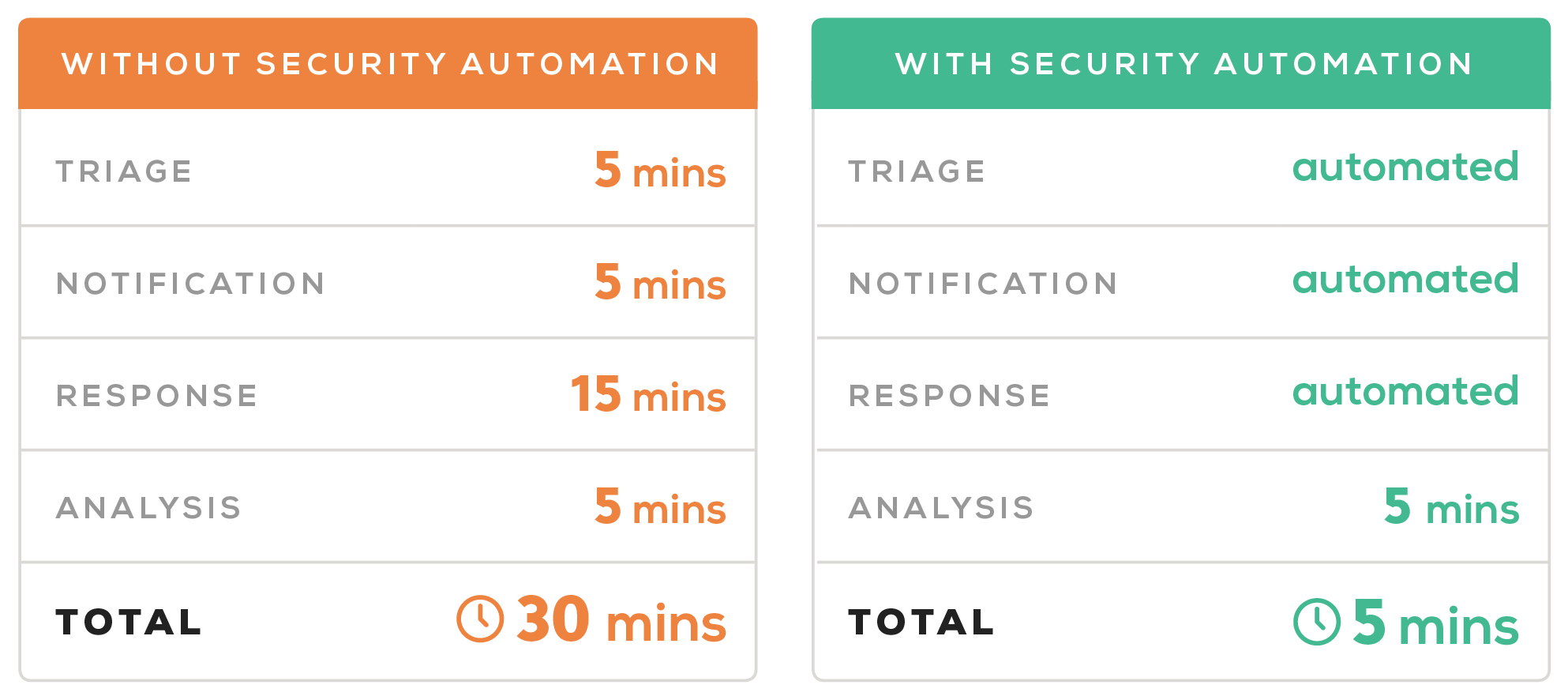
We arrived at these numbers by using:
- A typical host “privilege escalation” investigation process
- Komand’s security orchestration and automation platform
Any use case would fare similarly, since Komand can automate the three most time-intensive phases of investigation so your team can realize measurable security operation gains no matter the incident.
Want to take command of security operations and accelerate time-to-response? Check out our solution, Rapid7's InsightConnect.
