Last week, I joined Rapid7’s venerable penetration testers in Denver for their annual Mega-Hackathon. Once a year, our entire pen testing team gets together to share knowledge, test new tools and techniques (many of them proprietary), and put on a bunch of workshops and quick-fire talks to help our security experts level up and develop their mentoring skills. Those who have read our “Under the Hoodie” research report may already be familiar with some common (and not-so-common) penetration testing stories and stats uncovered by over 268 penetration testing service engagements for our customers.
But a penetration testing megathon, as we call it, offers a unique chance to go beyond the data and get a feel for what a whole host of penetration testers are like in their natural habitat—or at least as natural as a series of hotel meeting rooms stocked with Red Bull and surge protectors can be.
So, what happens when you put 30+ hackers in a room for a week and give them more than 173 days’ worth of pen testing service engagements to work on? As it turns out, in addition to finding myriad ways to demonstrate and communicate risk across client environments, our crack team of security consultants is adept at churning out research and enablement content to support Rapid7’s product, sales, and customer-facing teams. Here are a few completely unscientific takeaways from a week in the room where it happens:
By the numbers
During this year’s megathon, our pen testers collaborated on thousands of hours of engagement work spread across dozens of projects. Most of these were mixed engagements—meaning they spanned a few different categories of testing (e.g., internal and external pen tests alongside a web app test or firewall configuration). There were also a few projects that fell into an “Other” category that included IoT assessments, industrial control system (ICS) assessments, and reviews of highly specific devices or technologies.
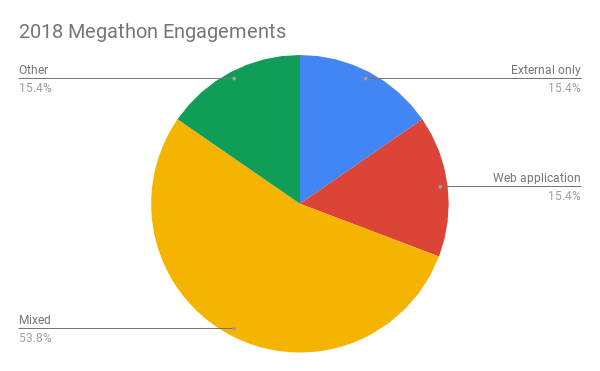
Our penetration testing shop has an unusually deep bench of expertise on everything from mobile apps and ICS to the world’s ever-broadening array of internet-aware devices. One of the major advantages that hackathons offer Rapid7 customers and employees is a chance to benefit from this collective expertise—especially when your hacker peers and mentors are sitting a table away instead of communicating across multiple time zones.
TTP, RCE, XSS, DA
On the off chance readers haven’t encountered enough acronyms in the information security world, an anecdotal survey of findings—and the tooling and techniques used—from this year’s megathon revealed that remote code execution (RCE) vulnerabilities, cross-site scripting (XSS), and suboptimal passwords (of course) remain common weak points across businesses, regardless of size.
The first 12 hours of the Megathon saw a half-dozen fist pumps from folks who got DA (domain administrator in human parlance) quickly as a result of tried-and-true techniques: A little user enumeration and some password spraying yields an account or two; add a pinch of privilege escalation and a dash of lateral movement et voila!—you’ve got yourself a shiny new DA title. Rapid7’s pen testers will be the first to tell anyone who asks that while getting in and gaining sufficient privileges are a key part of the job, they’re only the beginning; the true test of an ethical hacker’s skills is whether he or she is able to communicate that risk to clients in a way that allows them to mitigate or remediate it.
Several members of our team also made use of Metasploit’s modules for either MS17-010 or MS08-067. About half used Metasploit Framework during some part of their engagements, which aligns with the group’s overall preference for open-source tooling:
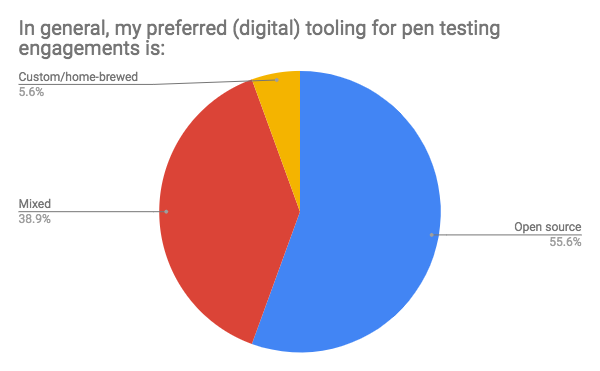
On the home-brew side, most of our folks used their own proprietary tech for three major areas: phishing, payload creation, and beloved one-line scripts they’ve ginned up or learned over the years to serve niche (and often critical) purposes.
Passion quotient
For me, the highlight of Megathon week was the stories our penetration testers shared on video and projector screens after the day’s hacking wound down (at least officially). I love working with our offensive security crew because of their passion and aptitude for side projects that showcase their own brands of individual flair: IoT hacking demos, a breakdown of password-cracking methodologies, stories of epic physical social-engineering feats aided by internet shopping sites, and pet software development projects were all on display after-hours.
Looking for a miniature security conference that covers APT emulation, container escape techniques, and phishing 2FA sessions? Want to run a hands-on hardware hacking workshop that even a total newbie can understand and appreciate? Love a good story about a guy who buys name-brand pizza company gear online and social-engineers his way into a secure area? Or, even better, appreciate a clear, concise demonstration of what risk looks like, what data it leads to, and how to lock it down?
