Today, security professionals are tasked with managing expansive, complex, and dynamic environments that are much more advanced than they were just a decade ago. In our latest installment of Whiteboard Wednesday, we break down the step-by-step approach you can take to gain visibility across a modern environment and the main areas you should focus on:
Watch the full Whiteboard Wednesday video
Five-minute video training
An overview
Today, visibility matters more than ever before. Expansive and ever-changing environments, data, and users means there are many more risks and ways in which adversaries can get in. To keep up, you need to be one (or many) steps ahead. In the video, we discuss the major components of a modern environment and the systems you need to consider integrating with or instrumenting to gain visibility.
Your solar system, your environment
It can be helpful to think of your modern environment as the solar system, with many interdependent planets to protect.
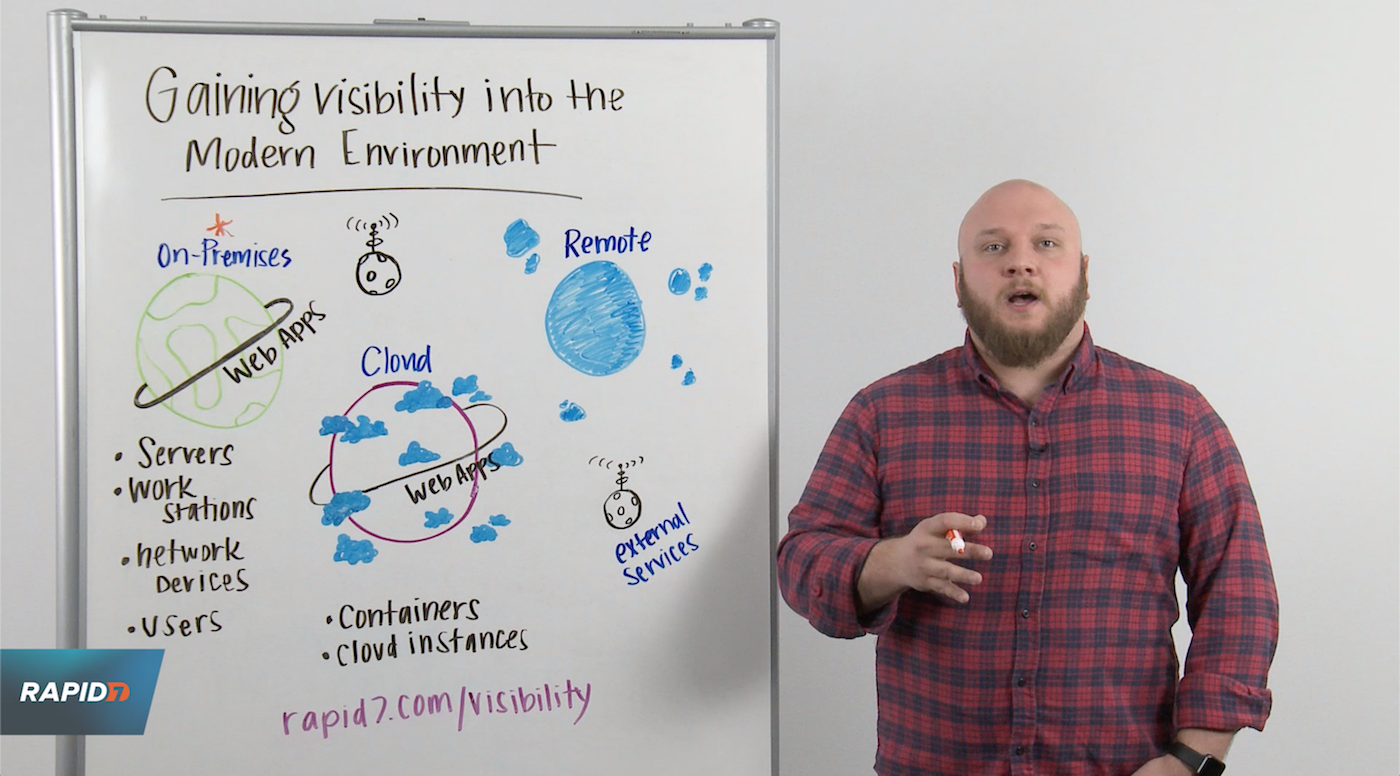
On-premises
The first planet to address when it comes to visibility is on-premises. It holds many important assets and is typically the environment people are most familiar with. There are several ways in which you can gain visibility into your on-premises environment, including:
- Servers in your data center. Modern data centers almost always run a hypervisor, meaning you need to integrate with that hypervisor so it can report to you when new VMs are spun up or taken away in order to maintain visibility.
- Workstations. As new desktops or laptops are added or removed from the environment, you should integrate with things like DHCP so that as new network leases are doled out, you can be notified that something new has been added to the environment.
- Network devices. You need to scan the network, enumerate the devices, and fingerprint them so you know what you have and what versions are running.
- Users. Look to integrate with things like Active Directory to understand who your users are and what they are doing.
The cloud
The next stop in the solar system is gaining visibility into your cloud environment. This is where things get can complex, since it includes cloud infrastructure, instances, configurations, web applications, and containers—you name it, it needs to be protected, and you need visibility. You need to know the moment a new asset is spun up and the moment one is terminated. The configuration layer must also be considered to ensure it’s aligning with best-practice benchmarks. This can be done by integrating with the Infrastructure-as-a-Service (IaaS) provider you’re using, whether it’s Azure, Google Cloud Compute, or AWS.
Remote users
Third, you need to consider securing remote users. It’s becoming more and more common today to have entirely or mostly remote employees, whether they work from home or travel often. This means they’re rarely (or sometimes never) connected to the corporate network. But because they are still accessing sensitive information and systems within the company’s IT environment, you need visibility into what they are doing:
- What devices are they using?
- What apps are they accessing?
- Are they using a VPN?
- Do they follow password policies?
To instrument, these devices you need to use solutions like agents that provide constant communication and beaconing to keep tabs on these assets.
External services
Last but certainly not least is gaining visibility into the external services you use. Although it seems like a small piece of the puzzle, it’s actually a big concern from a security standpoint. As businesses like yours continue to modernize and work with more third-party services, you need visibility into what users are doing on them—even if you don’t own or host these services. You’ll need to integrate with those services directly to gain that visibility.