As our economies start to slowly reopen, knowledge-based jobs are still heavily relying on working from home during the COVID-19 pandemic. It appears that for the foreseeable future, we will maintain a greater-than-usual remote workforce, accessing corporate networks and sensitive information remotely. This will cause the attack surface to grow for many organizations, giving attackers more opportunities to exploit vulnerabilities.
In order to help our customers better track their remote workforce and external-facing assets, we are introducing a new customizable dashboard within InsightVM that makes it easier for our customers to identify remote workforce assets, such as employee laptops, and offers key performance indicators (KPIs) to monitor their changing environment. In addition, this new dashboard provides information around exposure to encryption related vulnerabilities.
With the insights provided in the new dashboard, we hope to drive the following actions for our customers to manage and reduce their cybersecurity risk:
- Create Remediation Projects to facilitate and monitor remediation efforts to mitigate exposure to vulnerabilities or threats.
- Set up metrics using Goals and SLAs to monitor remote and external assets, their configuration, and track remediation efforts.
- Deploy agents on remote workforce assets to maintain ongoing visibility, which can be a challenge since they are often powered off or go offline.
So, let’s dive deeper into how to set up the new dashboard and look at which cards are included.
- Follow these instructions to create a new dashboard from a template. Choose the template titled “External and Remote Workforce Assets Dashboard.”
-
This action will create a local copy of the dashboard for you and save two new asset queries in your query library. These queries are:
- External Assets
- Remote Workforce Assets
They are based on IP ranges and operating system classification and are meant to be starting points for you to customize based on your environment. You can edit them by going to the Management page, Queries tab, and finding the queries with the above names. Instructions on how to use the Query Builder to edit them are available here. For example, if you already tag your external facing assets with an external tag, you can modify the query with the following criteria: asset.tags IN ['external']. When you update these queries, your dashboard will automatically update to reflect the updated criteria.
- In addition, there will be another query called “SSL/TLS Vulnerabilities, PKI” to filter out encryption related vulnerabilities on external facing assets.
We included the following cards in this new dashboard:
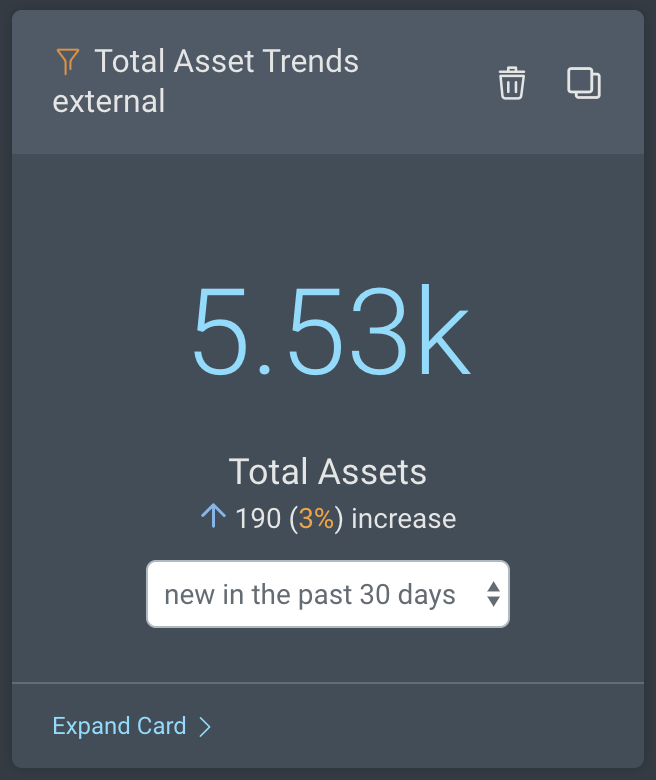
Asset Trends: These cards show the total number of external or remote workforce assets and how those numbers have changed in a specified time period.
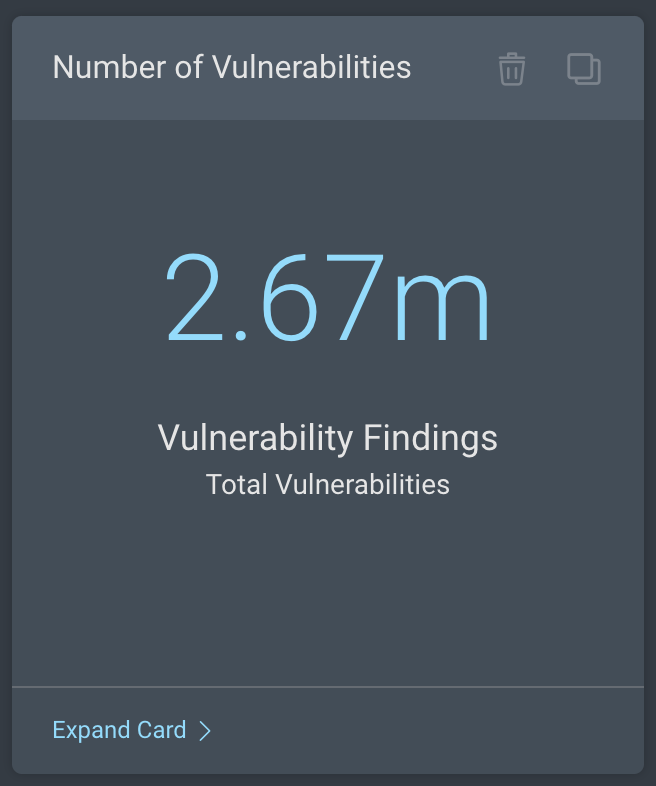
Vulnerability Count: These cards show the total number of vulnerabilities found on external or remote workforce assets. You have the option to clone these cards and filter them further to focus on specific vulnerabilities or severity levels (e.g., CVSS Score > 9). You can do this by clicking on Expand Card and adding additional criteria to the standard query.
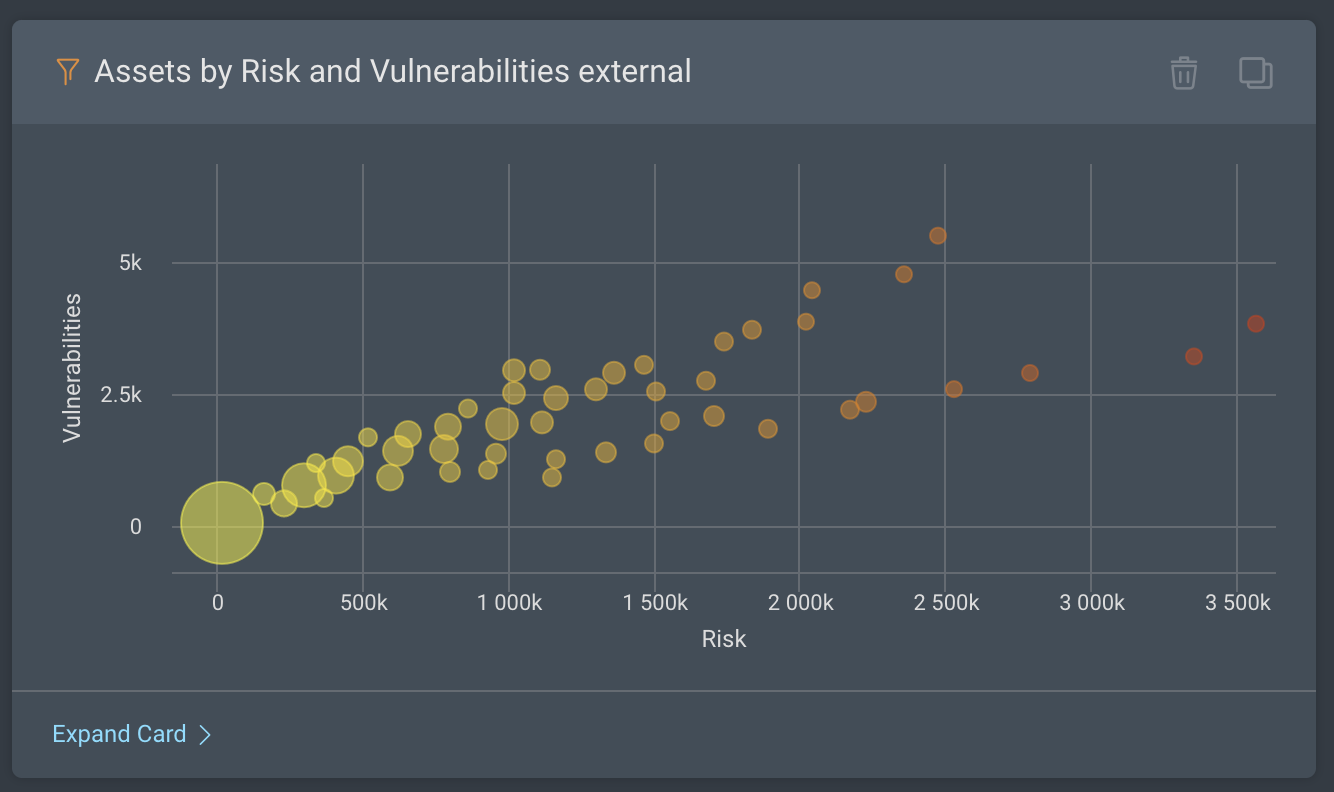
Assets by Risk and Vulnerabilities: These cards include scatter-plot charts with assets ordered by risk and number of vulnerabilities to help you easily identify the riskiest assets in your environment.
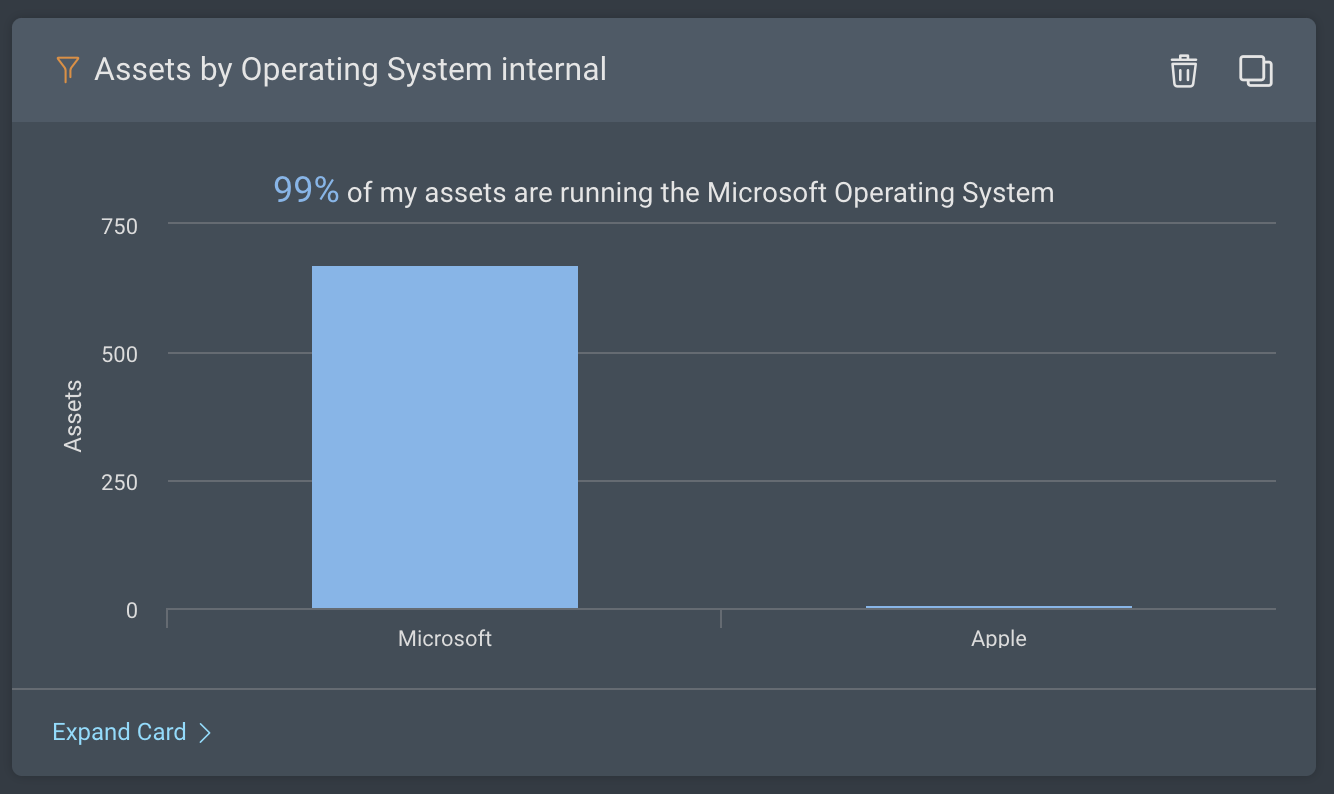
Assets by Operating System: This card provides a breakdown of remote workforce assets by operating systems.
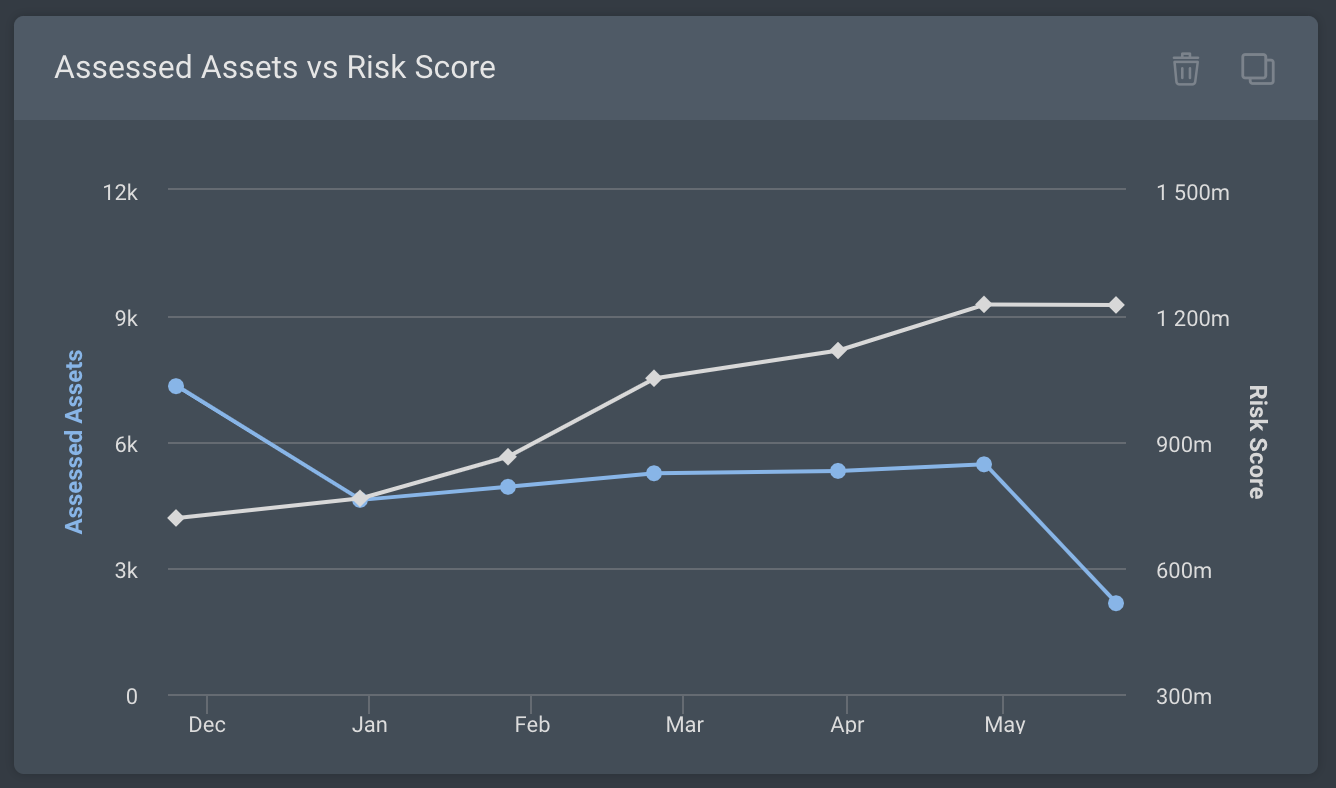
Assessed Assets vs. Risk Score: Repeated both for External Assets and Remote Workforce Assets, this card displays a graph of assessed assets compared to the amount of risk.
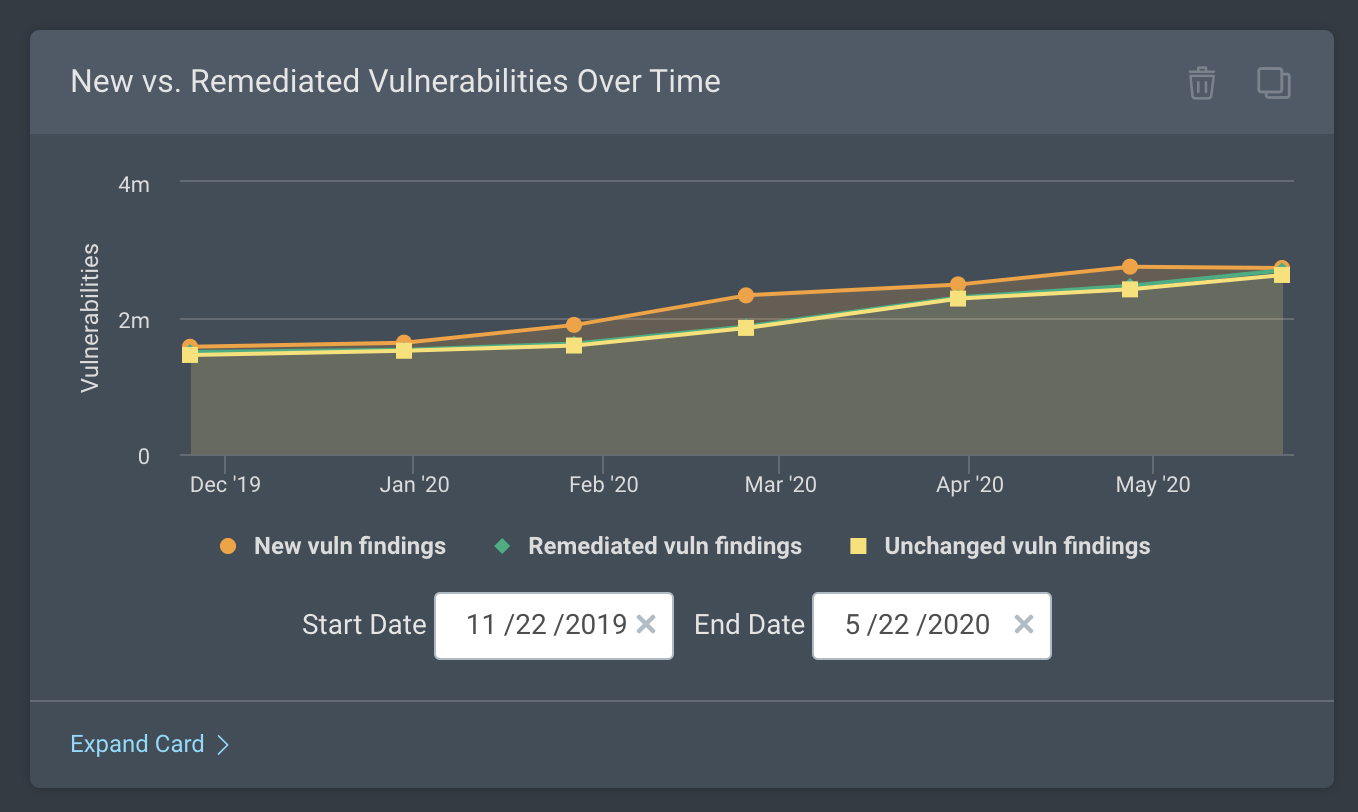
New vs. Remediated Vulnerabilities Over Time: This is a great card to monitor the effectiveness of your remediation efforts by visualizing trends in remediated vulnerability findings, new vulnerability findings, and unchanged vulnerability findings.
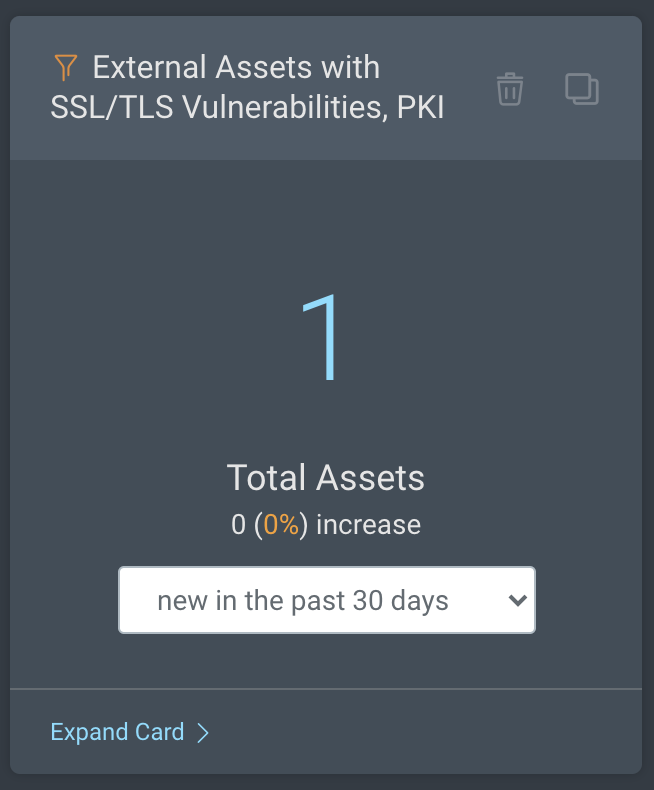
External Assets with SSL/TLS Vulnerabilities, PKI: This card shows the total number of external assets that are exposed to one or more SSL/TLS vulnerabilities.
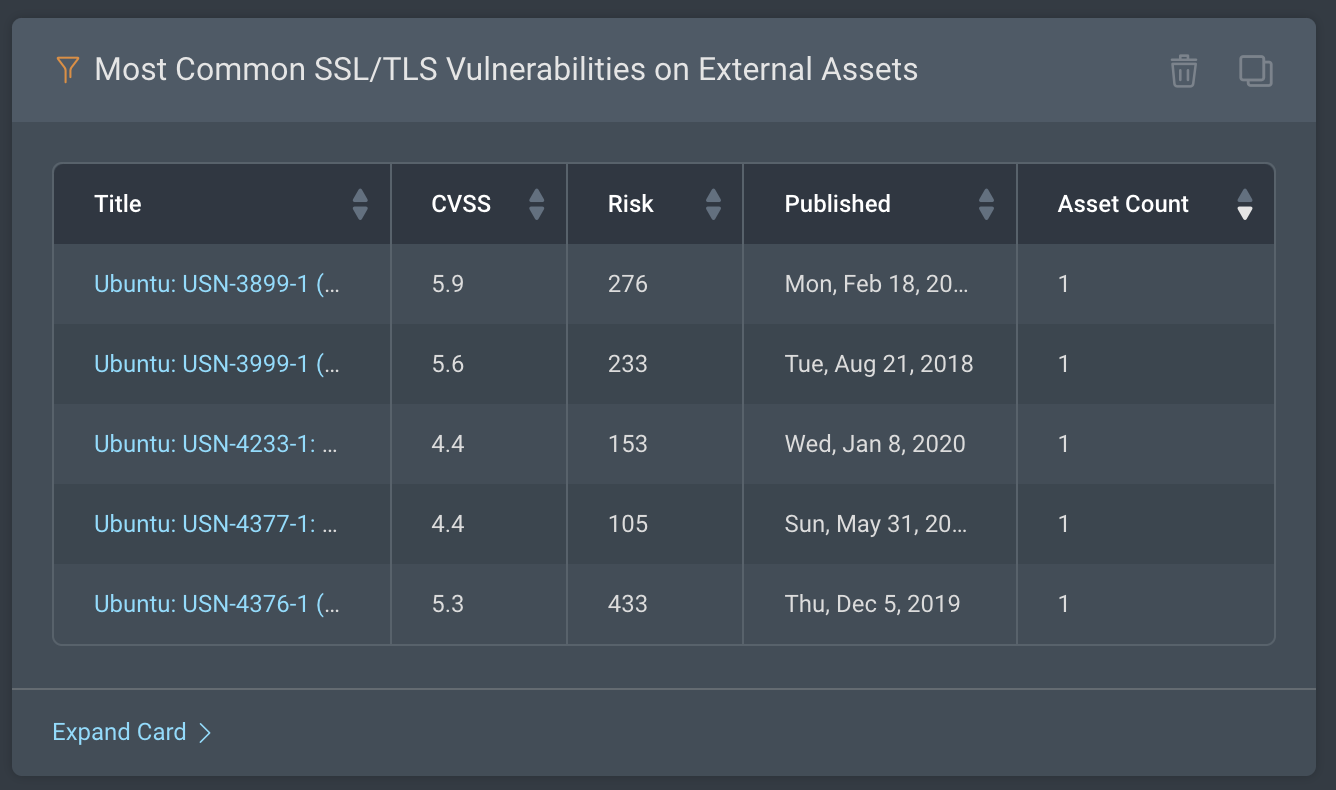
Most Common SSL/TLS Vulnerabilities on External Assets: This card shows the most common SSL/TLS vulnerabilities in your external environment based on the number of affected assets.
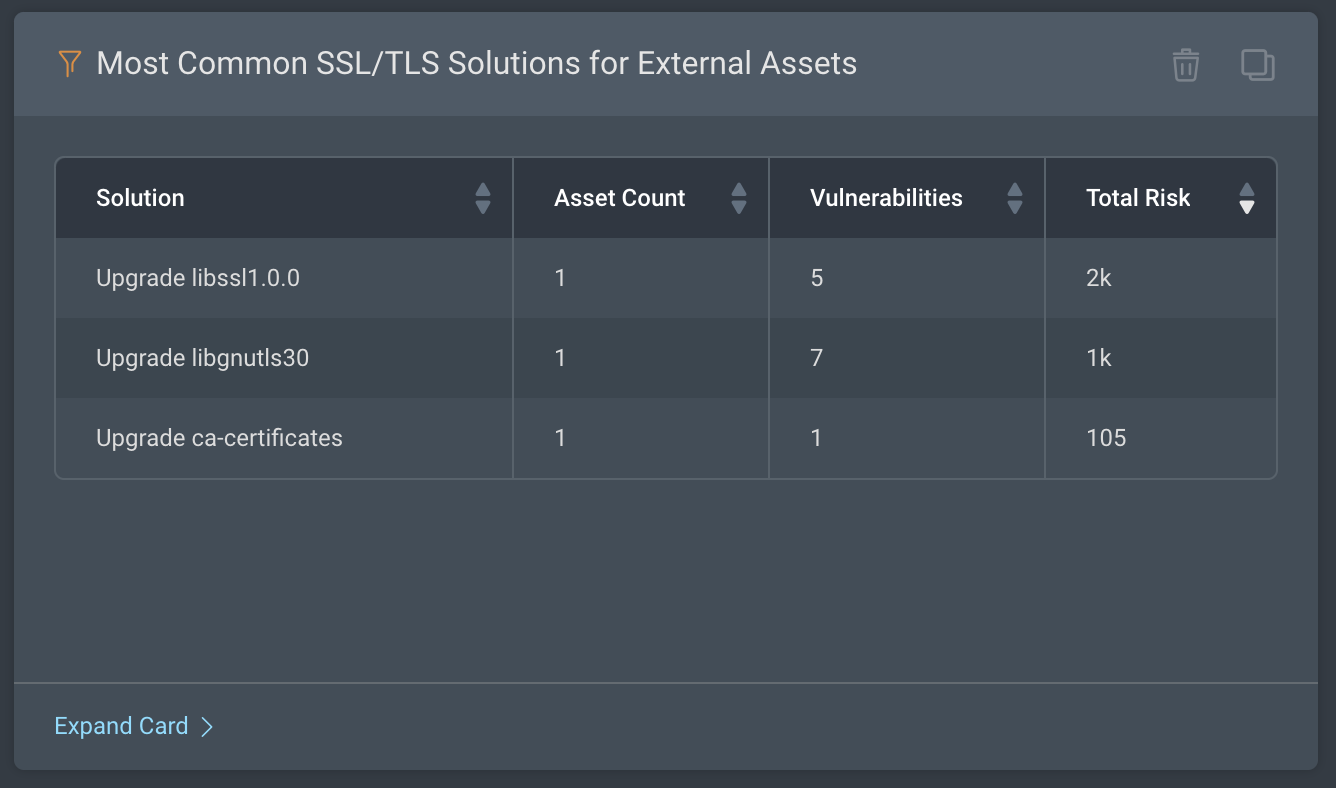
Most Common SSL/TLS Solutions for External Assets: This card shows the remediations or solutions that are the most frequently prescribed to remediate the SSL/TLS vulnerabilities on your external assets.
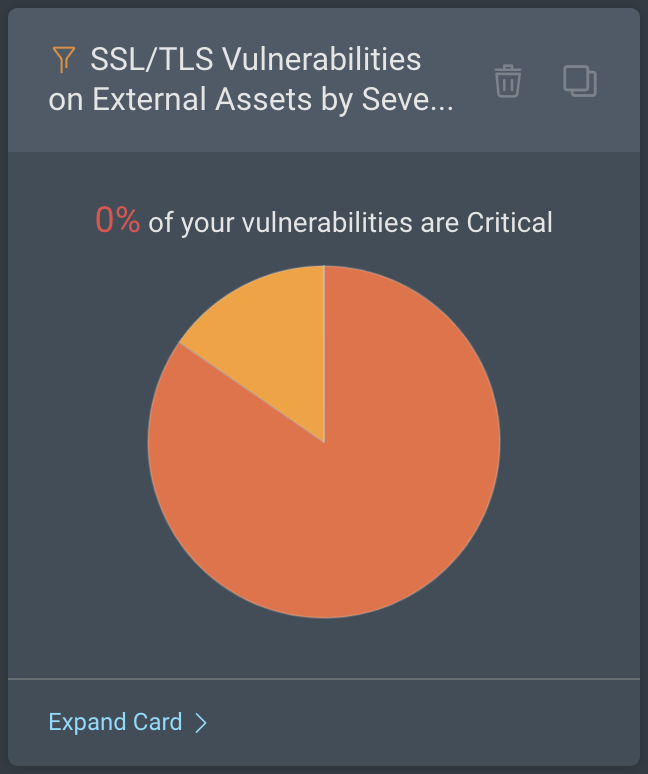
SSL/TLS Vulnerabilities on External Assets by Severity: This card shows the percentage breakdown of the SSL/TLS vulnerabilities on your external-facing assets by their severity levels.
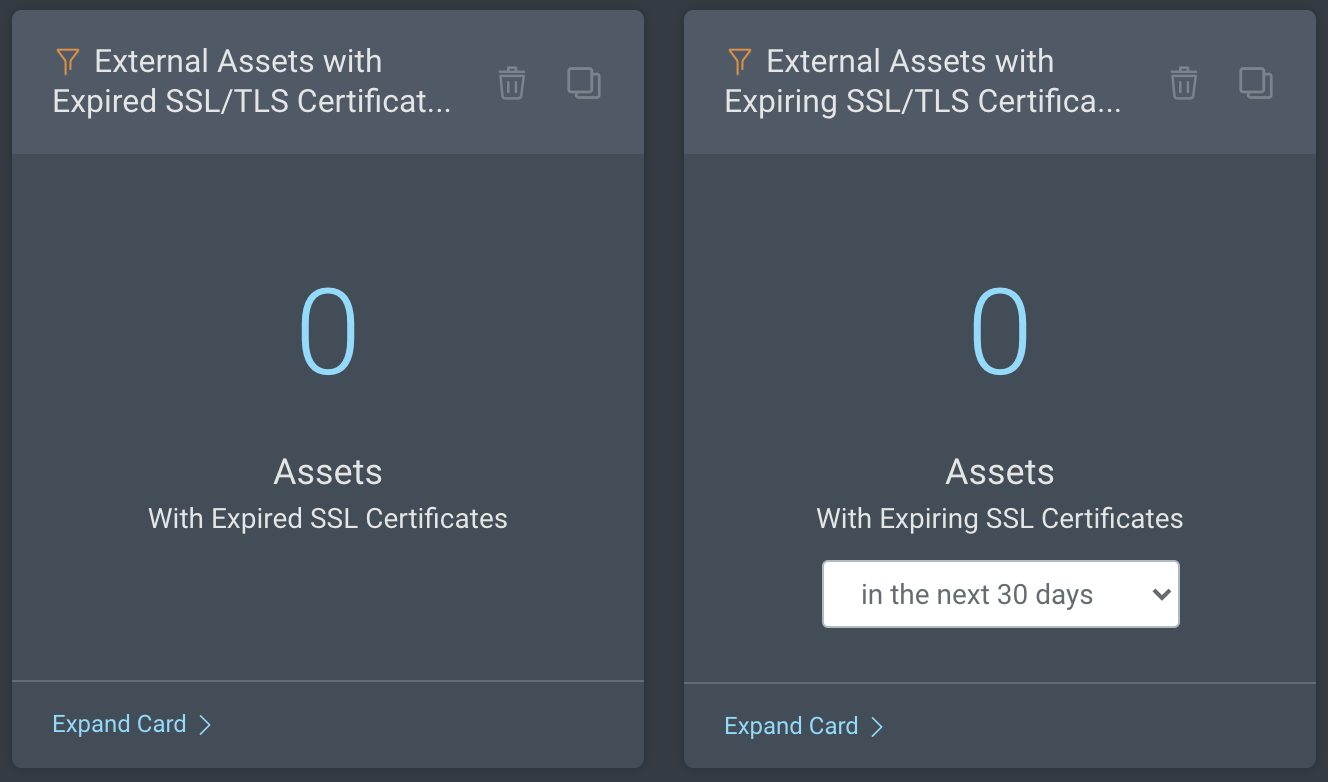
External Assets with Expiring or Expired SSL/TLS Certificates: These cards provide you the number of external assets in your environment that currently have expiring or expired SSL certificates. You can drill into these cards to browse the asset details.
We hope this new dashboard is helpful to you in protecting your environment, as large numbers of your employees now work remotely and attackers look to take advantage of the current COVID-19 pandemic.
