In July, we provided a rundown of what was new in InsightIDR, our cloud-based SIEM tool, from the first half of 2020 (check out the blog post here for a recap). We’ve released some pretty great features and updates since then, so we thought it was time for another recap! This post offers a closer look at some of the recent updates and releases in InsightIDR from Q3 2020.
LEQL Multi-groupby
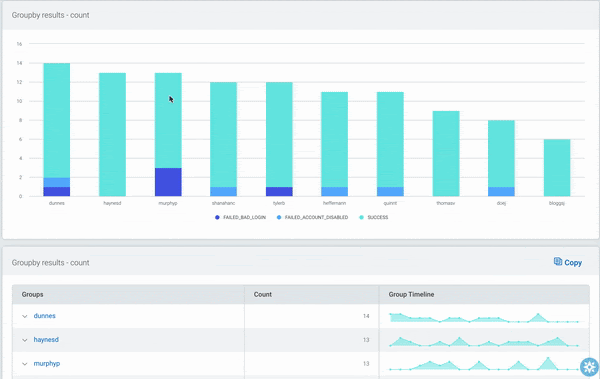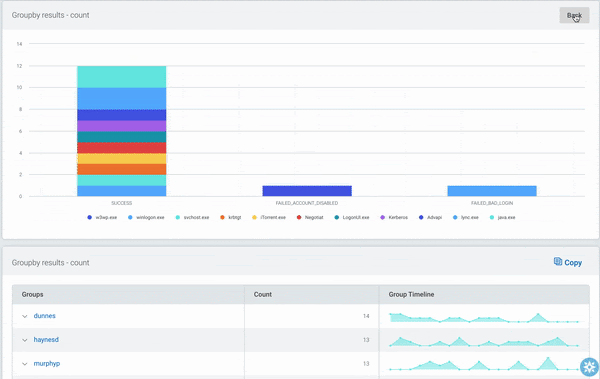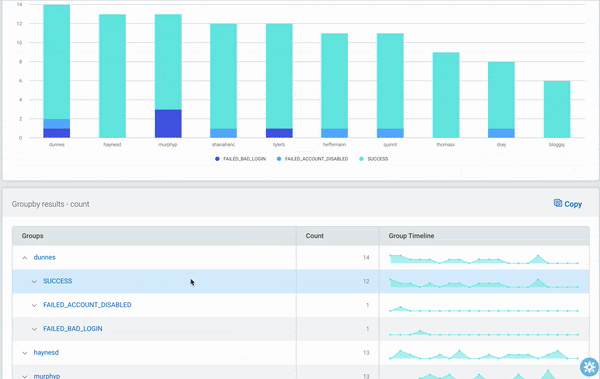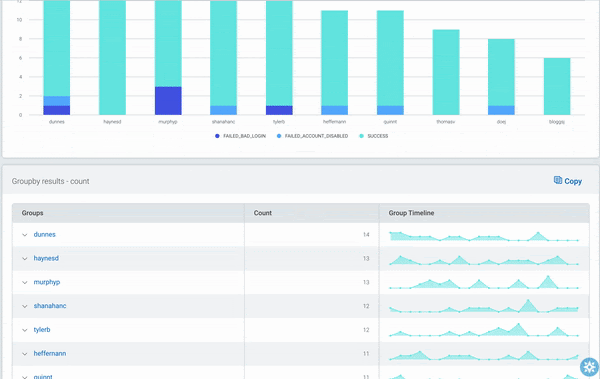
We’ve made many updates to InsightIDR’s Log Search capabilities this past year. Our latest addition, LEQL Multi-groupby, allows customers to group by multiple fields in their log data searches. With LEQL multi-groupby, you can get a more detailed view into your log data by grouping up to five fields in one single query, which reduces the number of queries they need to run in multiple tabs and makes their searches more efficient.
For example, now you can see failed logins by user and service and asset, network traffic by country and application, virus alerts by asset and risk, and so much more. Check out our recent blog for more information on LEQL multi-groupby.
Custom Alert Automation with new InsightConnect integration
Attacks happen fast—your response should, too. This is why InsightIDR, Rapid7’s cloud SIEM, integrates seamlessly with InsightConnect, Rapid7’s Security Orchestration, Automation, and Response (SOAR) solution, to eliminate manual processes and accelerate teams’ response to threats.
Joint customers of InsightIDR and InsightConnect have been able to kick off automation workflows for detected notable behaviors or built-in alerts. And now, with the latest cross-product integration, security teams have even more customization options when it comes to automated response: In addition to kicking off workflows from UBA alerts, joint customers can now trigger custom workflows to automatically initiate predefined actions each time a Custom Alert is triggered in InsightIDR.
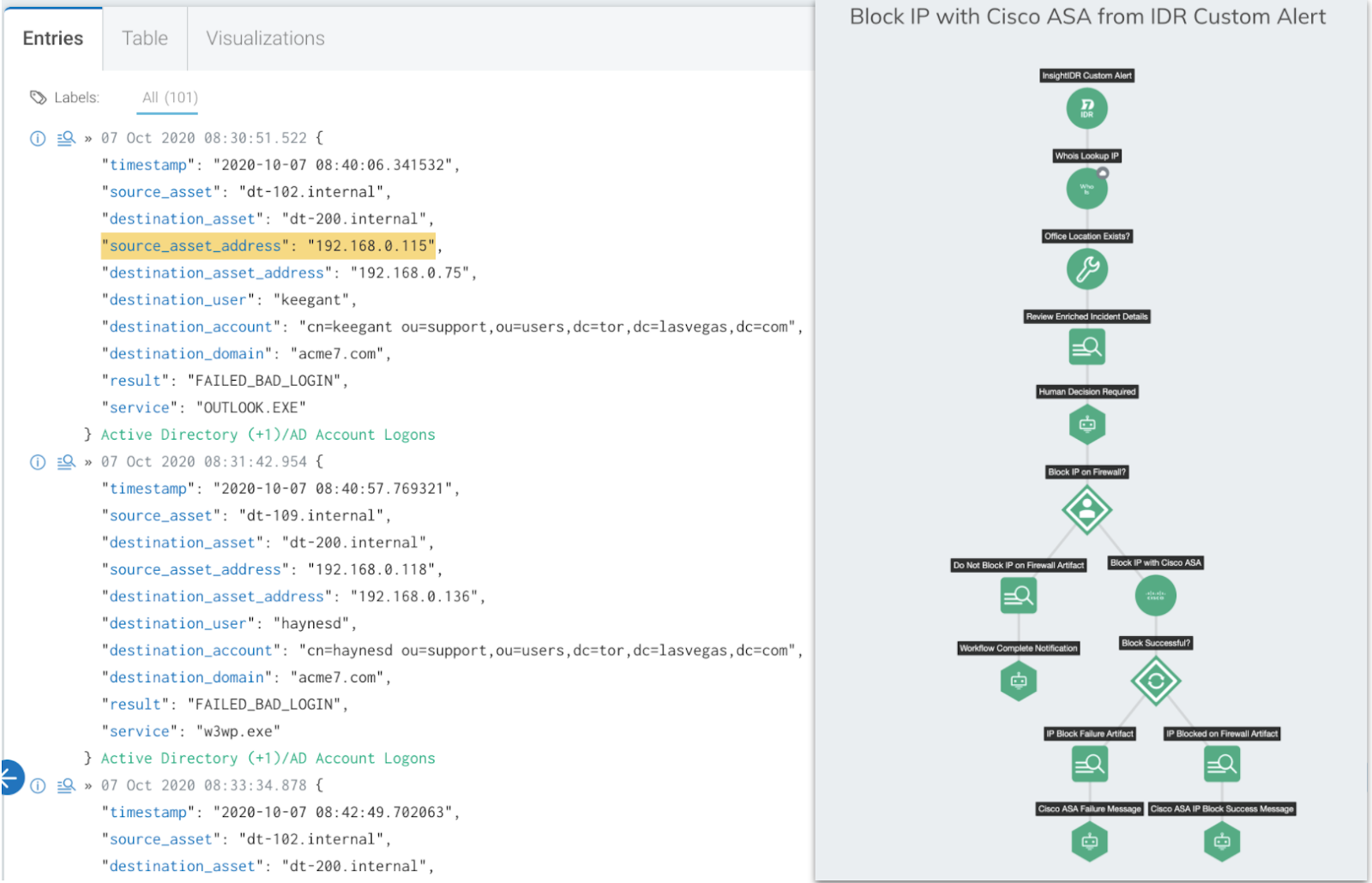
Network Traffic Analysis: Insight Network Sensor for AWS in Early Access
We’re really excited to announce that we’re in Early Access for our latest Network Traffic Analysis updates: coverage for AWS environments. With this upcoming release, InsightIDR customers will be able to easily deploy Insight Network Sensors in AWS cloud environments to monitor their network traffic for full packet analysis. Customers will utilize the VPC Traffic Mirroring feature in AWS to gain access to network traffic.
Notable Log Search and data enhancements
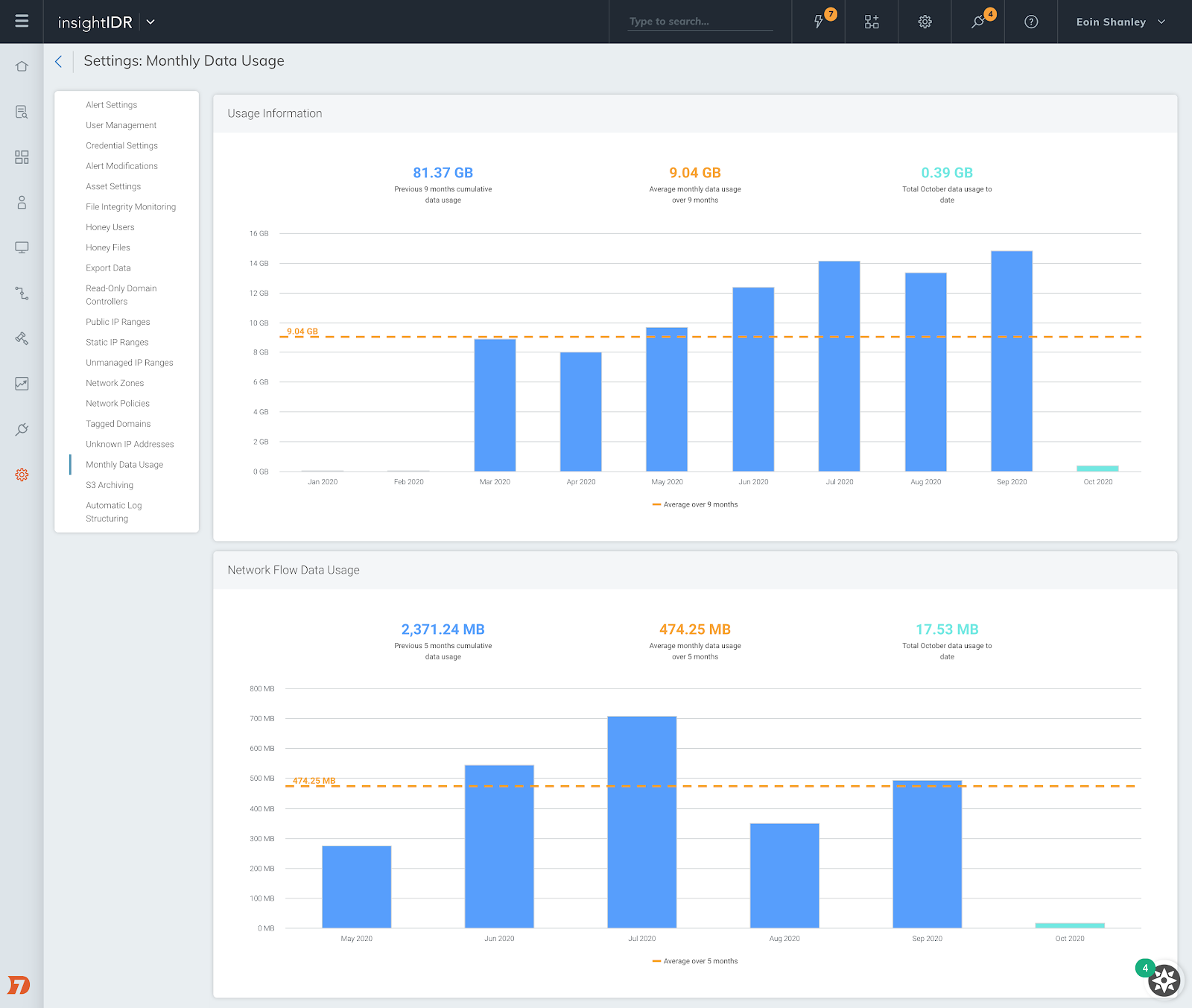
In Q3, we made several updates and added new features to our Log Search and Log Data capabilities. Here are a few of the highlights from the past few months:
- Monthly Log Data Usage Chart: You can now view your monthly log data usage in Settings > Monthly Data Usage. Check out your data usage over the past 12 months and better understand trends over time.
- Insight Agent Log Collection: You can now send the contents of any text log file in real time to InsightIDR! By creating logging.json files to be downloaded on each asset, the Insight Agent collects any and all additional logs from Application/Security/System window events. See more on this new capability in our help docs here.
- Updated Date Picker in Log Search: Our latest version of the date picker provides a larger selection of quick date ranges to choose from, an area where customers can choose a custom relative time range, and an easier way to select an absolute date range.
MDR Elite introduces “Active Response” for end-to-end detection and response
Rapid7 MDR with Active Response extends your team with 24x7 end-to-end threat detection and response to protect your business, reduce attacker dwell time, and accelerate your time to response. This new Active Response functionality enables Rapid7’s MDR SOC experts to contain users or endpoints on your behalf within minutes (not hours or days).
Customers who enable Active Response can be as hands-off or hands-on as they’d like with the option to cancel any action from their desktop or mobile device. Real-time updates through email, text, Slack, phone, and inside of InsightIDR allow security teams to stay in the loop on any alerts and actions MDR experts are prepared to take action on. Learn more about what Active Response can do for your organization in our recent blog post.
InsightIDR Detection Library
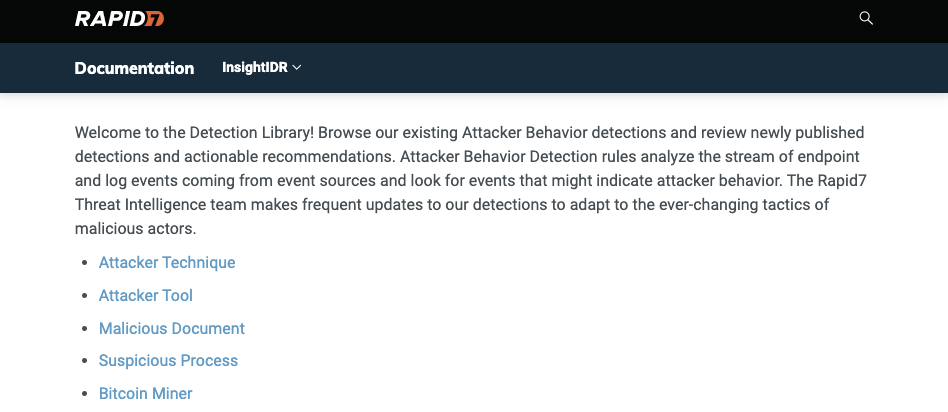
Prospects and customers can now see InsightIDR’s latest Attacker Behavior detections, along with actionable recommendations sourced directly from our Threat Intelligence and Detection Engineering team, in the publicly available InsightIDR Detection Library.
This library provides transparency and visibility to customers on what InsigthIDR’s Attacker Behavior detections are and why they work the way they do. Along with our expertly sourced recommendations, customers will have the guidance to confidently investigate and respond to these alerts. Check out the InsightIDR Detection Library to stay up-to-date on newly published detections and recommendations.
Event Source Enhancements and Updates
Recent event source updates include:
- Collector warning for number of Event Sources: We will now notify you when a collector contains more than the maximum recommended (80) event sources, or is nearing capacity. This way, you can proactively assess your event source distribution, and add an additional collector as needed.
- Generic syslog are now combined with Custom Logs: Customers can configure the syslog event source and see events in Log Search regardless of whether the header parses or not.
We also released new event sources in Q3, including:
- Zoom Pro (to learn more about this integration, check out our recent blog)
- Palo Alto Traps TMS
Stay tuned for more!
As always, we’re continuing to work on exciting product enhancements and releases throughout the year. Keep an eye on our blog and release notes as we continue to highlight the latest in detection and response at Rapid7.
NEVER MISS A BLOG
Get the latest stories, expertise, and news about security today.
Subscribe
