Microsoft is addressing 130 vulnerabilities this July Patch Tuesday, including five zero-day vulnerabilities, and eight further critical remote code execution (RCE) vulnerabilities. Overall, it’s safe to say that this is a busier Patch Tuesday than the past couple of months. Note that the total count of vulnerabilities reported no longer includes any Edge-on-Chromium fixes.
Office zero-day maldoc vuln: no patch, no problem
Surprisingly, there is no patch yet for one of the five zero-day vulnerabilities. Microsoft is actively investigating publicly-disclosed Office RCE CVE-2023-36884, and promises to update the advisory as soon as further guidance is available. Exploitation requires the victim to open a specially crafted malicious document, which would typically be delivered via email.
A Microsoft Security Research Centre (MSRC) blog post links exploitation of this vulnerability with Storm-0978, Microsoft’s designation for a cybercriminal group based out of Russia also tracked across the wider industry under the name RomCom. MSRC suggests that RomCom / Storm-0978 is operating in support of Russian intelligence operations. The same threat actor has also been associated with ransomware attacks targeting a wide array of victims.
Defenders who are understandably unsettled by the lack of immediate patches for CVE-2023-36884 should consult the multiple mitigation options on the advisory. Microsoft claims that assets with Defender for Office 365 are already protected. Further options include an existing optional Defender for Endpoint Attack Surface Reduction (ASR) rule to prevent Office from creating child processes, and a registry modification to disable the vulnerable cross-protocol file navigation. The registry option might be the most straightforward option for organizations without a mature Defender program, but Microsoft does warn that certain use cases relying on the functionality would be impacted if this mitigation is deployed.
There are broad similarities to last year’s Follina vulnerability, which was discussed publicly for over two weeks starting late May 2023 before Microsoft patched it on June 14th as part of Patch Tuesday. While it’s possible that a patch for CVE-2023-36884 will be issued as part of next month’s Patch Tuesday, Microsoft Office is deployed just about everywhere, and this threat actor is making waves; admins should be ready for an out-of-cycle security update for CVE-2023-36884.
The menu of mitigation options here should offer something for every Microsoft shop, but it will come as something of a relief that Microsoft is offering patches for the four other zero-day vulnerabilities mentioned in this month’s Security Update Guide.
MSHTML, Windows Error Reporting: zero-day elevation of privilege vulns
CVE-2023-32046 describes a vulnerability in the MSHTML browser rendering engine which would allow an attacker to act with the same rights as the exploited user account. Successful exploitation requires the victim to open a specially-crafted malicious file, typically delivered either via email or a web page. Assets where Internet Explorer 11 has been fully disabled are still vulnerable until patched; the MSHTML engine remains installed within Windows regardless of the status of IE11, since it is used in other contexts (e.g. Outlook).
A separate vulnerability in the Windows Error Reporting Service allows elevation to the Administrator role via abuse of Windows performance tracing. To exploit CVE-2023-36874, an attacker must already have existing local access to an asset, so this vulnerability will most likely make up part of a longer exploit chain.
SmartScreen & Outlook: zero-day security feature bypass vulns
Rounding out this month’s zero-day vulnerabilities are two security feature bypass flaws. CVE-2023-32049 allows an attacker to formulate a URL which will bypass the Windows SmartScreen “Do you want to open this file?” dialog. Previous SmartScreen bypasses have been exploited extensively, not least for no-notice delivery of ransomware.
Broadly similar is CVE-2023-35311, which describes a bypass of the Microsoft Outlook Security Notice dialog via a specially-crafted URL.
Windows RRAS: critical RCEs
Eight further critical RCE vulnerabilities are also patched, including three related vulnerabilities in the Windows Routing and Remote Access Service (RRAS) with CVSS v3 base score of 9.8 (CVE-2023-35365, CVE-2023-35366, and CVE-2023-35367). In each case, an attacker can send specially-crafted packets to vulnerable assets to achieve RCE. Happily, RRAS is not installed or configured by default, but admins with RRAS-enabled Windows Server installations will undoubtedly want to prioritize remediation.
SharePoint: critical RCEs
Anyone responsible for on-prem SharePoint should patch to avoid a variety of potential impacts from exploitation of CVE-2023-33157 and CVE-2023-33160, including information disclosure and editing, as well as reduced availability of the targeted environment. While both of these vulnerabilities require that an attacker already be authenticated as a user with at least Site Member privileges, this isn’t necessarily much of a defense, since this is the lowest standard permission group with the least privileges other than the read-only Site Visitor role, and will typically be widely granted. Microsoft assesses exploitation as more likely for both of these.
Windows core components: critical RCEs
The remainder of this month’s critical RCE patches target flaws in the Windows Layer-2 Bridge Network Driver (CVE-2023-35315), and usual suspects Windows Message Queuing (CVE-2023-32057) and Windows PGM (CVE-2023-35297).
Windows Remote Desktop: security feature bypass
CVE-2023-35352 will be of interest to anyone running an RDP server. Although the advisory is short on detail, an attacker could bypass certificate or private key authentication when establishing a remote desktop protocol session. Although the CVSS v3 base score of 7.5 falls short of the critical band, this is only because Microsoft has scored this vulnerability as having no impact on either confidentiality or availability, probably because the scoring is against the RDP service itself rather than whatever may be accessed downstream; this seems like a case where CVSS cannot fully capture the potential risk, and Microsoft’s Security Update Severity Rating System does rank this vulnerability as critical.
Summary Charts
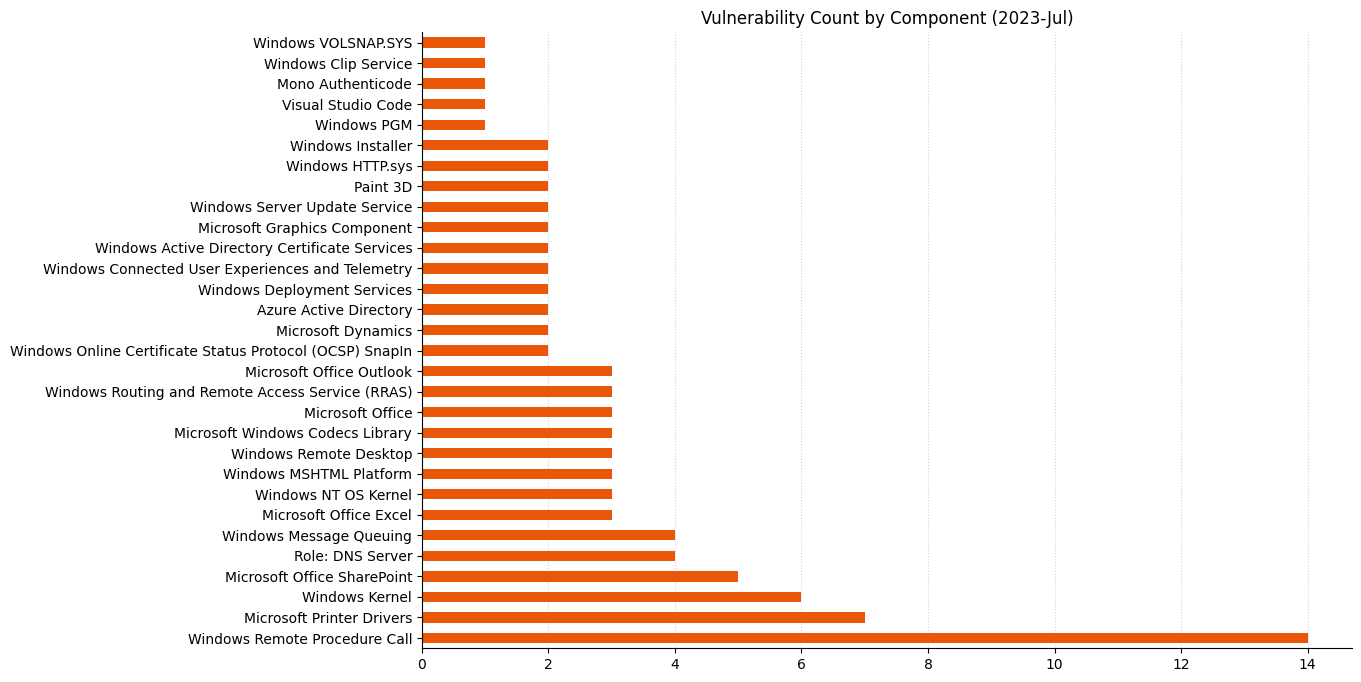
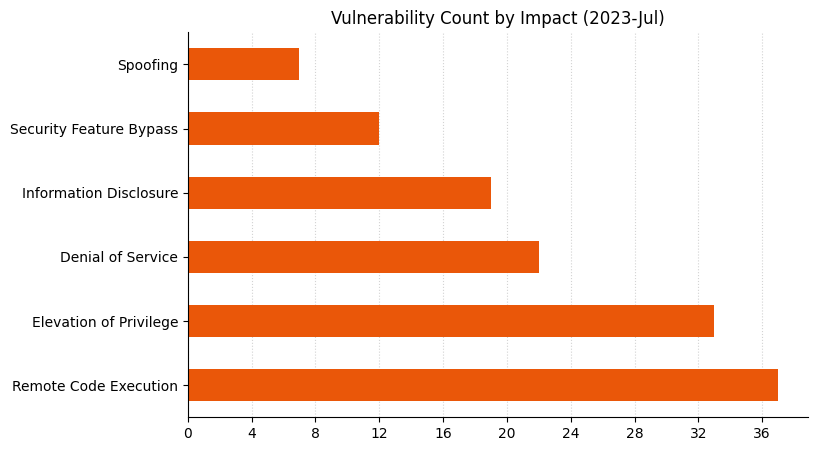
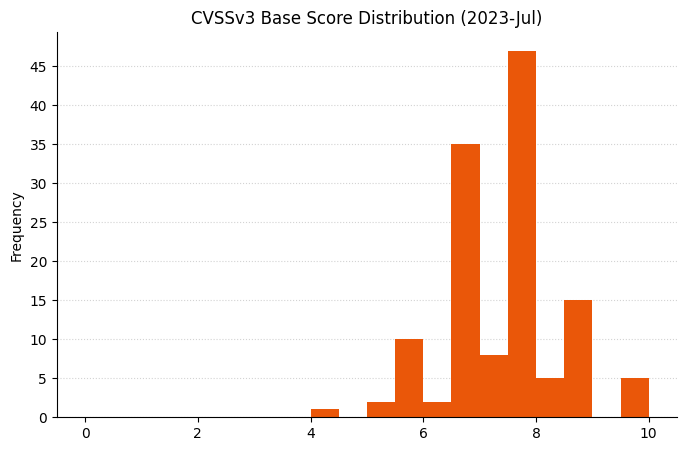
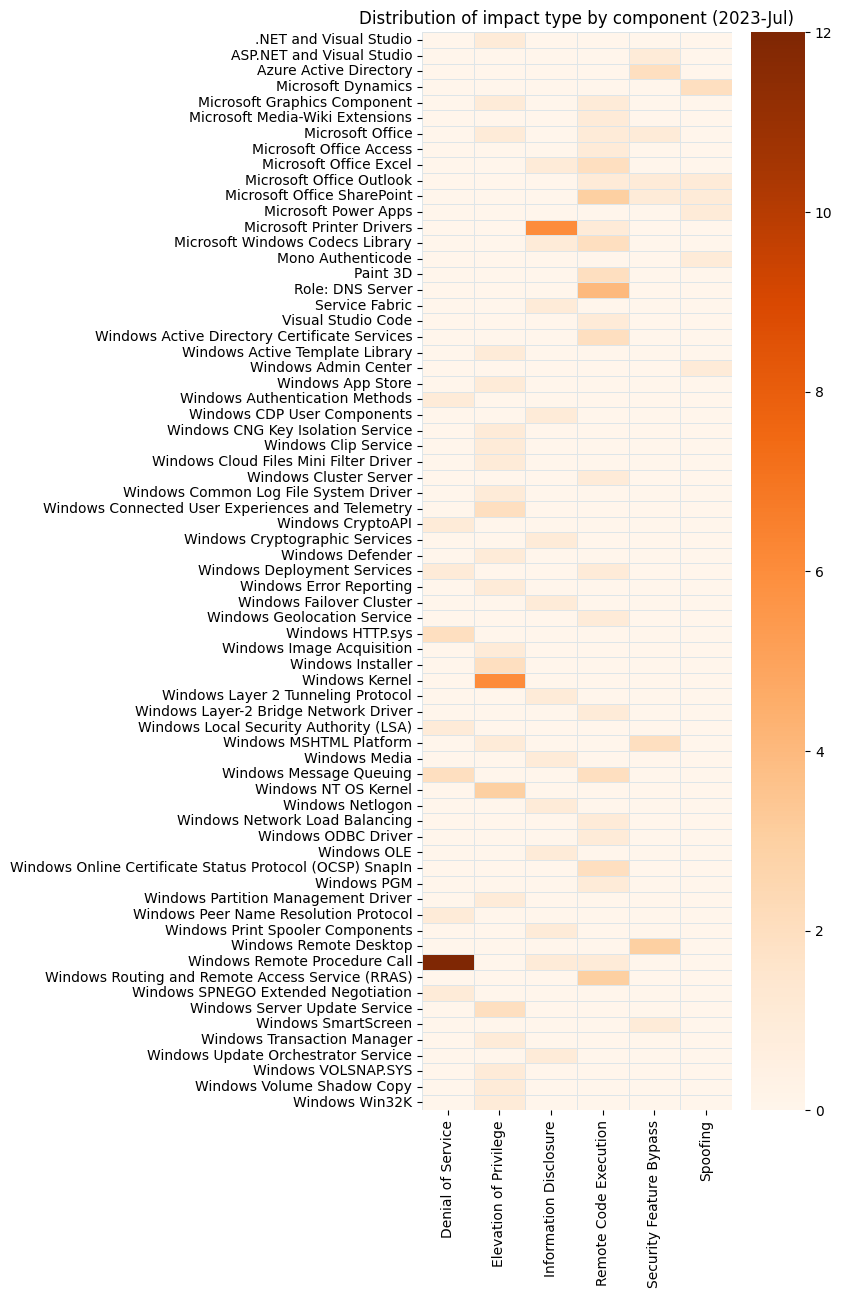
Summary Tables
Apps vulnerabilities
| CVE | Title | Exploited? | Publicly disclosed? | CVSSv3 base score |
|---|---|---|---|---|
| CVE-2023-32047 | Paint 3D Remote Code Execution Vulnerability | No | No | 7.8 |
| CVE-2023-35374 | Paint 3D Remote Code Execution Vulnerability | No | No | 7.8 |
Azure vulnerabilities
| CVE | Title | Exploited? | Publicly disclosed? | CVSSv3 base score |
|---|---|---|---|---|
| CVE-2023-36868 | Azure Service Fabric on Windows Information Disclosure Vulnerability | No | No | 6.5 |
Developer Tools vulnerabilities
| CVE | Title | Exploited? | Publicly disclosed? | CVSSv3 base score |
|---|---|---|---|---|
| CVE-2023-35333 | MediaWiki PandocUpload Extension Remote Code Execution Vulnerability | No | No | 8.8 |
| CVE-2023-33170 | ASP.NET and Visual Studio Security Feature Bypass Vulnerability | No | No | 8.1 |
| CVE-2023-33127 | .NET and Visual Studio Elevation of Privilege Vulnerability | No | No | 8.1 |
| CVE-2023-36867 | Visual Studio Code GitHub Pull Requests and Issues Extension Remote Code Execution Vulnerability | No | No | 7.8 |
| CVE-2023-35373 | Mono Authenticode Validation Spoofing Vulnerability | No | No | 5.3 |
ESU vulnerabilities
| CVE | Title | Exploited? | Publicly disclosed? | CVSSv3 base score |
|---|---|---|---|---|
| CVE-2023-32050 | Windows Installer Elevation of Privilege Vulnerability | No | No | 7 |
Microsoft Dynamics vulnerabilities
| CVE | Title | Exploited? | Publicly disclosed? | CVSSv3 base score |
|---|---|---|---|---|
| CVE-2023-33171 | Microsoft Dynamics 365 (on-premises) Cross-site Scripting Vulnerability | No | No | 8.2 |
| CVE-2023-35335 | Microsoft Dynamics 365 (on-premises) Cross-site Scripting Vulnerability | No | No | 8.2 |
| CVE-2023-32052 | Microsoft Power Apps (online) Spoofing Vulnerability | No | No | 5.4 |
Microsoft Office vulnerabilities
| CVE | Title | Exploited? | Publicly disclosed? | CVSSv3 base score |
|---|---|---|---|---|
| CVE-2023-33150 | Microsoft Office Security Feature Bypass Vulnerability | No | No | 9.6 |
| CVE-2023-33159 | Microsoft SharePoint Server Spoofing Vulnerability | No | No | 8.8 |
| CVE-2023-33160 | Microsoft SharePoint Server Remote Code Execution Vulnerability | No | No | 8.8 |
| CVE-2023-33134 | Microsoft SharePoint Server Remote Code Execution Vulnerability | No | No | 8.8 |
| CVE-2023-33157 | Microsoft SharePoint Remote Code Execution Vulnerability | No | No | 8.8 |
| CVE-2023-35311 | Microsoft Outlook Security Feature Bypass Vulnerability | Yes | No | 8.8 |
| CVE-2023-33149 | Microsoft Office Graphics Remote Code Execution Vulnerability | No | No | 7.8 |
| CVE-2023-33148 | Microsoft Office Elevation of Privilege Vulnerability | No | No | 7.8 |
| CVE-2023-33158 | Microsoft Excel Remote Code Execution Vulnerability | No | No | 7.8 |
| CVE-2023-33161 | Microsoft Excel Remote Code Execution Vulnerability | No | No | 7.8 |
| CVE-2023-33152 | Microsoft ActiveX Remote Code Execution Vulnerability | No | No | 7 |
| CVE-2023-33153 | Microsoft Outlook Remote Code Execution Vulnerability | No | No | 6.8 |
| CVE-2023-33151 | Microsoft Outlook Spoofing Vulnerability | No | No | 6.5 |
| CVE-2023-33162 | Microsoft Excel Information Disclosure Vulnerability | No | No | 5.5 |
| CVE-2023-33165 | Microsoft SharePoint Server Security Feature Bypass Vulnerability | No | No | 4.3 |
Microsoft Office Windows ESU vulnerabilities
| CVE | Title | Exploited? | Publicly disclosed? | CVSSv3 base score |
|---|---|---|---|---|
| CVE-2023-36884 | Office and Windows HTML Remote Code Execution Vulnerability | Yes | Yes | 8.3 |
System Center vulnerabilities
| CVE | Title | Exploited? | Publicly disclosed? | CVSSv3 base score |
|---|---|---|---|---|
| CVE-2023-33156 | Microsoft Defender Elevation of Privilege Vulnerability | No | No | 6.3 |
Windows vulnerabilities
| CVE | Title | Exploited? | Publicly disclosed? | CVSSv3 base score |
|---|---|---|---|---|
| CVE-2023-32049 | Windows SmartScreen Security Feature Bypass Vulnerability | Yes | No | 8.8 |
| CVE-2023-35315 | Windows Layer-2 Bridge Network Driver Remote Code Execution Vulnerability | No | No | 8.8 |
| CVE-2023-35364 | Windows Kernel Elevation of Privilege Vulnerability | No | No | 8.8 |
| CVE-2023-35302 | Microsoft PostScript and PCL6 Class Printer Driver Remote Code Execution Vulnerability | No | No | 8.8 |
| CVE-2023-29347 | Windows Admin Center Spoofing Vulnerability | No | No | 8.7 |
| CVE-2023-21756 | Windows Win32k Elevation of Privilege Vulnerability | No | No | 7.8 |
| CVE-2023-35317 | Windows Server Update Service (WSUS) Elevation of Privilege Vulnerability | No | No | 7.8 |
| CVE-2023-32056 | Windows Server Update Service (WSUS) Elevation of Privilege Vulnerability | No | No | 7.8 |
| CVE-2023-35313 | Windows Online Certificate Status Protocol (OCSP) SnapIn Remote Code Execution Vulnerability | No | No | 7.8 |
| CVE-2023-35323 | Windows OLE Remote Code Execution Vulnerability | No | No | 7.8 |
| CVE-2023-35356 | Windows Kernel Elevation of Privilege Vulnerability | No | No | 7.8 |
| CVE-2023-35357 | Windows Kernel Elevation of Privilege Vulnerability | No | No | 7.8 |
| CVE-2023-35358 | Windows Kernel Elevation of Privilege Vulnerability | No | No | 7.8 |
| CVE-2023-35363 | Windows Kernel Elevation of Privilege Vulnerability | No | No | 7.8 |
| CVE-2023-35304 | Windows Kernel Elevation of Privilege Vulnerability | No | No | 7.8 |
| CVE-2023-35305 | Windows Kernel Elevation of Privilege Vulnerability | No | No | 7.8 |
| CVE-2023-35343 | Windows Geolocation Service Remote Code Execution Vulnerability | No | No | 7.8 |
| CVE-2023-33155 | Windows Cloud Files Mini Filter Driver Elevation of Privilege Vulnerability | No | No | 7.8 |
| CVE-2023-35362 | Windows Clip Service Elevation of Privilege Vulnerability | No | No | 7.8 |
| CVE-2023-35337 | Win32k Elevation of Privilege Vulnerability | No | No | 7.8 |
| CVE-2023-32051 | Raw Image Extension Remote Code Execution Vulnerability | No | No | 7.8 |
| CVE-2023-35320 | Connected User Experiences and Telemetry Elevation of Privilege Vulnerability | No | No | 7.8 |
| CVE-2023-35353 | Connected User Experiences and Telemetry Elevation of Privilege Vulnerability | No | No | 7.8 |
| CVE-2023-35352 | Windows Remote Desktop Security Feature Bypass Vulnerability | No | No | 7.5 |
| CVE-2023-35325 | Windows Print Spooler Information Disclosure Vulnerability | No | No | 7.5 |
| CVE-2023-35339 | Windows CryptoAPI Denial of Service Vulnerability | No | No | 7.5 |
| CVE-2023-32084 | HTTP.sys Denial of Service Vulnerability | No | No | 7.5 |
| CVE-2023-35298 | HTTP.sys Denial of Service Vulnerability | No | No | 7.5 |
| CVE-2023-35348 | Active Directory Federation Service Security Feature Bypass Vulnerability | No | No | 7.5 |
| CVE-2023-35347 | Microsoft Install Service Elevation of Privilege Vulnerability | No | No | 7.1 |
| CVE-2023-35360 | Windows Kernel Elevation of Privilege Vulnerability | No | No | 7 |
| CVE-2023-35361 | Windows Kernel Elevation of Privilege Vulnerability | No | No | 7 |
| CVE-2023-35336 | Windows MSHTML Platform Security Feature Bypass Vulnerability | No | No | 6.5 |
| CVE-2023-35308 | Windows MSHTML Platform Security Feature Bypass Vulnerability | No | No | 6.5 |
| CVE-2023-35331 | Windows Local Security Authority (LSA) Denial of Service Vulnerability | No | No | 6.5 |
| CVE-2023-32037 | Windows Layer-2 Bridge Network Driver Information Disclosure Vulnerability | No | No | 6.5 |
| CVE-2023-35329 | Windows Authentication Denial of Service Vulnerability | No | No | 6.5 |
| CVE-2023-35296 | Microsoft PostScript and PCL6 Class Printer Driver Information Disclosure Vulnerability | No | No | 6.5 |
| CVE-2023-32083 | Microsoft Failover Cluster Information Disclosure Vulnerability | No | No | 6.5 |
| CVE-2023-36871 | Azure Active Directory Security Feature Bypass Vulnerability | No | No | 6.5 |
| CVE-2023-32041 | Windows Update Orchestrator Service Information Disclosure Vulnerability | No | No | 5.5 |
| CVE-2023-35326 | Windows CDP User Components Information Disclosure Vulnerability | No | No | 5.5 |
| CVE-2023-36872 | VP9 Video Extensions Information Disclosure Vulnerability | No | No | 5.5 |
| CVE-2023-32039 | Microsoft PostScript and PCL6 Class Printer Driver Information Disclosure Vulnerability | No | No | 5.5 |
| CVE-2023-32040 | Microsoft PostScript and PCL6 Class Printer Driver Information Disclosure Vulnerability | No | No | 5.5 |
| CVE-2023-35324 | Microsoft PostScript and PCL6 Class Printer Driver Information Disclosure Vulnerability | No | No | 5.5 |
| CVE-2023-32085 | Microsoft PostScript and PCL6 Class Printer Driver Information Disclosure Vulnerability | No | No | 5.5 |
| CVE-2023-35306 | Microsoft PostScript and PCL6 Class Printer Driver Information Disclosure Vulnerability | No | No | 5.5 |
Windows ESU vulnerabilities
| CVE | Title | Exploited? | Publicly disclosed? | CVSSv3 base score |
|---|---|---|---|---|
| CVE-2023-35365 | Windows Routing and Remote Access Service (RRAS) Remote Code Execution Vulnerability | No | No | 9.8 |
| CVE-2023-35366 | Windows Routing and Remote Access Service (RRAS) Remote Code Execution Vulnerability | No | No | 9.8 |
| CVE-2023-35367 | Windows Routing and Remote Access Service (RRAS) Remote Code Execution Vulnerability | No | No | 9.8 |
| CVE-2023-32057 | Microsoft Message Queuing Remote Code Execution Vulnerability | No | No | 9.8 |
| CVE-2023-35322 | Windows Deployment Services Remote Code Execution Vulnerability | No | No | 8.8 |
| CVE-2023-35303 | USB Audio Class System Driver Remote Code Execution Vulnerability | No | No | 8.8 |
| CVE-2023-35300 | Remote Procedure Call Runtime Remote Code Execution Vulnerability | No | No | 8.8 |
| CVE-2023-32038 | Microsoft ODBC Driver Remote Code Execution Vulnerability | No | No | 8.8 |
| CVE-2023-35328 | Windows Transaction Manager Elevation of Privilege Vulnerability | No | No | 7.8 |
| CVE-2023-33154 | Windows Partition Management Driver Elevation of Privilege Vulnerability | No | No | 7.8 |
| CVE-2023-32046 | Windows MSHTML Platform Elevation of Privilege Vulnerability | Yes | No | 7.8 |
| CVE-2023-32053 | Windows Installer Elevation of Privilege Vulnerability | No | No | 7.8 |
| CVE-2023-35342 | Windows Image Acquisition Elevation of Privilege Vulnerability | No | No | 7.8 |
| CVE-2023-36874 | Windows Error Reporting Service Elevation of Privilege Vulnerability | Yes | No | 7.8 |
| CVE-2023-35299 | Windows Common Log File System Driver Elevation of Privilege Vulnerability | No | No | 7.8 |
| CVE-2023-35340 | Windows CNG Key Isolation Service Elevation of Privilege Vulnerability | No | No | 7.8 |
| CVE-2023-35312 | Microsoft VOLSNAP.SYS Elevation of Privilege Vulnerability | No | No | 7.8 |
| CVE-2023-35297 | Windows Pragmatic General Multicast (PGM) Remote Code Execution Vulnerability | No | No | 7.5 |
| CVE-2023-35338 | Windows Peer Name Resolution Protocol Denial of Service Vulnerability | No | No | 7.5 |
| CVE-2023-33163 | Windows Network Load Balancing Remote Code Execution Vulnerability | No | No | 7.5 |
| CVE-2023-35330 | Windows Extended Negotiation Denial of Service Vulnerability | No | No | 7.5 |
| CVE-2023-35309 | Microsoft Message Queuing Remote Code Execution Vulnerability | No | No | 7.5 |
| CVE-2023-32044 | Microsoft Message Queuing Denial of Service Vulnerability | No | No | 7.5 |
| CVE-2023-32045 | Microsoft Message Queuing Denial of Service Vulnerability | No | No | 7.5 |
| CVE-2023-21526 | Windows Netlogon Information Disclosure Vulnerability | No | No | 7.4 |
| CVE-2023-32054 | Volume Shadow Copy Elevation of Privilege Vulnerability | No | No | 7.3 |
| CVE-2023-35350 | Windows Active Directory Certificate Services (AD CS) Remote Code Execution Vulnerability | No | No | 7.2 |
| CVE-2023-32043 | Windows Remote Desktop Security Feature Bypass Vulnerability | No | No | 6.8 |
| CVE-2023-35332 | Windows Remote Desktop Protocol Security Feature Bypass | No | No | 6.8 |
| CVE-2023-32055 | Active Template Library Elevation of Privilege Vulnerability | No | No | 6.7 |
| CVE-2023-35344 | Windows DNS Server Remote Code Execution Vulnerability | No | No | 6.6 |
| CVE-2023-35345 | Windows DNS Server Remote Code Execution Vulnerability | No | No | 6.6 |
| CVE-2023-35346 | Windows DNS Server Remote Code Execution Vulnerability | No | No | 6.6 |
| CVE-2023-35310 | Windows DNS Server Remote Code Execution Vulnerability | No | No | 6.6 |
| CVE-2023-35351 | Windows Active Directory Certificate Services (AD CS) Remote Code Execution Vulnerability | No | No | 6.6 |
| CVE-2023-32033 | Microsoft Failover Cluster Remote Code Execution Vulnerability | No | No | 6.6 |
| CVE-2023-35321 | Windows Deployment Services Denial of Service Vulnerability | No | No | 6.5 |
| CVE-2023-35316 | Remote Procedure Call Runtime Information Disclosure Vulnerability | No | No | 6.5 |
| CVE-2023-33166 | Remote Procedure Call Runtime Denial of Service Vulnerability | No | No | 6.5 |
| CVE-2023-33167 | Remote Procedure Call Runtime Denial of Service Vulnerability | No | No | 6.5 |
| CVE-2023-33168 | Remote Procedure Call Runtime Denial of Service Vulnerability | No | No | 6.5 |
| CVE-2023-33169 | Remote Procedure Call Runtime Denial of Service Vulnerability | No | No | 6.5 |
| CVE-2023-33172 | Remote Procedure Call Runtime Denial of Service Vulnerability | No | No | 6.5 |
| CVE-2023-33173 | Remote Procedure Call Runtime Denial of Service Vulnerability | No | No | 6.5 |
| CVE-2023-32034 | Remote Procedure Call Runtime Denial of Service Vulnerability | No | No | 6.5 |
| CVE-2023-32035 | Remote Procedure Call Runtime Denial of Service Vulnerability | No | No | 6.5 |
| CVE-2023-35314 | Remote Procedure Call Runtime Denial of Service Vulnerability | No | No | 6.5 |
| CVE-2023-35318 | Remote Procedure Call Runtime Denial of Service Vulnerability | No | No | 6.5 |
| CVE-2023-35319 | Remote Procedure Call Runtime Denial of Service Vulnerability | No | No | 6.5 |
| CVE-2023-33164 | Remote Procedure Call Runtime Denial of Service Vulnerability | No | No | 6.5 |
| CVE-2023-32042 | OLE Automation Information Disclosure Vulnerability | No | No | 6.5 |
| CVE-2023-35341 | Microsoft DirectMusic Information Disclosure Vulnerability | No | No | 6.2 |
| CVE-2023-33174 | Windows Cryptographic Information Disclosure Vulnerability | No | No | 5.5 |
Download Rapid7's Annual Vulnerability Intelligence Report ▶︎

