When we talk to Metasploit users, they usually use it for either penetration testing, password auditing or vulnerability validation, but few use it for more than one of these purposes. By leveraging your investment in Metasploit, you can triple-dip at the same price - no extra licenses needed.
Penetration Testing
With penetration testing, you can identify issues in your security infrastructure that could lead to a data breach. Weaknesses you can identify include exploitable vulnerabilities, weak or shared passwords, vulnerable web applications, and low security awareness among your staff. Typically, penetration tests are set up as projects, although companies are starting to adopt penetration testing as a program to:
- Regularly assess the security of their infrastructure
- Test the security of new applications and systems before roll-out
- Re-test the security of systems after major changes
Password Auditing
Adding password auditing to your security program can really help you lower the risk of a data breach. By regularly scanning your network, Metasploit's brute forcing function can help you identify the following issues:
- Weak passwords that lack length or complexity
- Passwords contained in dictionaries
- Passwords that are easily guessed based on information about the infrastructure
- Vendor default passwords
- Replaying cached credentials
- Re-use of passwords across trust zones
- Development test credentials in a production environment
- Active accounts of previous employees
Vulnerability Validation
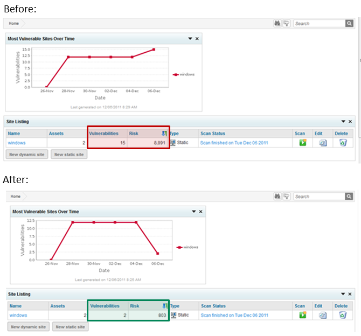
This is a lesser-known use case for Metasploit, but a very powerful one if used right. Vulnerability scanners can typically only detect if a vulnerable version of an application or operating system is installed on a system. However, not all vulnerabilities are exploitable, and only exploitable vulnerabilities can lead to a data breach. If you don't know which vulnerabilities put the company's data at risk, you have to fix all vulnerabilities. If you have ever read the long reports of vulnerability scanners, you know this is a daunting and audacious task. Most companies don't have the resouces to ever close this list out.
With Metasploit, you can validate whether a vulnerability is in fact exploitable. You should focus on remediating these vulnerabilities, and can safely ignore the vulnerabilities that cannot be exploited. After you have remediated an exploitable vulnerability, use Metasploit as your litmus test to see if it is now no longer exploitable. Metasploit can import the vulnerability scanning reports from all major vulnerability scanners, so you can leverage your existing infrastructure and investment.
While penetration testing and password auditing will increase the security of your infrastructure as a type of "security quality assurance", vulnerability validation is a tool that helps you reduce the workload of your security team and focus on issues that really matter.
If you're interested in testing out Metasploit Pro for either penetration testing or vulnerability validation, download a free trial now.