This month, a security researcher disclosed that a version of the old banking Trojan “Trojan.ibank” has been modified to look for SAP GUI installations, a concerning sign that SAP system hacking has gone into mainstream cybercrime. Once a domain of a few isolated APT attacks, SAP appears to be in the cross hairs of hackers that know just how much sensitive data ERP systems house, including financial, customer, employee and production data. With more than 248,500 customers in 188 countries, SAP may see an increase of attacks and their customers face the threat of data theft, fraud and sabotage.
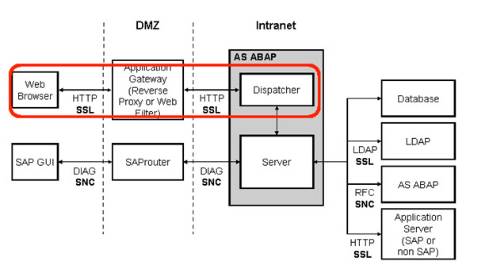
This trend is not really surprising, given that financial, customer, employee and production data reside in a company's enterprise resource planning (ERP) systems—and they are juicy targets for all sorts of malicious hackers. What's worse, these systems have often organically grown over decades and are so complex that few people understand their organization's entire ecosystem, let alone some of SAP's protocols and components that are not publically documented. If you are a security professional responsible for security audits, you may want to download Rapid7's new free research paper on conducting penetration tests on SAP systems.
Organized cyber-crime often looks for credit card numbers contained in business transaction data, which they use to conduct fraudulent transactions. They can extract social security numbers in an employee database to conduct identity theft. By changing the payee account details in the system, they can redirect funds into their own accounts and go home with a hefty paycheck.
But cyber-crime is not the only player to worry about. State-sponsored hacking groups regularly break into enterprises for purposes of industrial espionage. ERP systems provide them with a wealth of data to pass on to their domestic industry – as well as a chance to sabotage production flows and financial data. As a result, mergers and acquisitions may fall through or foreign competitors may get a head start on copying the latest technology.
SAP is the market leader for ERP systems with more than 248,500 customers in 188 countries. In collaboration with its community contributors, Rapid7's security researchers have published a research report on how attackers may use vulnerabilities in SAP systems to get to a company's innermost secrets. The research report gives an overview of key SAP components, explores how you can map out the system before an attack, and gives step-by-step examples on how to exploit vulnerabilities and brute-force logins. These methods have been implemented and published in the form of more than 50 modules for Metasploit, a free, open source software for penetration testing. The modules enable companies to test whether their own systems could be penetrated by an attacker.
Many attackers will try to gain access to SAP systems by pivoting through a host on a target network, for example after compromising a desktop system through a spear phishing email. However, Rapid7 researchers found close to 3,000 SAP systems directly exposed to the Internet providing direct access to attackers.
Rapid7 security researcher Juan Vazquez has published a technical research paper summarizing the vast body of work published by security researchers and himself, many of them Metasploit open source contributors who are credited throughout the paper. The research paper is a practical, technical overview of the various SAP systems and protocols as well as over 50 Metasploit modules that can be leveraged for pentesting SAP solutions. Get your free research paper now “SAP Penetration Testing Using Metasploit - How to Protect Sensitive ERP Data”