Not having visibility can be dangerous in many situations. The new Metasploit 4.8 gives you better visibility in four key areas:
- View phishing exposure in the context of the overall user risk
- See which vulnerabilities pose the biggest risk to your organization
- Have all host information at your fingertips when doing a pentest
- Discover the latest risks on your network with new exploits and other modules
See Phishing Exposure as One Factor of User Risk
Users are often a weak part of the security chain, exposing organizations to attacks. This has led to a change in attacker methodology from brute force system-based attacks to deception-oriented attacks. Especially phishing has seen a rise in recent years. Many organizations already conduct end-user trainings but find it challenging to determine how vulnerable their users really are and which users pose the largest risk.
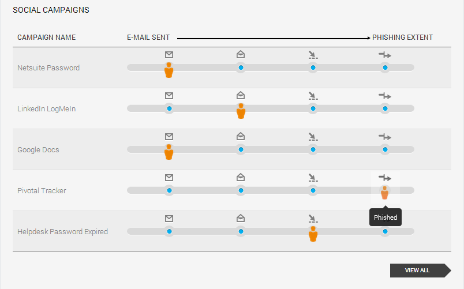
Rapid7 Metasploit Pro measures the effectiveness of security awareness trainings by running simulated phishing campaigns and integrates with Rapid7 UserInsight to provide this information in the context of a more comprehensive user risk, including network access, cloud service usage, and compromised credentials.
What's new – the details:
- UserInsight can now pull phishing information through Metasploit Pro's Remote API
- UserInsight provides an overview of the current status of each user and incorporates the phishing risk into the overall user risk
- Security professional can see user awareness trending over time
Here is how this helps you:
- Clear picture of user risks: Security analysts get a quick and clear picture of a user's accounts, network activity, cloud services, mobile devices, network activity and now phishing in one place, unifying information normally scattered across systems.
- More effective security program: Tracking the effectiveness of security awareness trainings means you can adapt them to become more effective over time.
Metasploit Pro is the only phishing simulation solution that integrates with a solution to provide insight into user activity and risk. Unlike alternative penetration testing solutions, Metasploit Pro's social engineering reports provides conversion rates at each step in the campaign funnel, such as how many people clicked through a phishing email, how many entered username and password on a fake website, and how many systems were compromised. Only Metasploit provides advice on how to address risk at each step in the social engineering funnel.
While some phishing simulation services can only measure user awareness, Metasploit Pro can also measure the effectiveness of technical controls. If desired, phishing web pages or email attachments can contain exploits that test patch levels, security configurations, and network-based defenses.
Simulated phishing campaigns are exclusive to Metasploit Pro users.
See which vulnerabilities pose the biggest risk to your organization
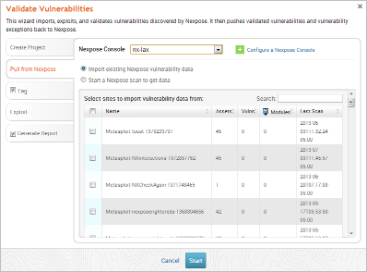
Vulnerability validation helps you to determine if a vulnerability poses a high risk to your environment. It focuses on vulnerabilities with known public exploits that provide an easy way into your network - even for less experienced attackers.
Metasploit Pro simplifies and expedites vulnerability validation. It provides a unified, guided interface, called the Vulnerability Validation Wizard, that walks you through each step of the vulnerability validation process - from importing Nexpose data to auto-exploiting vulnerabilities to sending the validation results back to Nexpose. You can even define exceptions for vulnerabilities that were not successfully exploited.
Nexpose and Metasploit Pro seamlessly integrate to streamline the vulnerability validation workflow. It creates a closed-loop security risk assessment solution so that you can find potential vulnerabilities, exploit them, and identify the security flaws that pose a real threat to a network.
After vulnerabilities have been validated, the results are returned to Nexpose, where exploitability of a vulnerability can be used to create reports and prioritize vulnerabilities for remediation.
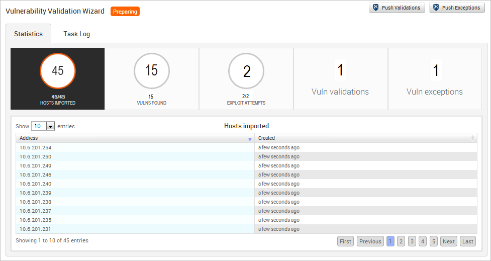
What's new – the details:
- Metasploit added a vulnerability validation wizard, greatly simplifying the vulnerability validation process.
- Exploited vulnerabilities are now marked in Nexpose with a special icon,
- Nexpose users can create a dynamic asset group containing validated vulnerabilities, making it easy to see how many machines fall into that group and enabling reporting and trending,
- Nexpose users can now filter by exploited vulnerabilities and create top remediations reports that provide clear instructions for the IT teams.
- Vulnerabilities discovered by Metasploit that were not part of the original Nexpose import are marked with a green “New” flag.
- Clear status next to each vulnerability in Metasploit on whether the vulnerability could be exploited.
- Faster and more robust import of vulnerability scans from Nexpose and third-party scanners
Here is how this helps you:
- Reduced cost: Focusing on prioritized, high-risk vulnerabilities reduces the workload of the remediation team.
- Higher security assurance: Knowing which vulnerabilities pose a high risk and addressing them first reduces the likelihood that an attacker can get in.
- Higher credibility: Provide proof of exploitability to application owners to elevate the remediation discussion to an objective level
Only Rapid7 offers closed-loop vulnerability validation, returning information about successful validations and vulnerability exceptions into the vulnerability management solution for easy remediation, reporting, and trending.
Unlike other solutions, that require a manual XML export and import of vulnerability data, Metasploit Pro can pull existing scan data directly from Nexpose, through a supported API.
Closed-loop vulnerability validation is exclusive to Metasploit Pro users.
If you're interested to hear more about vulnerability validation and see a live demo, join our free webcast "Don't Trust, Validate! How to Determine the Real Risk of Your Vulnerabilities."
Have all host information at your fingertips when doing a pentest
While penetration testers are used to bending technology to suit their needs, solving difficult tasks is not an end it itself. Especially in large penetration tests, it can be challenging to manage a lot of data efficiently and without losing the overview. These difficulties can quickly cause longer work hours and overdue projects.
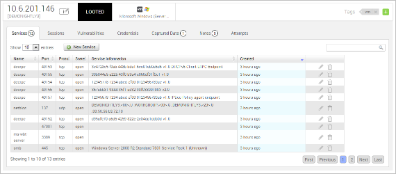
Metasploit Pro makes it easier to carry out standard tasks and to manage the vast amount of information collected during a penetration test. This directly translates into time savings and a reduced training need for new staff. For example, Metasploit Pro manages data by tracking active projects, importing results from other sources, and now allowing manual input.
What's new – the details:
- Overhauled usability of the single host view, the most used screen in Metasploit Pro, to provide all important data at a glance.
- New screen includes counts/stats for services, vulnerabilities, notes, credentials, captured data, file shares, exploit attempts, and matched modules.
- Pentesters can now manually add services, vulnerabilities, credentials, and captured data files they have discovered outside of Metasploit.
Here is how this helps you:
- Reduced cost: Better usability means shorter project times, lower cost, and reduced training needs for new staff
Metasploit Pro makes it much easier than Metasploit Framework to handle large penetration tests and bring new staff on board.
The new single host view is available in Metasploit Community, Metasploit Express, and Metasploit Pro.
128 New Modules in Metasploit 4.8.0: Routers, HP Enterprise Software, and Awesome Payloads
First off, we have 128 new modules since 4.7's release back in July (and you get bonus secgeek points if that count makes you a little nervous). That comes in at just about one and a half new modules a day, every day, since July 15. These modules are all over the place, since most of them come in unannounced to be cleaned up and put to work like so many Dickensian orphans. However, some themes did shake out with what we pursued in exploit-land for this release.
We have eight new modules targeting SOHO routers and access points, from Michael Messner, Craig Heffner, Brandon Perry, and Juan Vazquez. SOHO router hacking has been a focus for Metasploit for about a year now, and we're still championing the idea that if you have work-from-home employees, or even high-priority targets like the CFO's laptop, SOHO routers like these should be in scope for your engagement. It's a discussion worth having, and the availability of Metasploit modules can help a penetration tester make his case.
There are 24 new modules that exploit ZDI-disclosed vulnerabilities, 20 of which saw a bunch of work from Juan Vazquez, who I swear doesn't have it in for HP. It just so happens that over half of these ZDI vulns are targeting HP enterprise server software, including StorageWorks, LoadRunner, IMC, and Procurve Manager. ZDI bugs are great targets for exploit developers, because they represent popular software that you're likely to find in the enterprise, so penetration testers get a lot of mileage out of these.
This release was unique among most in that there are some really neat new payloads; we now have new shell bind and reverse shell payloads in Lua and Node.js from xistence and Joe Vennix, respectively. These go along with our usual bash, VBS, Perl, Python, and assorted other language shells. If your client's IDS/IPS/AV vendor isn't paying attention, these new shell spawners might slip past their tried-and-true defenses. That said, I have to say that the most exciting new payload is a Python implementation of Meterpreter from Spencer McIntyre. This brings more Meterpreter functionality to pretty much any standard Linux build, and is getting much more active development than our old C-based POSIX Meterpreter.
Oh, yes, and there's good old Windows Meterpreter. We've made huge improvements there, thanks to some phenomenal focused effort from OJ "TheColonial" Reeves. OJ has brought Meterpreter (sometimes kicking and screaming) to the modern era of C development, with a completely revamped build environment (using the free edition of Microsoft Visual Studio 2013) and continuous integration platform. Along the way, he smashed a huge pile of bugs and annoyances, both internally and externally reported. What this all means to users is that Meterpreter is slightly smaller and *much* more stable now, *and* it's totally amenable to open source C development. The days of having to incorporate every change with the tribal knowledge of James "Egypt" Lee and HD Moore are pretty much over.
For exploit developers, we have a bunch of new brand new libraries for use: FireFart's WordPress manipulation API makes WP-specific assessments much easier, and Meatballs' WDSCP protocol library takes advantage of insecure Windows Deployment Services (are there any other kind?) to get a quick foothold in a WDS-imaged enterprise. Meatballs also contributed a handful of new binary templates for use with payload generation, including templates for PowerShell, VBA, MSI installers, and more, all of which complicate Metasploit's relationship with the various anti-virus vendors.
Of course, that's not all, but those are the headline features for Metasploit Framework 4.8.0. We landed over 2,300 commits since mid-July; the summary above and the modules below represent the most visible changes. But with nearly a hundred non-Rapid7 people who got commits into the master repository for Metasploit Framework, it's really pretty impossible to give a complete rundown of every cool new thing that hit; for that, you can start by looking at the last four or five months' worth of blog posts, or even better, peruse the git shortlog (from your nearest git clone, type 'git shortlog 4.7.0...4.8.0').
So, thanks to all the volunteers listed below for all your commits (and commitment!) to our collective open source security product, sorted by commit count, then alphabetically by first name or handle. You guys make Metasploit go.
Meatballs1, FireFart, jiuweigui, Spencer McIntyre, m-1-k-3, several people calling themselves "root" (fix your .gitconfig, guys!), Nathan Einwechter, xistence, Rick Flores, Karn Ganeshen, MrXors, AverageSecurityGuy, Ramon de C Valle, Markus Wulftange, kaospunk, dummys, Bruno Morisson, RageLtMan, mubix, g0tmi1k, darknight007, bcoles, TecR0c, shellster, Charlie Eriksen, Rich Lundeen, Boris, bmerinofe, joernchen of Phenoelit, jgor, jamcut, ZeroChaos, trustedsec, Shelby Spencer, Sean Verity, Patrick Webster, Dhiru Kholia, ddouhine, Davy Douhine, Alexandre Maloteaux, Tyler Krpata, swtornio, Stephen Haywood, Ryan Wincey, Norbert Szetei, Nicholas Davis, kernelsmith, h0ng10, Frederic Basse, Daniele Martini, Brandon Perry, Brandon Knight, Winterspite, Vlatko Kosturjak, violet, tkrpata, Till Maas, scriptjunkie, Sagi Shahar, Ruslaideemin, Rick Flores, rbsec, pyoor, Paul, nmonkee, MosDefAssassin, Matt Andreko, Juushya, Joshua J. Drake, Jon Hart, Jonathan Rudenberg, Joff Thyer, Joe Barrett, Icewall, Henrik Kentsson, ethicalhack3r, Darren Martyn, corelanc0d3er, Borja Merino, Booboule, allfro, and Alexia Cole.
New modules since 4.7.0:
Exploit modules
- Astium Remote Code Execution by xistence exploits OSVDB-88860
- D-Link Devices Unauthenticated Remote Command Execution by juan vazquez and Michael Messner exploits OSVDB-89861
- D-Link Devices Unauthenticated Remote Command Execution by juan vazquez and Michael Messner exploits OSVDB-92698
- D-Link DIR-605L Captcha Handling Buffer Overflow by juan vazquez and Craig Heffner exploits OSVDB-86824
- D-Link Devices UPnP SOAP Command Execution by juan vazquez and Michael Messner exploits OSVDB-94924
- D-Link Devices UPnP SOAP Telnetd Command Execution by juan vazquez and Michael Messner exploits OSVDB-94924
- Foreman (Red Hat OpenStack/Satellite) bookmarks/create Code Injection by Ramon de C Valle exploits CVE-2013-2121
- Linksys WRT110 Remote Command Execution by juan vazquez, Craig Young, and joev exploits CVE-2013-3568
- PineApp Mail-SeCure ldapsyncnow.php Arbitrary Command Execution by juan vazquez and Dave Weinstein exploits ZDI-13-185
- PineApp Mail-SeCure livelog.html Arbitrary Command Execution by juan vazquez and Unknown exploits ZDI-13-184
- PineApp Mail-SeCure test_li_connection.php Arbitrary Command Execution by juan vazquez and Dave Weinstein exploits ZDI-13-188
- Raidsonic NAS Devices Unauthenticated Remote Command Execution by juan vazquez and Michael Messner exploits OSVDB-90221
- Sophos Web Protection Appliance sblistpack Arbitrary Command Execution by juan vazquez and Francisco Falcon exploits CVE-2013-4983
- Zabbix 2.0.8 SQL Injection and Remote Code Execution by Jason Kratzer and Lincoln exploits CVE-2013-5743
- Sophos Web Protection Appliance clear_keys.pl Local Privilege Escalation by juan vazquez and Francisco Falcon exploits CVE-2013-4984
- VMWare Setuid vmware-mount Unsafe popen(3) by egyp7 and Tavis Ormandy exploits CVE-2013-1662
- HP StorageWorks P4000 Virtual SAN Appliance Login Buffer Overflow by juan vazquez and e6af8de8b1d4b2b6d5ba2610cbf9cd38 exploits ZDI-13-179
- Java storeImageArray() Invalid Array Indexing Vulnerability by sinn3r, juan vazquez, and Unknown exploits CVE-2013-2465
- Nodejs js-yaml load() Code Execution by Neal Poole and joev exploits CVE-2013-4660
- GestioIP Remote Command Execution by bperry
- GLPI install.php Remote Command Execution by Tristan Leiter exploits CVE-2013-5696
- HP System Management Homepage JustGetSNMPQueue Command Injection by sinn3r and Markus Wulftange exploits CVE-2013-3576
- VMware Hyperic HQ Groovy Script-Console Java Execution by Brendan Coles
- ISPConfig Authenticated Arbitrary PHP Code Execution by Brandon Perry exploits CVE-2013-3629
- Linksys WRT110 Remote Command Execution by juan vazquez, Craig Young, and joev exploits CVE-2013-3568
- Moodle Remote Command Execution by Brandon Perry exploits CVE-2013-3630
- NAS4Free Arbitrary Remote Code Execution by Brandon Perry exploits CVE-2013-3631
- OpenMediaVault Cron Remote Command Execution by Brandon Perry exploits CVE-2013-3632
- OpenX Backdoor PHP Code Execution by egyp7 and Unknown exploits CVE-2013-4211
- ProcessMaker Open Source Authenticated PHP Code Execution by Brendan Coles
- Ruby on Rails Known Secret Session Cookie Remote Code Execution by joernchen of Phenoelit
- Apache Struts 2 DefaultActionMapper Prefixes OGNL Code Execution by sinn3r, juan vazquez, and Takeshi Terada exploits CVE-2013-2251
- >vTigerCRM v5.4.0/v5.3.0 Authenticated Remote Code Execution by Brandon Perry exploits CVE-2013-3591
- Zabbix Authenticated Remote Command Execution by Brandon Perry exploits CVE-2013-3628
- Mac OS X Persistent Payload Installer by Marcin 'Icewall' Noga and joev
- >Mac OS X Sudo Password Bypass by juan vazquez, Todd C. Miller, and joev exploits CVE-2013-1775
- Western Digital Arkeia Remote Code Execution by xistence exploits OSVDB-97615
- ClipBucket Remote Code Execution by Gabby and xistence
- FlashChat Arbitrary File Upload by Brendan Coles and x-hayben21 exploits OSVDB-98233
- Graphite Web Unsafe Pickle Handling by Charlie Eriksen exploits CVE-2013-5093
- Joomla Media Manager File Upload Vulnerability by juan vazquez and Jens Hinrichsen exploits CVE-2013-5576
- Open Flash Chart v2 Arbitrary File Upload by Braeden Thomas, Brendan Coles, Gjoko Krstic, and Halim Cruzito exploits CVE-2009-4140
- OpenEMR 4.1.1 Patch 14 SQLi Privilege Escalation Remote Code Execution by xistence exploits OSVDB-97482
- SPIP connect Parameter PHP Injection by Arnaud Pachot, Davy Douhine, and Frederic Cikala exploits OSVDB-83543
- Squash YAML Code Execution by Charlie Eriksen exploits CVE-2013-5036
- VICIdial Manager Send OS Command Injection by sinn3r, juan vazquez, Adam Caudill, and AverageSecurityGuy exploits CVE-2013-4468
- WebTester 5.x Command Execution by Brendan Coles
- ZeroShell Remote Code Execution by Yann CAM and xistence
- CA BrightStor ARCserve Tape Engine 0x8A Buffer Overflow by MC exploits OSVDB-68330
- Apple Quicktime 7 Invalid Atom Length Buffer Overflow by sinn3r, Jason Kratzer, Paul Bates, and Tom Gallagher exploits ZDI-13-110
- HP LoadRunner lrFileIOService ActiveX Remote Code Execution by juan vazquez and rgod exploits ZDI-13-182
- HP LoadRunner lrFileIOService ActiveX WriteFileString Remote Code Execution by juan vazquez and Brian Gorenc exploits ZDI-13-207
- Microsoft Internet Explorer SetMouseCapture Use-After-Free by sinn3r and Unknown exploits MS13-080
- Firefox onreadystatechange Event DocumentViewerImpl Use After Free by sinn3r, juan vazquez, Nils, Unknown, and w3bd3vil exploits CVE-2013-1690
- Firefox XMLSerializer Use After Free by juan vazquez and regenrecht exploits ZDI-13-006
- MS13-055 Microsoft Internet Explorer CAnchorElement Use-After-Free by sinn3r, Jose Antonio Vazquez Gonzalez, Orange Tsai, and Peter Vreugdenhil exploits MS13-055
- MS13-059 Microsoft Internet Explorer CFlatMarkupPointer Use-After-Free by sinn3r and corelanc0d3r exploits MS13-059
- MS13-069 Microsoft Internet Explorer CCaret Use-After-Free by sinn3r and corelanc0d3r exploits MS13-069
- MS13-080 Microsoft Internet Explorer CDisplayPointer Use-After-Free by sinn3r and Unknown exploits MS13-080
- Siemens Solid Edge ST4 SEListCtrlX ActiveX Remote Code Execution by juan vazquez and rgod exploits OSVDB-93696
- EMC Replication Manager Command Execution by Davy Douhine and Unknown exploits ZDI-11-061
- A-PDF WAV to MP3 v1.0.0 Buffer Overflow by Dr_IDE, d4rk-h4ck3r, and dookie exploits OSVDB-67241
- Apple Quicktime 7 Invalid Atom Length Buffer Overflow by sinn3r, Jason Kratzer, Paul Bates, and Tom Gallagher exploits ZDI-13-110
- Beetel Connection Manager NetConfig.ini Buffer Overflow by metacom and wvu exploits OSVDB-98714
- Chasys Draw IES Buffer Overflow by juan vazquez, Christopher Gabriel, Javier 'soez', and Longinos Recuero Bustos exploits CVE-2013-3928
- MS13-071 Microsoft Windows Theme File Handling Arbitrary Code Execution by juan vazquez and Eduardo Prado exploits MS13-071
- freeFTPd PASS Command Buffer Overflow by TecR0c and Wireghoul exploits OSVDB-96517
- Open-FTPD 1.2 Arbitrary File Upload by Brendan Coles and Serge Gorbunov exploits CVE-2010-2620
- PCMAN FTP Server Post-Authentication STOR Command Stack Buffer Overflow by Christian (Polunchis) Ramirez and Rick (nanotechz9l) Flores exploits OSVDB-94624
- Cogent DataHub HTTP Server Buffer Overflow by juan vazquez and rgod exploits ZDI-13-178
- HP Intelligent Management Center BIMS UploadServlet Directory Traversal by juan vazquez and rgod exploits ZDI-13-238
- HP Managed Printing Administration jobAcct Remote Command Execution by juan vazquez and Andrea Micalizzi exploits ZDI-11-352
- HP ProCurve Manager SNAC UpdateCertificatesServlet File Upload by juan vazquez and rgod exploits ZDI-13-225
- HP ProCurve Manager SNAC UpdateDomainControllerServlet File Upload by juan vazquez and rgod exploits ZDI-13-226
- HP SiteScope Remote Code Execution by juan vazquez and rgod exploits ZDI-13-205
- Intrasrv 1.0 Buffer Overflow by PsychoSpy and xis_one exploits OSVDB-94097
- MiniWeb (Build 300) Arbitrary File Upload by AkaStep and Brendan Coles exploits OSVDB-92200
- Oracle Endeca Server Remote Command Execution by juan vazquez and rgod exploits ZDI-13-190
- Ultra Mini HTTPD Stack Buffer Overflow by PsychoSpy and superkojiman exploits CVE-2013-5019
- VMware vCenter Chargeback Manager ImageUploadServlet Arbitrary File Upload by juan vazquez and Andrea Micalizzi exploits ZDI-13-147
- Agnitum Outpost Internet Security Local Privilege Escalation by juan vazquez and Ahmad Moghimi exploits OSVDB-96208
- IKE and AuthIP IPsec Keyring Modules Service (IKEEXT) Missing DLL by Ben Campbell
- MS13-005 HWND_BROADCAST Low to Medium Integrity Privilege Escalation by Axel Souchet, Ben Campbell, and Tavis Ormandy exploits MS13-005
- Persistent Payload in Windows Volume Shadow Copy by Jedediah Rodriguez
- >Windows Management Instrumentation (WMI) Remote Command Execution by Ben Campbell exploits CVE-1999-0504
- Symantec Altiris DS SQL Injection by 3v0lver and Brett Moore exploits ZDI-08-024
- HP Data Protector Cell Request Service Buffer Overflow by juan vazquez and e6af8de8b1d4b2b6d5ba2610cbf9cd38 exploits ZDI-13-130
- HP LoadRunner magentproc.exe Overflow by juan vazquez and Unknown exploits ZDI-13-169
- PowerShell Payload Web Delivery by Ben Campbell and Chris Campbell
- Interactive Graphical SCADA System Remote Command Injection by Luigi Auriemma and MC exploits CVE-2011-1566
Auxiliary and post modules
- HP Intelligent Management SOM Account Creation by juan vazquez and rgod exploits ZDI-13-240
- Foreman (Red Hat OpenStack/Satellite) users/create Mass Assignment by Ramon de C Valle exploits CVE-2013-2113
- Nexpose XXE Arbitrary File Read by Bojan Zdrnja, Brandon Perry, and Drazen Popovic
- Openbravo ERP XXE Arbitrary File Read by Brandon Perry exploits CVE-2013-3617
- Sophos Web Protection Appliance patience.cgi Directory Traversal by juan vazquez and Wolfgang Ettlingers exploits CVE-2013-2641
- vBulletin Administrator Account Creation by juan vazquez and Unknown exploits OSVDB-98370
- GE Proficy Cimplicity WebView substitute.bcl Directory Traversal by juan vazquez and Unknown exploits CVE-2013-0653
- SMB File Delete Utility by mubix
- SMB File Download Utility by mubix
- Node.js HTTP Pipelining Denial of Service by Marek Majkowski, joev, and titanous exploits CVE-2013-4450
- Samba read_nttrans_ea_list Integer Overflow by Jeremy Allison and dz_lnly exploits CVE-2013-4124
- HP ProCurve SNAC Domain Controller Credential Dumper by juan vazquez and rgod
- >Auxilliary Parser Windows Unattend Passwords by Ben Campbell
- Microsoft Windows Deployment Services Unattend Retrieval by Ben Campbell
- Cisco Ironport Bruteforce Login Utility by Karn Ganeshen
- DLink User-Agent Backdoor Scanner by juan vazquez, Craig Heffner, and Michael Messner
- HP Intelligent Management BIMS DownloadServlet Directory Traversal by juan vazquez and rgod exploits ZDI-13-239
- HP Intelligent Management SOM FileDownloadServlet Arbitrary Download by juan vazquez and rgod exploits ZDI-13-242
- Jenkins Enumeration by Jeff McCutchan
- Host Information Enumeration via NTLM Authentication by Brandon Knight
- Radware AppDirector Bruteforce Login Utility by Karn Ganeshen
- Sentry Switched CDU Bruteforce Login Utility by Karn Ganeshen
- Supermicro Onboard IPMI CGI Vulnerability Scanner by juan vazquez and hdm exploits CVE-2013-3623
- Supermicro Onboard IPMI Static SSL Certificate Scanner by juan vazquez and hdm exploits CVE-2013-3619
- Supermicro Onboard IPMI url_redirect.cgi Authenticated Directory Traversal by juan vazquez and hdm
- SAP Host Agent Information Disclosure by Bruno Morisson exploits CVE-2013-3319
- Gather eCryptfs Metadata by Dhiru Kholia
- CUPS 1.6.1 Root File Read by Jann Horn and joev exploits CVE-2012-5519
- Multi Gather Resolve Hosts by Ben Campbell
- OSX Capture Userspace Keylogger by joev
- OSX Password Prompt Spoof by Joff Thyer and joev
- OSX Manage Record Microphone by joev
- OSX Manage Webcam by joev
- Windows Single Sign On Credential Collector (Mimikatz) by Ben Campbell
- Windows Gather DNS Cache by Borja Merino
- Windows Gather Prefetch File Information by TJ Glad
- Windows Resolve Hosts by Ben Campbell
- Windows Manage Set Port Forwarding With PortProxy by Borja Merino
The new modules are available in all Metasploit editions, including Metasploit Pro, Metasploit Express, Metasploit Community, and Metasploit Framework.
And It's All Available Now
If you're new to Metasploit, you can get started by downloading Metasploit for Linux or Windows. If you're already tracking the bleeding-edge of Metasploit development, then these modules are but an msfupdate command away. For readers who prefer the packaged updates for Metasploit Community and Metasploit Pro, you'll be able to install the new hotness today when you check for updates through the Software Updates menu under Administration.
For additional details on what's changed and what's current, please see Brandont's most excellent release notes.