This is a vulnerability advisory for the HP SiteScope DNS Tool Command Injection vulnerability, made in accordance with Rapid7's disclosure policy.
Summary
Due to a problem with sanitizing user input, authenticated users of HP SiteScope running on Windows can execute arbitrary commands on affected platforms as the local SYSTEM account. While it is possible to set a password for the SiteScope application administrator, this is not enforced upon installation. Therefore, in default deployments, any user who can navigate to the SiteScope service may execute arbitrary commands on the underlying operating system. If a password is set, only authenticated users may do so, which is still an unexpected level of operating system access.
Product Description
HP SiteScope is an agentless application monitorting solution, provided by Hewlettt Packard to enterprise customers.
Credit
This issue was first discovered and reported by Kirk Hayes of Rapid7, Inc. and Charles Riggs of Knowledge Consulting Group.
Exploitation
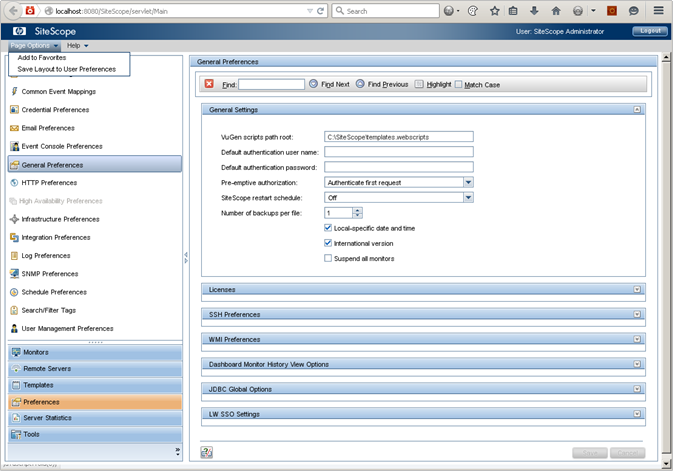
Navigating to:8080/SiteScope/servlet/Main will typically present any user with a control panel UI with the permissions of "SiteScope Administrator," as seen in the screenshot below.
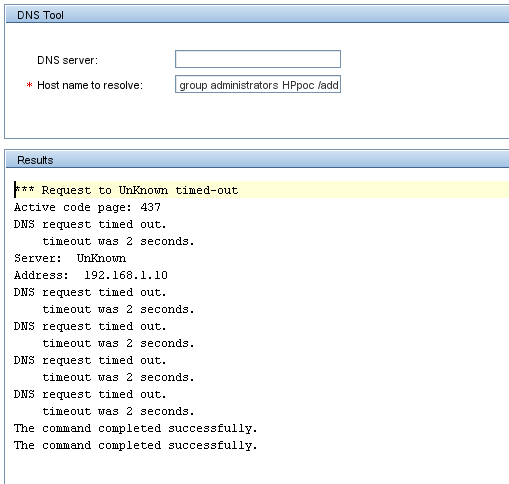
Once logged in, an attacker may navigate to the DNS Tool, found under Tools > Network Tools > DNS Tool, and enter any domain name for resolution in the Host name to resolve field, and append any other valid operating system command with the usual techniques. For example, attempting to resolve google.com & net user HPpoc QWERty1234 /ADD & net localgroup administrators HPpoc /ADD results in successfully creating a user and adding the user to the local administrators group, as seen in the screenshot below:
An attacker may similarly append any operating system command in the DNS Server field as well.
A Metasploit module has been published that demonstrates the issue.
Mitigations
In order to mitigate this issue, users should only grant access to the SiteScope application web services only to users who are trusted to local system access on the machine SiteScope is installed on. Of course, users are also strongly encouraged to set a strong password for all SiteScope users.
Alternatively, users should host SiteScope on Linux platforms, and configure SiteScope to run as a non-root user. This advice appears to be the preferred mitigation from the vendor per discussions between the vendor and Rapid7. On Windows, SiteScope appears to require local SYSTEM access in order to perform intended functionality, so account permissions for the application or individual users would not appear to be effective on this operating system.
Disclosure Timeline
In accordance with with Rapid7's disclosure policy, the vendor was made aware of this issue at least 60 days prior to this advisory's publication.
- Mon, Jun 01, 2015: Initial Discovery by Kirk Hayes and Charles Riggs
- Tue, Jun 02, 2015: Validated current version's vulnerability (v11.30)
- Thu, Jun 04, 2015: Offered to HP TippingPoint's ZDI program
- Tue, Jun 30, 2015: Rejected by ZDI
- Wed, Jul 01, 2015: Details disclosed to vendor, case # SSRT103139 assigned
- Wed, Aug 19, 2015: Issue receipt acknowledged by vendor, mitigation suggested
- Tue, Aug 25, 2015: Details disclosed to CERT
- Mon, Aug 31, 2015: CERT assigned VU#626368
- Fri, Oct 9, 2015: Public disclosure and Metasploit module published.
