If you’re a retailer, chances are you’ve already heard the buzz about Magecart, the online credit card-skimming malware that has hit multiple organizations and been reported on by other cybersecurity firms. Magecart is now a looming threat to nearly every retailer this Black Friday and throughout the rest of the holiday season (and beyond). While physical card skimming is still an issue—and will be for quite a while—Magecart is the first of its kind that can do so at scale by injecting itself into online checkout sites.
Since groups using Magecart have already been successful at stealing massive amounts of credit card data, we strongly recommend businesses, especially those with online checkouts, to take direct action to reduce risk. We’ve been analyzing Magecart since the emergence of chip-and-PIN cards, so in this post, we’ll explain why retailers struggle to get ahead of Magecart and provide two key ways to mitigate and reduce the risk of getting hit and impacted.
Why the Magecart malware attack is so tricky to detect
Unlike many opportunistic, commoditized threats, attack groups using Magecart have been careful to avoid detection. Designed to evade common detection techniques, some variants do not present themselves at every checkout, which is one reason it has often flown under the radar. It can be detected only if you’re actively looking at web browser content that’s loaded after encryption on the endpoint. And even if you do detect it, a customer may have already entered credit card and personal information, leaving them just as exposed.
How to detect Magecart
Even though Magecart is extremely difficult to detect, there are some indicators it's on the prowl and may be after your storefront’s customers. Some Magecart variants utilize weaponized versions of common "shopping-cart" portal software, so if you use popular, off-the-shelf e-commerce components, you may be in the “at-risk” category. Other variants will choose specific targets and profile their store/shopping process (commonly referred to as "crawling" your site). If they see you're using a third-party resource on key pages, they can use that knowledge to target that third-party site and compromise it to gain a surreptitious foothold in your checkout process.
In either scenario (targeted or common framework), the malicious JavaScript has some clever components in different variants. It tries to hide from prying eyes who use low-level browser tools to inspect what's going on. It knows from where you’re surfing and can use that to choose to stay hidden. Very clever variants evade web scanners and site-testing tools, and some utilize all the information a JavaScript component can scrape from a PC's environment to make sure it's safe to run. Once a Magecart instance determines the coast is clear, it shuts off personal information and account information to a third party as your customers complete the sale process, never realizing what has happened.
The quickest defense against the Magecart attack
Become an off-the-grid farmer—just kidding. Since that’s likely not in the cards for everyone and Black Friday is right around the corner, you need to find a way to address Magecart—and fast. Our biggest piece of advice is to narrow your scope and focus on locking down your checkout page. Since this is where your customers enter in the credit card data Magecart attackers want, this is the first place to focus your efforts.
Start by avoiding using any third-party JavaScript on any page where sensitive information is recorded or transmitted. This is typically how Magecart “wins.” However, if you absolutely need to use a third-party JavaScript resource on your sensitive checkout pages, be sure to follow these two steps:
1. Make sure you load the exact right domain resource
This means double- and triple-checking for typos in all components of the domain, as clever attackers register commonly misspelled domains and host malware there so they can execute the attack once a connection is made. Implement the most extensive QA tests on this page to be sure the domain resource is legitimate and exactly what you intended. We also recommend testing the page from several different physical/logical internet locations. Magecart is smart enough to know people will test this from company networks, so they won’t inject the code. You can be smarter than them by testing elsewhere.
2. Implement resource integrity.
Good, modern content delivery networks (CDNs), such as jQuery, provide integrity-check configurations when they tell you how to use a resource. Here’s a snippet of code they generate for you when you want to use a particular version of their library:
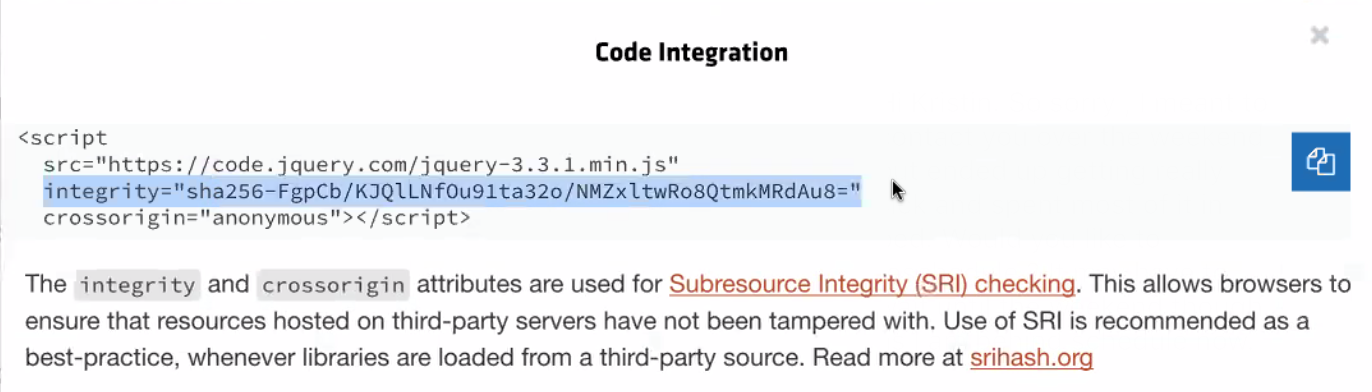
If you use jQuery in the checkout process, these two steps alone can stop Magecart from being successful.
While you should be wary of trusting a third-party online tool to generate SRI hashes for you, Report-URI is a reputable site that can also ease the process. Virtually all modern in-house web development stacks have the ability to generate these hashes for you, so check with your application development team before hitting a potentially sketch URL.
A longer-term fix is to be sure you’re using a reputable CDN and using SRI on all third-party resources. There are many CDNs out there today, but many don’t take security as seriously as they should (we know, you’re shocked). A lot of the news articles about Magecart focus on particular CDNs that are the issue, but shaming individual providers doesn’t solve anything. Investing in a CDN that prioritizes security and defaults to presenting embedding code with resource integrity fields (or has APIs to support this) will make Magecart much less likely to succeed.
What about the high rate of reinfection?
It’s true that one in five retailers get reinfected with Magecart in a matter of days. The biggest problem leading to reinfection is likely a lack of communication between security, IT, and operations teams during the remediation process. While a fix may have been made on the front end to thwart Magecart, we often see that the fix was done in-production and not back in development where it would have been integrated into all new content pushes. So, the same exact code gets pushed using the same malicious or compromised CDN, and your site is once again an unwitting partner in cybercrime.
The best way to prevent reinfection is to bring all of your content local and not use a CDN. That may be unrealistic for many reasons, so choosing a reputable CDN and using SRI is paramount.
Locking Magecart out
Magecart isn’t going away anytime soon, but if you can follow the simple mitigation techniques in this post, you can greatly reduce your risk of being hit during this busy shopping season. Down the road, we may see compliance standards such as PCI address this new Magecart vector head-on—in fact, there is language in the current standard that speaks to protecting against this kind of attack. In our view, it’s always better to opt in to these security best practices rather than having to implement them due to a regulation, so mitigation now will save you from more work down the line.
