Many thanks to Rapid7’s Emmett Kelly, Greg Wiseman, and Brent Cook for their assistance with the vulnerability research and this post.
Atlassian was notified in late February about a remote code execution (RCE) flaw in its Confluence and Data Center products and issued an alert with a patch on March 20, 2019. Organizations running versions between the following are impacted by this issue and should prioritize patching to mitigate damage from potential attackers:
- 6.6.0 ↔ 6.6.12
- 6.12.0 ↔ 6.12.3
- 6.13.0 ↔ 6.13.3
- 6.14.0 ↔ 6.14.2
The core issue lies in a server-side template injection weakness in a “Widget Connector” component. An attacker is able to exploit this weakness to achieve path traversal and RCE on impacted systems.
On April 10, 2019, a proof-of-concept (PoC) exploit for this vulnerability was released, along with a detailed explanation of the flaw.
Shortly after the PoC was made public, a pull request was filed with Rapid7’s Metasploit Framework.
On Friday, April 12, 2019, Rapid7’s InsightVM team provided full coverage for identifying vulnerable systems.
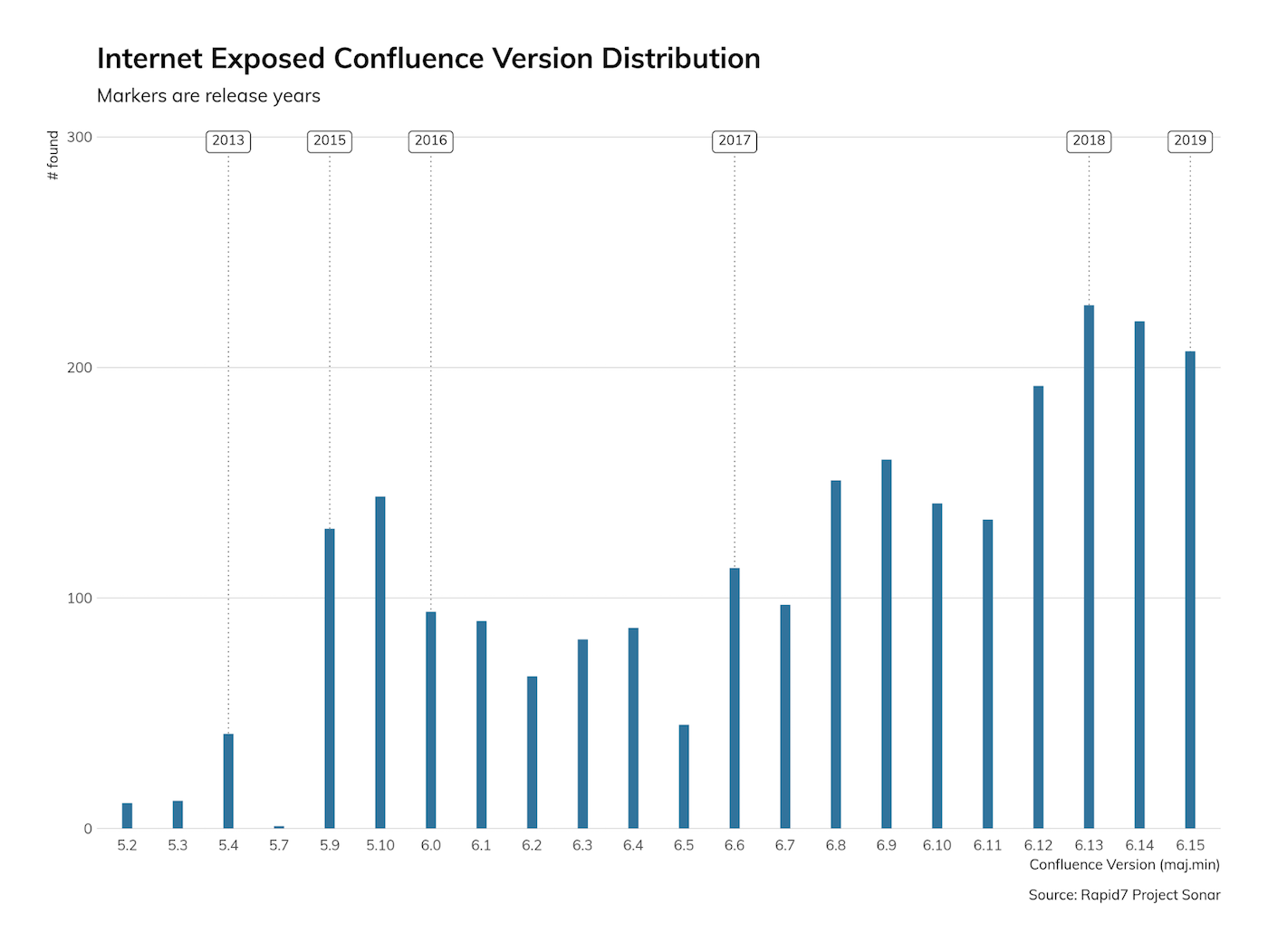
Rapid7 Labs’ Project Sonar discovered nearly 20,000 publicly exposed Confluence servers, as seen below, with over 2,500 being in the version ranges impacted by this vulnerability (however, sites running seriously older versions of Confluence have many other things to be worried about as well).
There has been no evidence in Rapid7 Labs’ Project Lorelei of active probing for this vulnerability as of the morning of Friday, April 12, 2019, but the Labs team will keep watching for activity and update this post if there is evidence of widespread attacker activity.
