We've provided quite a bit of information and education on WannaCry, Petya-like ransomware, and EternalBlue over the past two years. Rather than take a cue from a bad ‘80s sitcom and write a warbly-vision retrospective post, let's take a look at the current attacker landscape related to both EternalBlue and ransomware in general, along with some lessons that have clearly not been learned since the emergence of the exploits leaked by the Shadow Brokers. Don’t worry, though—we’ll close with a bit of hope for the future.
Do [they] really want to hurt [you]? (Hint: yes)
Depending on how you scan, where you scan from, and what you are trying to count when it comes to finding exposed Microsoft Windows Server Message Block (SMB) nodes on the internet, you'll get a number anywhere between 500,000 to 1 million. The range is due to whether you are an ethical internet scanner and obey opt-out requests and use well-identified scanner nodes (like Rapid7's Project Sonar) or whether you just cast ethics to the wind and find ways to cut corners and even use compromised devices to tally up an inventory.
Even though half a million or 1 million nodes seems like a big number, neither is truly accurate, since many regional internet service providers have blocked extranet access to the common service ports associated with Microsoft SMB since EternalBlue-based exploits became commonplace.
Regardless of the precise number, there are plenty of vulnerable nodes on the internet for attackers to practice against, with more appearing daily due to the advent of dynamic systems provisioning in cloud environments. And, practice they do:
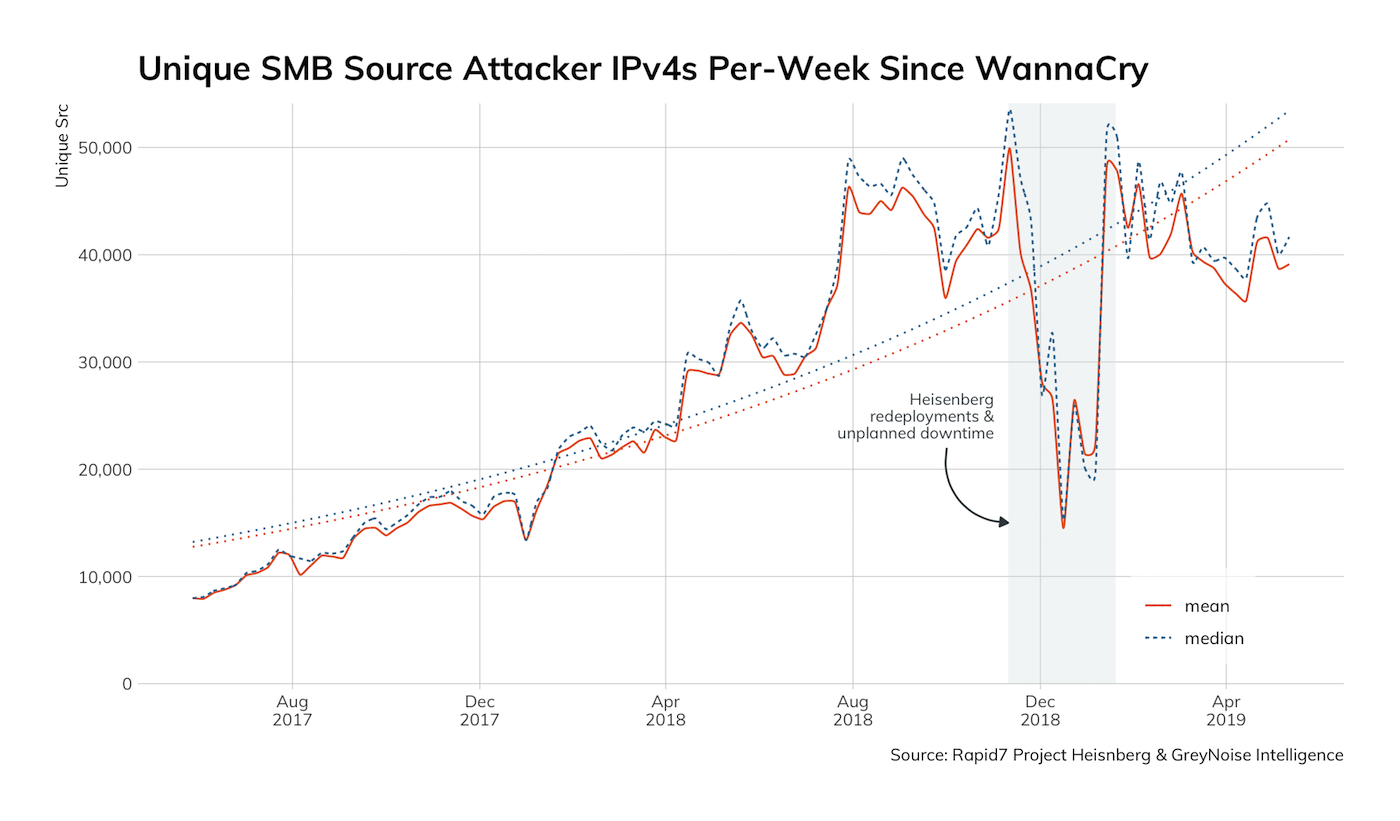
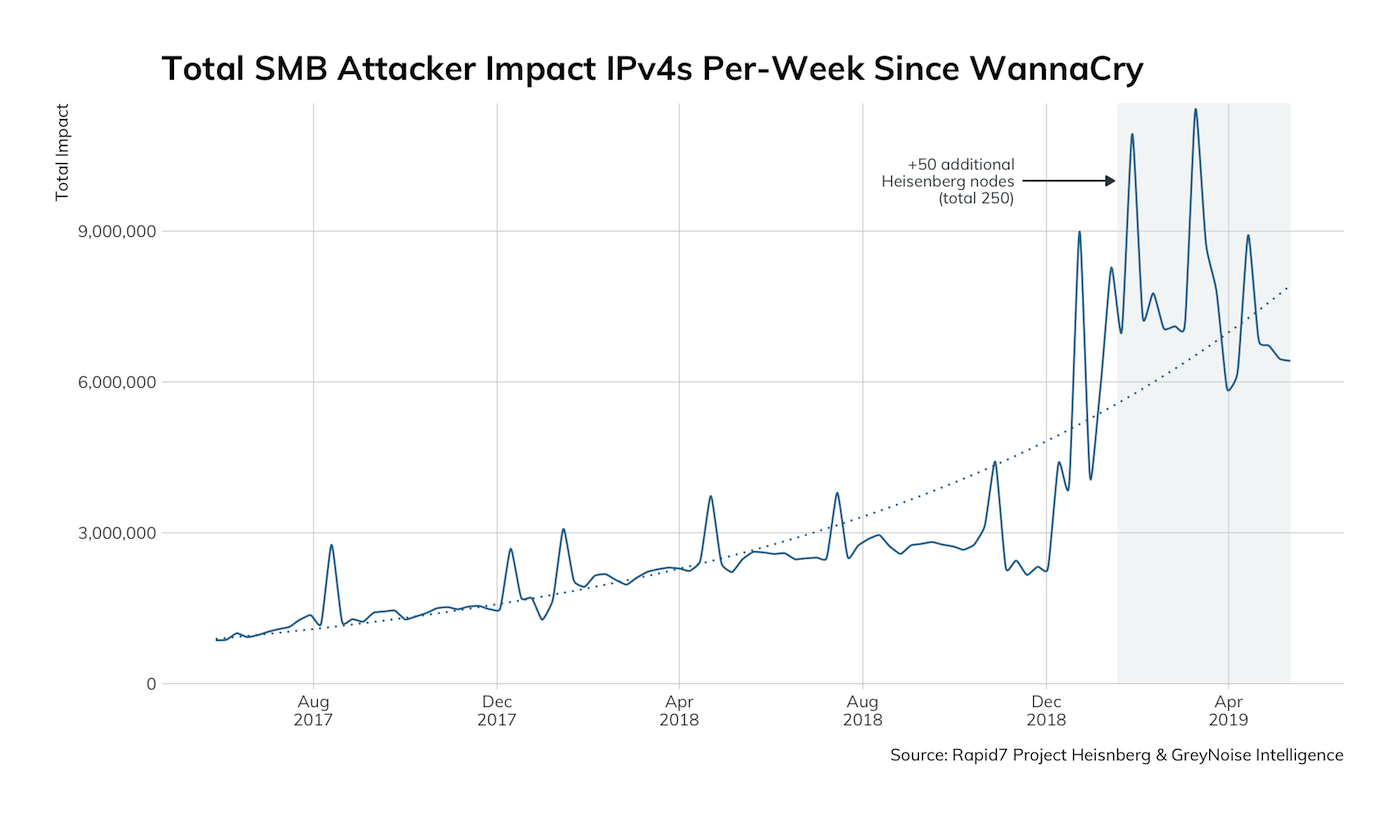
NOTE: The dip around December 2018 you see in the above figure is due to some rejiggering of our Project Lorelei nodes, and the significant elevation in daily totals in 2019 is due to Rapid Labs expanding from 150 to 250 honeypot nodes with a significantly larger presence in the southern hemisphere.
EternalBlue-based SMB probes and attacks are absolutely part of the "new normal" of background noise on the internet, with attackers—opportunistic or otherwise—testing out some form of their latest and greatest code and techniques with almost perfect immunity so they can have even more success once they gain a foothold in your organization.
Despite an overall upward trend (the dotted lines) for unique and total activity, there are a couple somewhat interesting observations in the Lorelei SMB charts. First, the increase in honeypot regional coverage did not result in the detection of more unique attacker sources—that is (thankfully), the attackers interested in SMB enumeration do not have infinite IPv4 capacity at their disposal.
To uncover the second notable observation, let's just focus on SMB attacker activity since January 2019:
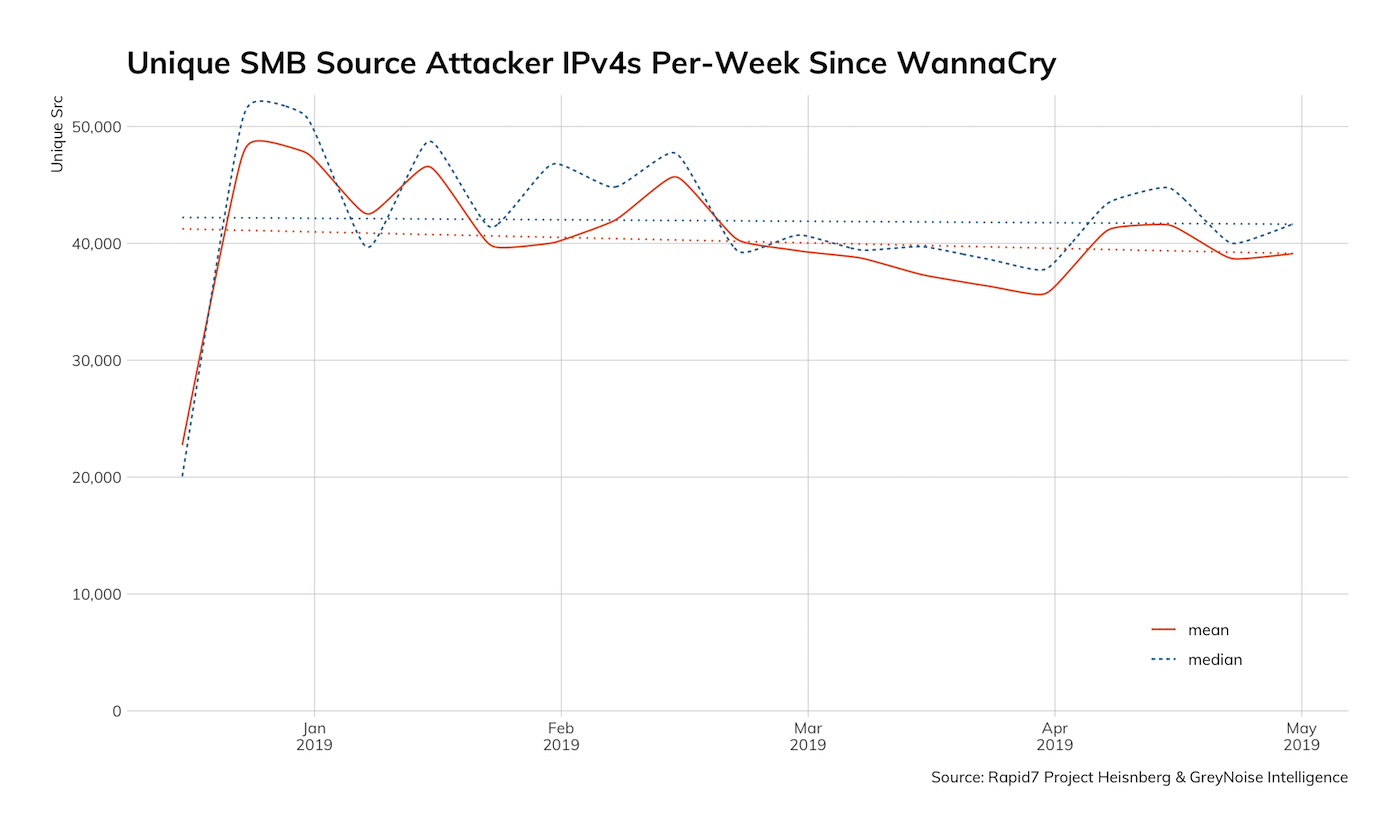
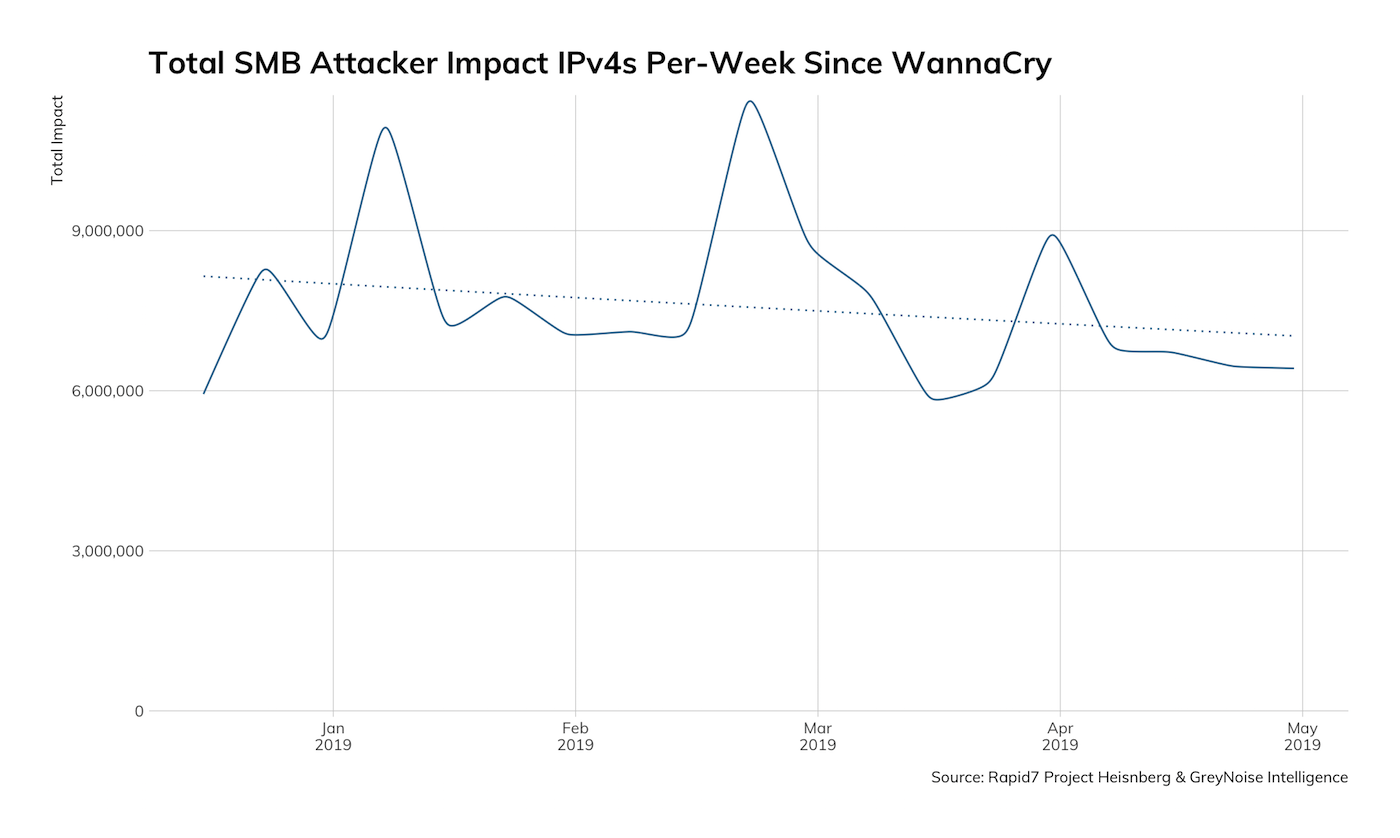
We're more than five months into the year, and the count-based trend is heading downward. Yes, that's right—there appears to be a diminishing focus on enumerating and compromising internet-facing SMB servers. If you're thinking, "So what? There's still quite a bit of traffic and it's a minor trend!" you should consider applying to one of the open positions in our Data Science team, since that is a great first,>Managed Detection and Response customers and will be sure to note any posits in future blog posts and quarterly threat reports.
Waking up with the house on fire (Ransomware is everywhere)
The popular internet security news aggregation site Bleeping Computer has a regular feature called "This Week in Ransomware." That should give you some idea of how prevalent this topic and threat tactic is. WannaCry and NotPetya were built as attack tools that use EternalBlue components to accomplish their goals. Despite this being a "WannaCry retrospective," the truth is that ransomware comes in many shapes and sizes and has not gone away despite many pundits diminishing this threat vector all throughout 2018. One big reason for the quantifiable reduction in ransomware attacks can be inferred from this Bitcoin price chart from CoinMarketCap:
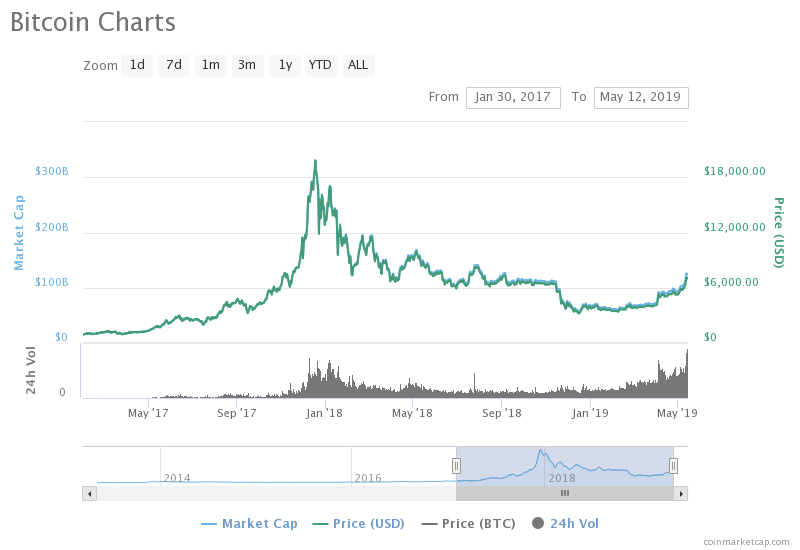
Ransoms are generally tied to digital currency and most digital currencies ebb and flow with Bitcoin's price. So, when a given currency market is bottoming out, it doesn't make much sense to try to gain illicit funds that way, especially using a technique that generally requires a decent amount of human interaction and support infrastructure.
As prices have stabilized and even begun to take on an upward trend, there is a renewed focus on this attack vector, with many ill-resourced organizations—such as state and local governments and government agencies—bearing the brunt of these renewed attack efforts.
The big issue is that these attacks are wildly successful in at least the disruption and destruction phases (most victims of publicly disclosed ransomware attacks do not pay or at least do not admit to paying the ransom demands). You can investigate this yourself by a lightweight search on DataBreaches.net. In most of these incidents, it was apparent that:
- Attackers were generally successful due to good phishing campaigns and their ability to take advantage of poor system maintenance practices within impacted organizations.
- Victims take quite a while to recover from successful attacks because they do not have robust and practicable backup, restoration, and digital disaster recovery plans.
Your organization absolutely needs to invest in front-line phishing defenses such as DMARC and wicked-modern anti-phishing awareness programs. You also need to ignore pundits who tell you not to patch your systems and level up your vulnerability management program to make it harder for attackers use known system weakness to accomplish their goals.
You also need to ensure you've focused on a super-important CIS Critical Control: data recovery capability. This means you need to know which systems are critical to your business or operational processes and what data is needed to get mission-critical jobs done every day.
Don't mind if I do (Learning lessons from those who learned lessons)
You don't need to take our word for it. Both Maersk and, more recently, Norsk Hydro provide lessons that should be taken to heart.
Both suffered from powerful ransomware attacks and both underscore the need to be able to transition to manual processes during recovery efforts (which means you need a recovery plan).
In fact, you should take some time to read up on the Norsk Hydro attack, since it's not only a lesson in how to prepare for and recover from such an attack, but it's also the gold standard of how to handle a very public breach with impressive, regular disclosure, sharing of indicators, and radical transparency.
Hopefully, your organization will never have to deal with a ransomware attack, but relying on hope isn't a great cyberdefense strategy. Take stock of your ability to prevent and recover from ransomware-based attacks, talk to your industry peers and information-sharing groups to get an idea of prevalence and likelihood, and draft effective resilience and response plans. Doing so may help avoid the need for a "WannaCry: Three Years Later" retrospective.