Late last week, the Open Web Application Security Project (OWASP) released its top 10 list of critical web application security risks. The last OWASP Top 10 came out in 2017, and in the intervening 4 years, we've seen a fundamental shift in application security that includes greater emphasis on securing web applications during the ever-evolving development process.
In this post, we're going to discuss the 2021 OWASP Top 10, how the list is evolving alongside the web application security discussion, and what you should take away from this year's Top 10. And if you want to learn more, stay tuned in the coming weeks for deeper dives into several of the main recommendations this year's OWASP team has identified.
What is the OWASP Top 10?
The OWASP Top 10 is an awareness document that highlights the top 10 most critical web application security risks. The risks are in a ranked order based on frequency, severity, and magnitude for impact.
OWASP has maintained this list since 2003, and every few years, they update the list based on advancements in both application development and application security. Many organizations look to the OWASP Top 10 as a guide for minimizing risk.
So, what's changed?
As mentioned above, OWASP and their Top 10 have evolved to focus more on helping developers build secure applications and work with security teams. After partnering with organizations and once again taking into consideration frequency, severity, and magnitude for risk that these vulnerabilities introduce, OWASP recently released their new OWASP Top 10 for 2021. Check out the changes below:
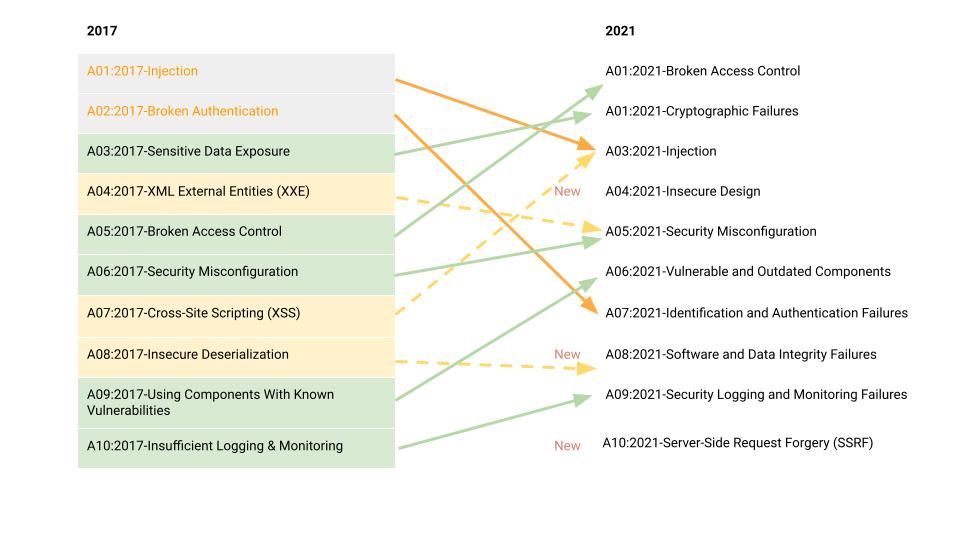
Some of the notable changes include the introduction of new categories, consolidation, and scope changes to categories. Examples of these changes include:
- The introduction of insecure design — We've seen this repeatedly highlighted as an area to watch, as the pressure mounts to continuously deliver new apps and features. An application's architecture must take thoughtful security principles into account from the very beginning of the design process.
- Broadened focus of injections — The new injection vulnerability category now includes 33 CWEs and many common injection types, such as SQL and NoSQL. The notable consolidation that took place this year was the inclusion of Cross-Site Scripting (XSS) into the injection category.
- Vulnerable and outdated components replace “using components with known vulnerabilities" — This is an example of an expanded scope of category to include using outdated open-source libraries and their associated vulnerabilities.
The changes to the OWASP Top 10 reflect the shifts we've witnessed in application development and security. As the pressure mounts for teams to deliver high-quality products faster than ever, and we see the introduction of many cloud-native technologies to facilitate the acceleration of development cycles, developers must focus on scalable security from the start.
The 2021 OWASP Top 10 highlights a strategic approach to security that includes the architecture that supports the application, as well as the APIs, data, and so much more. The methodologies for testing and monitoring your applications through development to production are also critical in this framework. The 2021 OWASP Top 10 highlights many of these changes with the adoption of best-in-class tools and practices such as shifting left, DevSecOps, and a focus on preventing risk through a combination of both testing and monitoring.
Want to learn more? Stay tuned for our follow-up blogs, where we'll take a deeper dive into some of the OWASP Top 10 to discuss what's changed and why these updates are important.
NEVER MISS A BLOG
Get the latest stories, expertise, and news about security today.
Subscribe