This post offers a closer look at some of the recent updates and releases in InsightIDR, our extended detection and response solution, from Q3 2021.
Welcome IntSights to the Rapid7 Insight Platform family!
As you may have seen in recent communications, Rapid7 acquired IntSights, a leading provider of external threat intelligence and remediation. We're excited to introduce their flagship external threat intelligence product, Threat Command, as part of our Rapid7 portfolio. Threat Command allows any SecOps team, regardless of size or capability maturity, to expand identification and remediation across an ever-expanding attack surface, while automating threat mitigation.
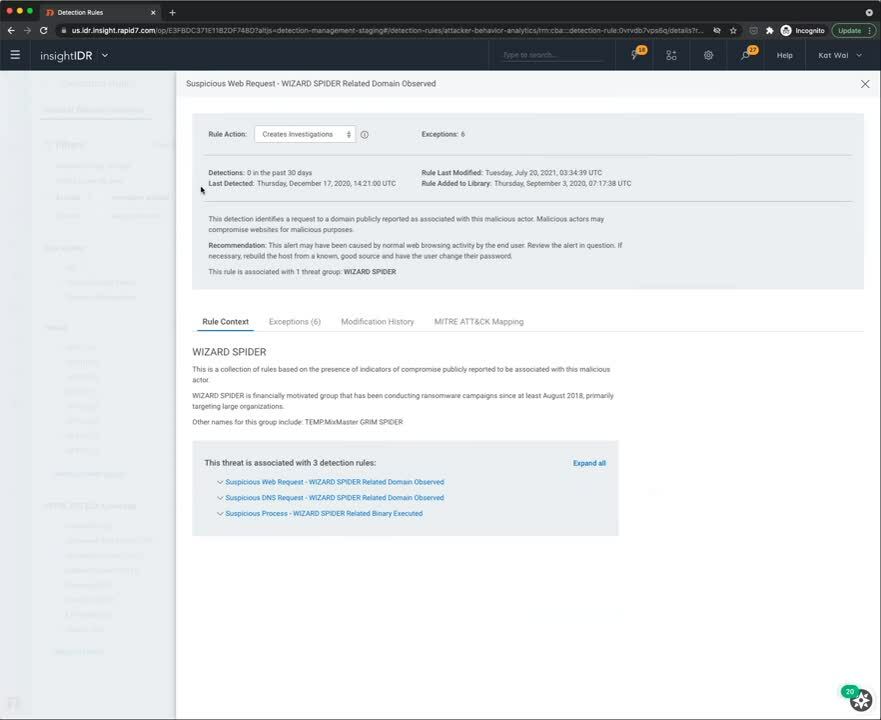
New detection rule management experience
We're excited to announce that InsightIDR customers now have more customization and increased visibility for Attacker Behavior Analytics (ABA) detections. We're continuing to make improvements and additions to our detections management experience — here are the latest additions:
- Detection rules — Filter detection rules by threat group, rule behavior, and attributes for more visibility into your alerts and investigations.
- MITRE ATT&CK mapping — View and filter detections by specific MITRE ATT&CK framework tactics and techniques for more context to the alerts in your environment.
- Create exceptions to a detection rule — In the past, IDR customers could only tune alerts once they were an investigation, and they could not control how IDR would tune the alert for them. Now, with exceptions for ABA alerts, you can filter out noise very precisely using data from the alert.
See the latest detection management experience in the demo below:
526 new ABA detection rules added to IDR
We've also added 526 new ABA detection rules into InsightIDR to expand its coverage of Windows, Mac, and Linux suspicious process threats, covering a wide variety of techniques on the MITRE ATT&CK matrix. These detection rules can be tuned to your environment by creating exceptions and modifying the rule action to only receive the alerts you care about. Visit the Detection Library for actionable descriptions and recommendations.
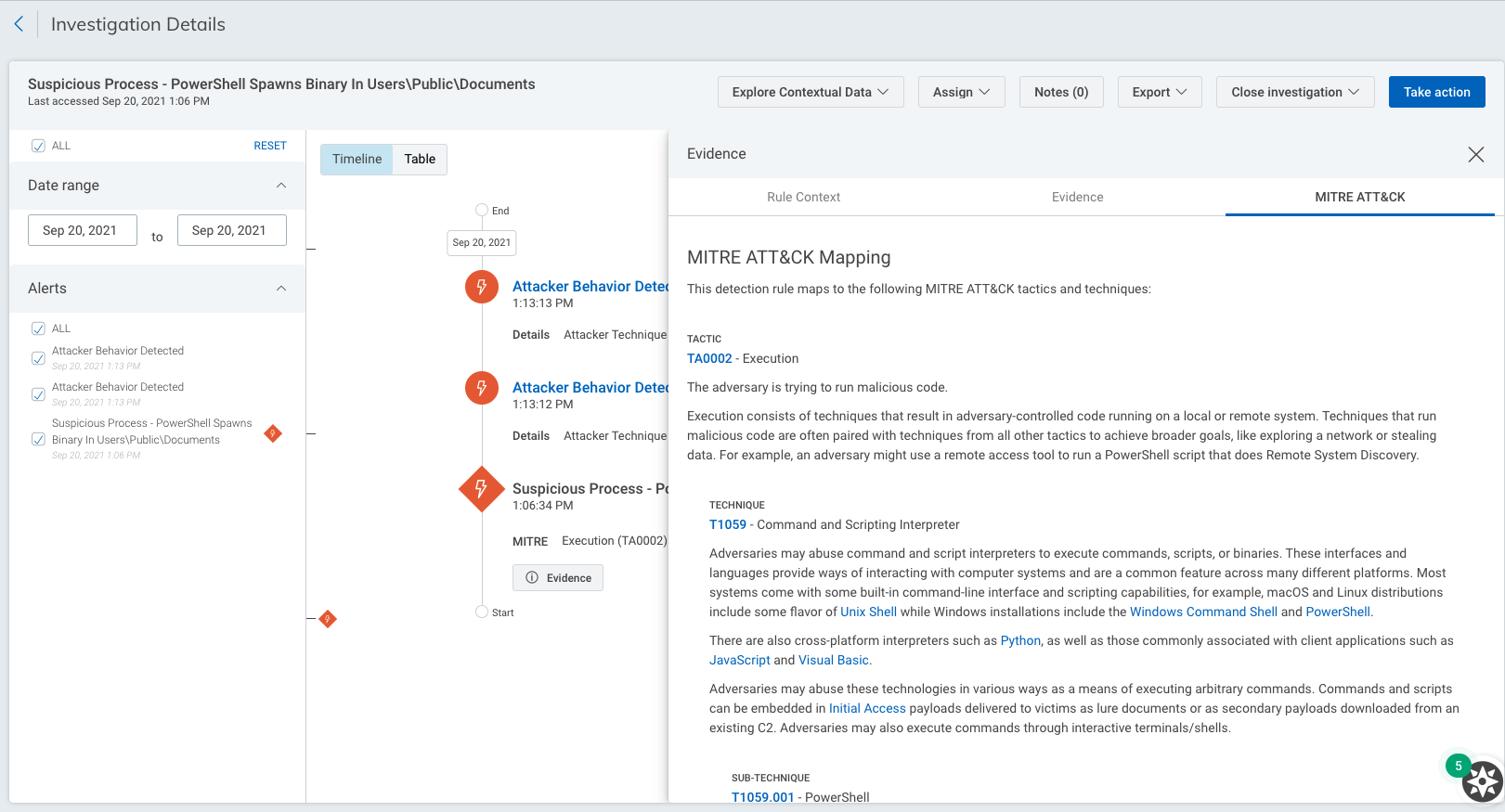
MITRE ATT&CK details in investigations
In addition to our detections updates, we've made improvements to our investigations experience to provide deeper insight into an attacker's position in the kill chain and give context into the nature of an alert.
When performing an investigation in InsightIDR, detections will be mapped to a description of the associated MITRE tactics, techniques, and sub-techniques. You'll also be prompted to visit attack.mitre.org to view context rich adversary behavior profiles with descriptions, MITRE ATT&CK mitigation strategies, and detection recommendations for each tactic, technique and sub-technique, developed by MITRE.
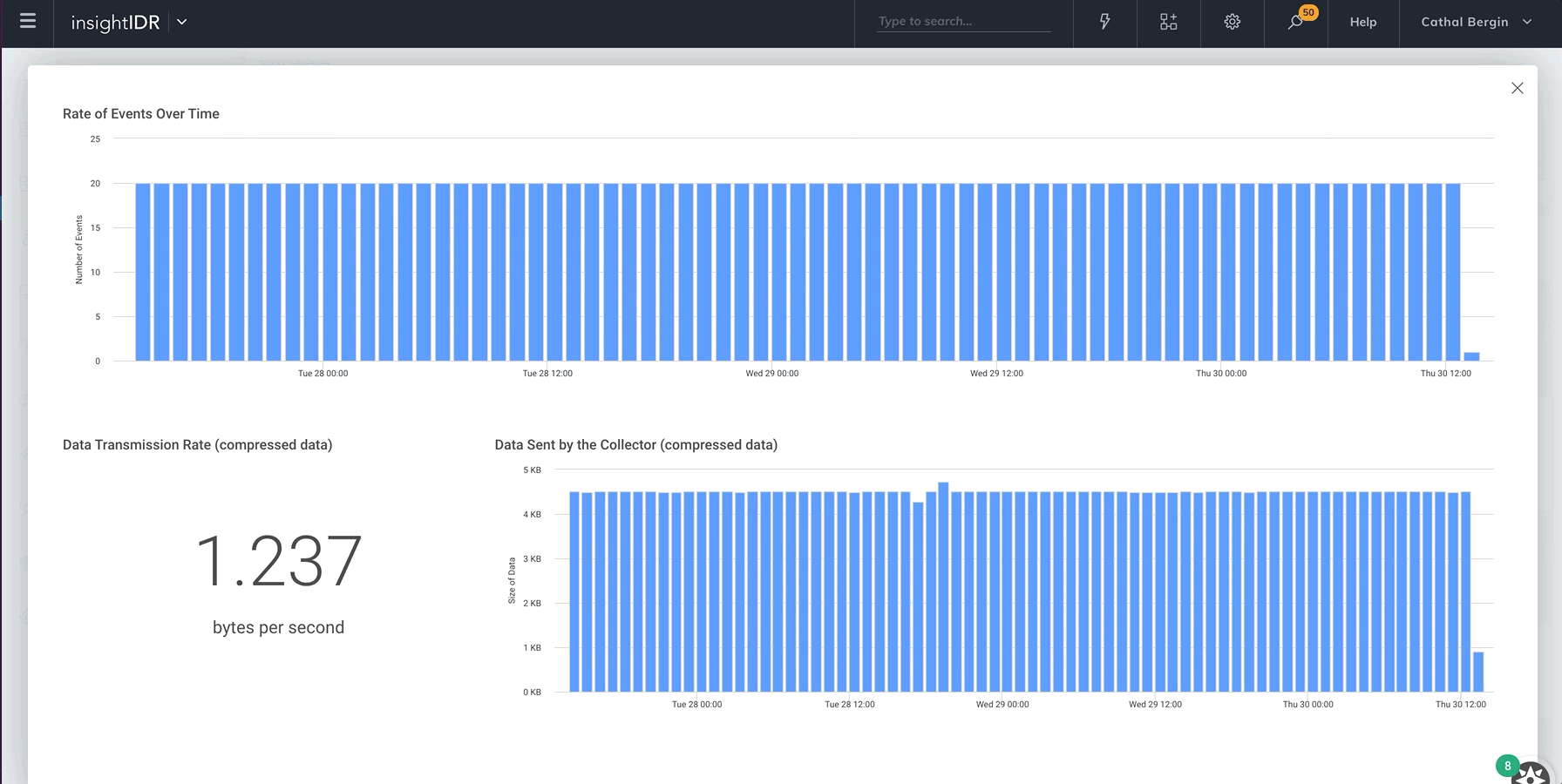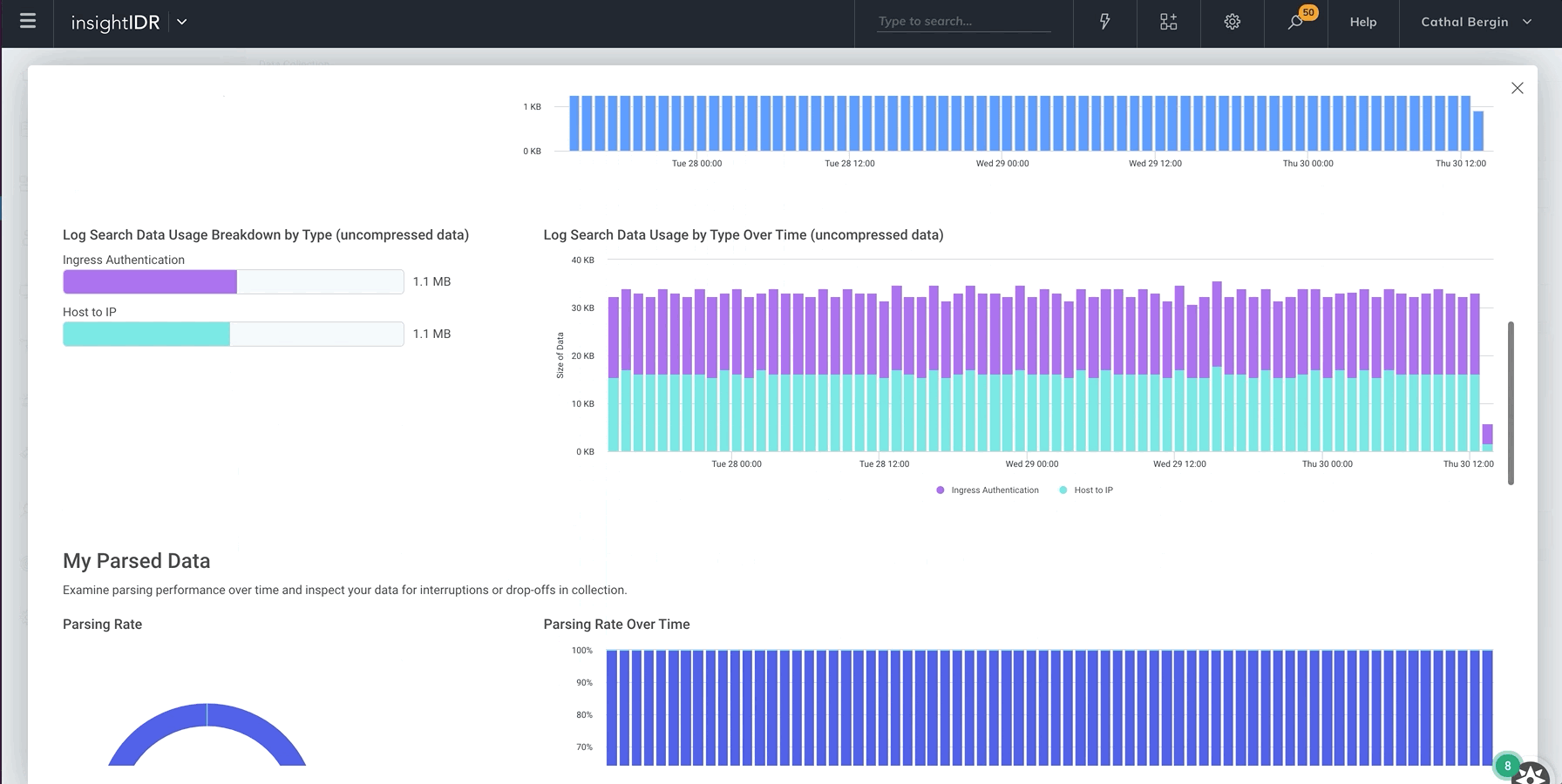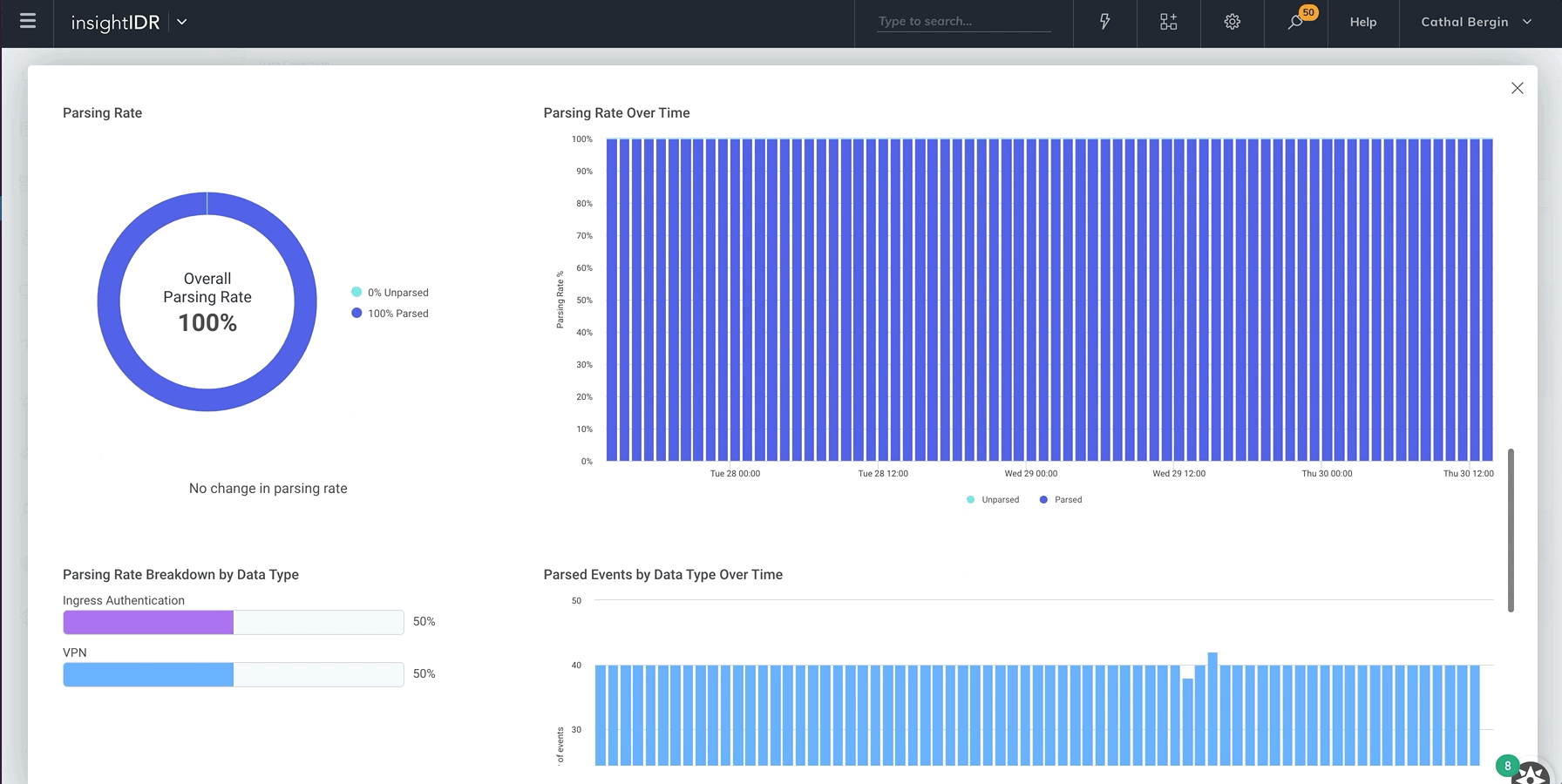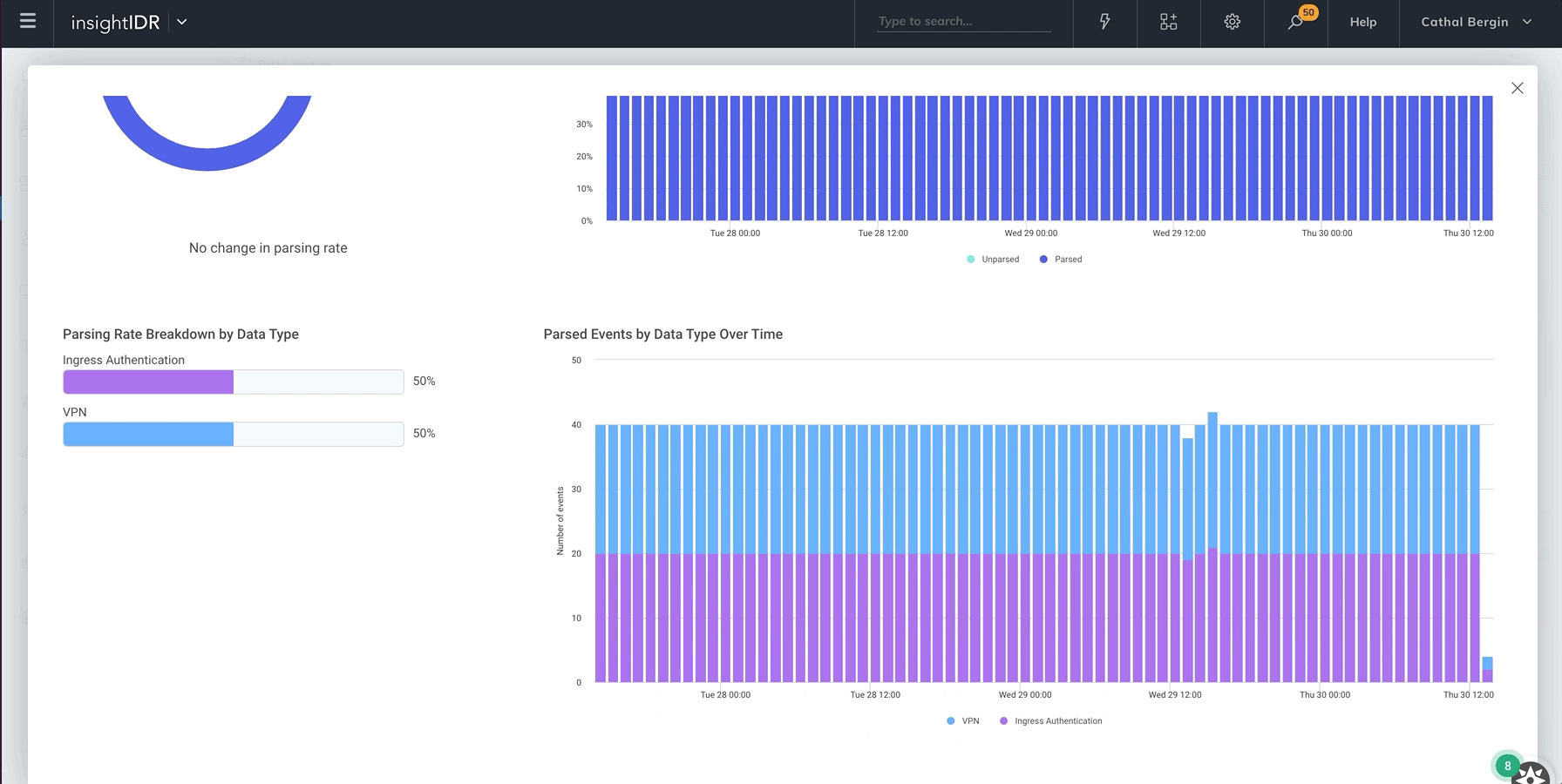
Monitor event source health
We recently released new visual tools to help you easily view the health of your event source data. You now have extensive visibility into data transmission and parsing rates of your event source. This allows you to check if an event source is running as intended, quickly identify any issues or unusual activity, or visually compare data for each event source.
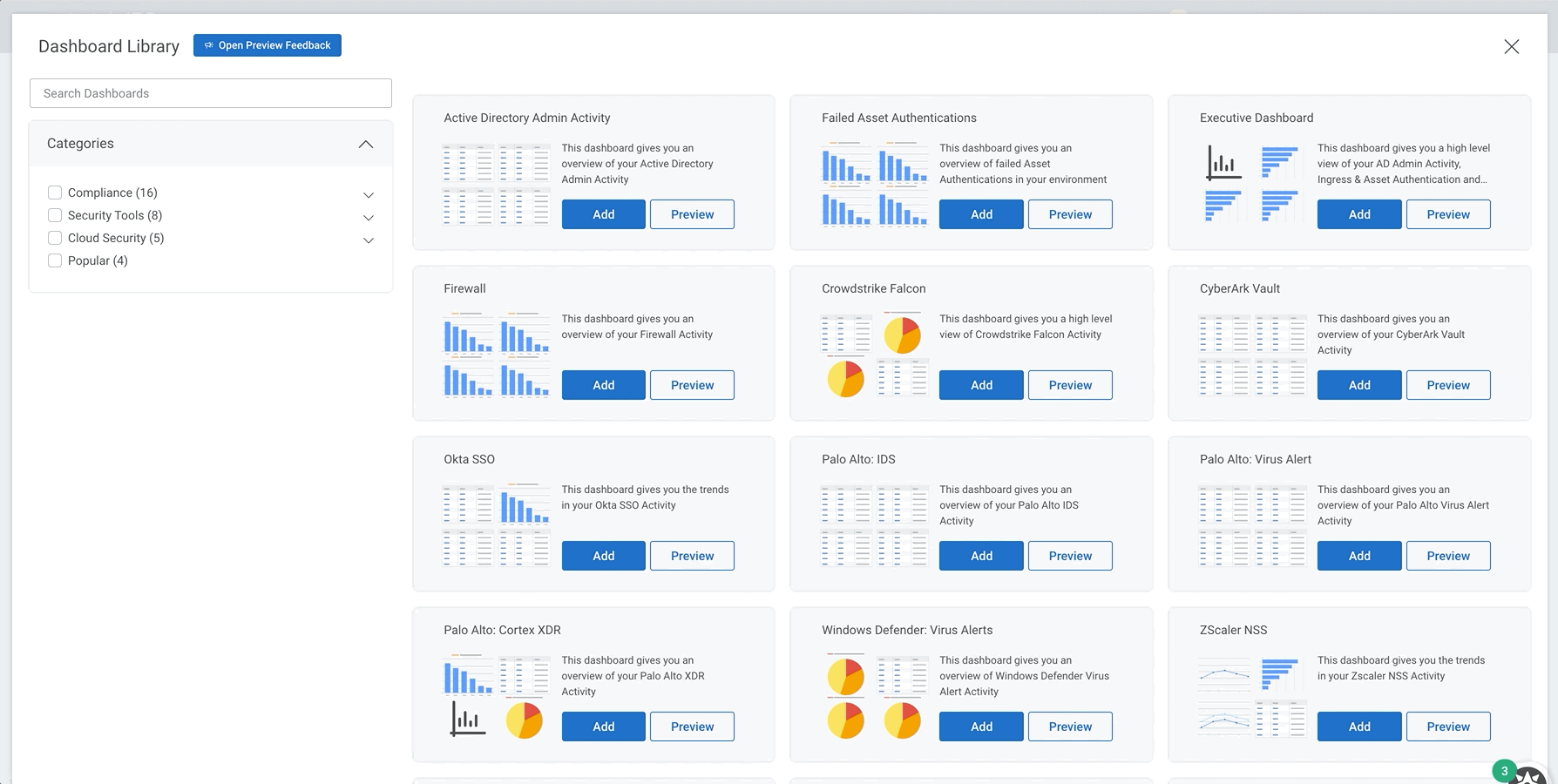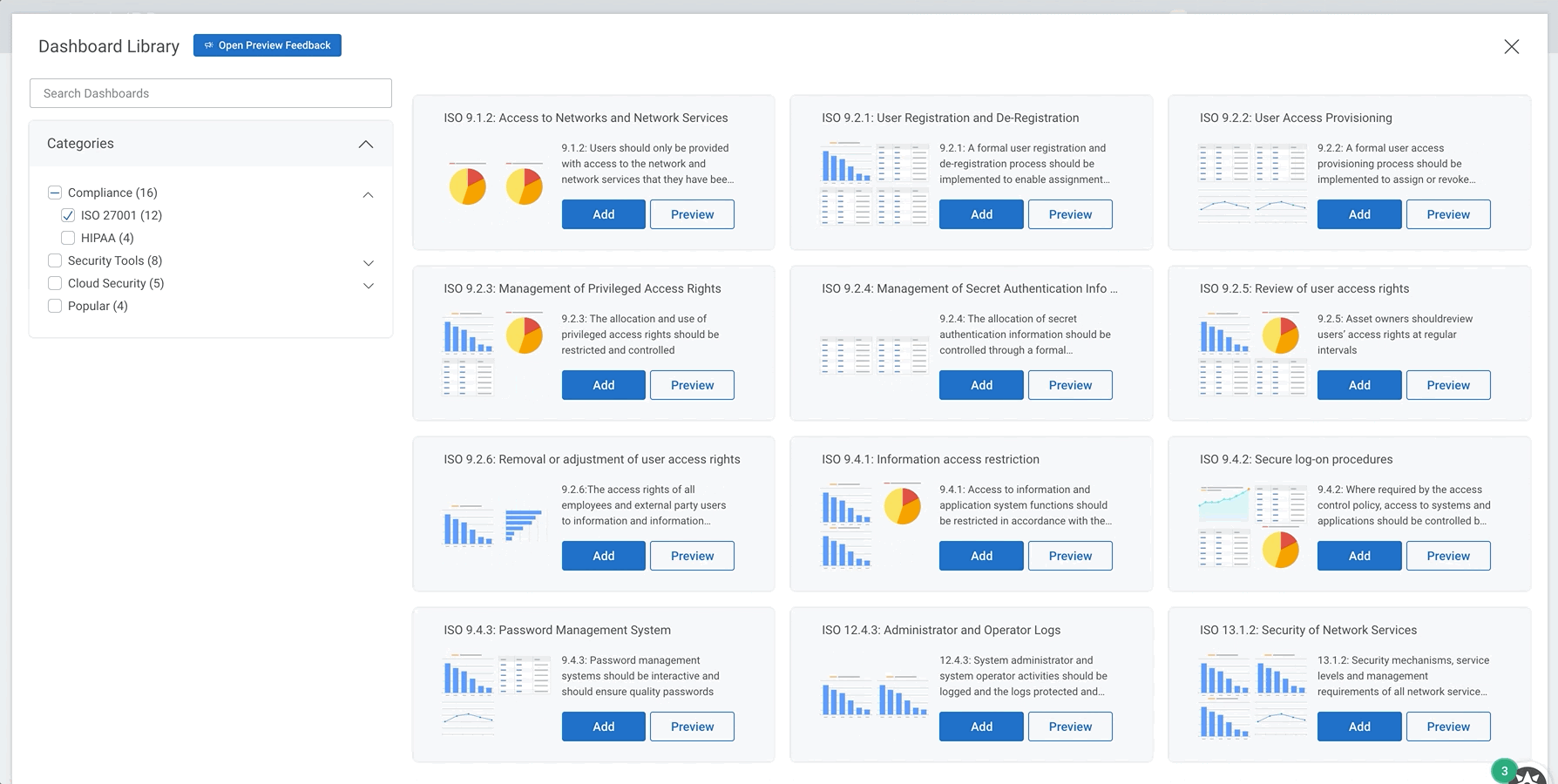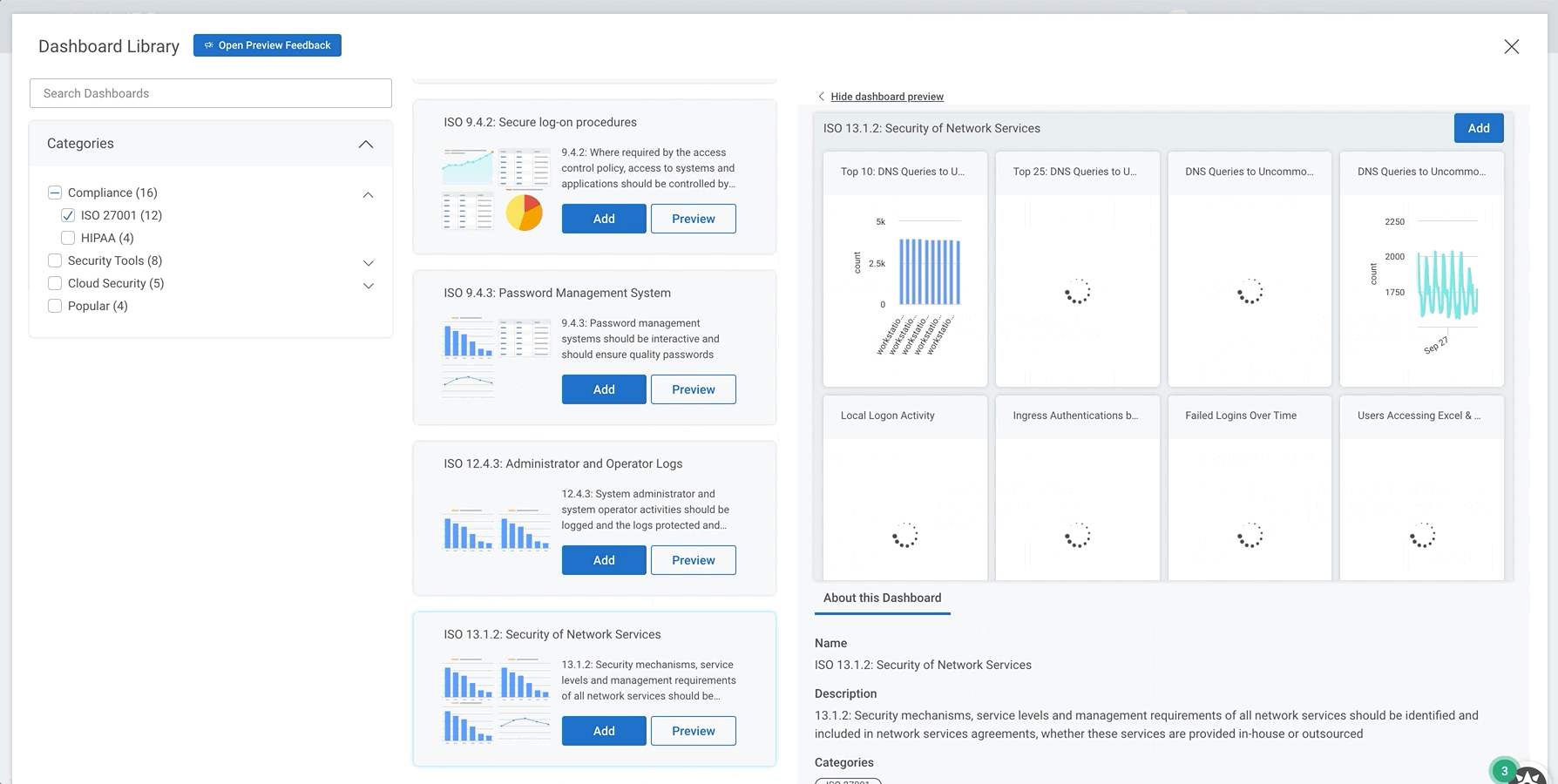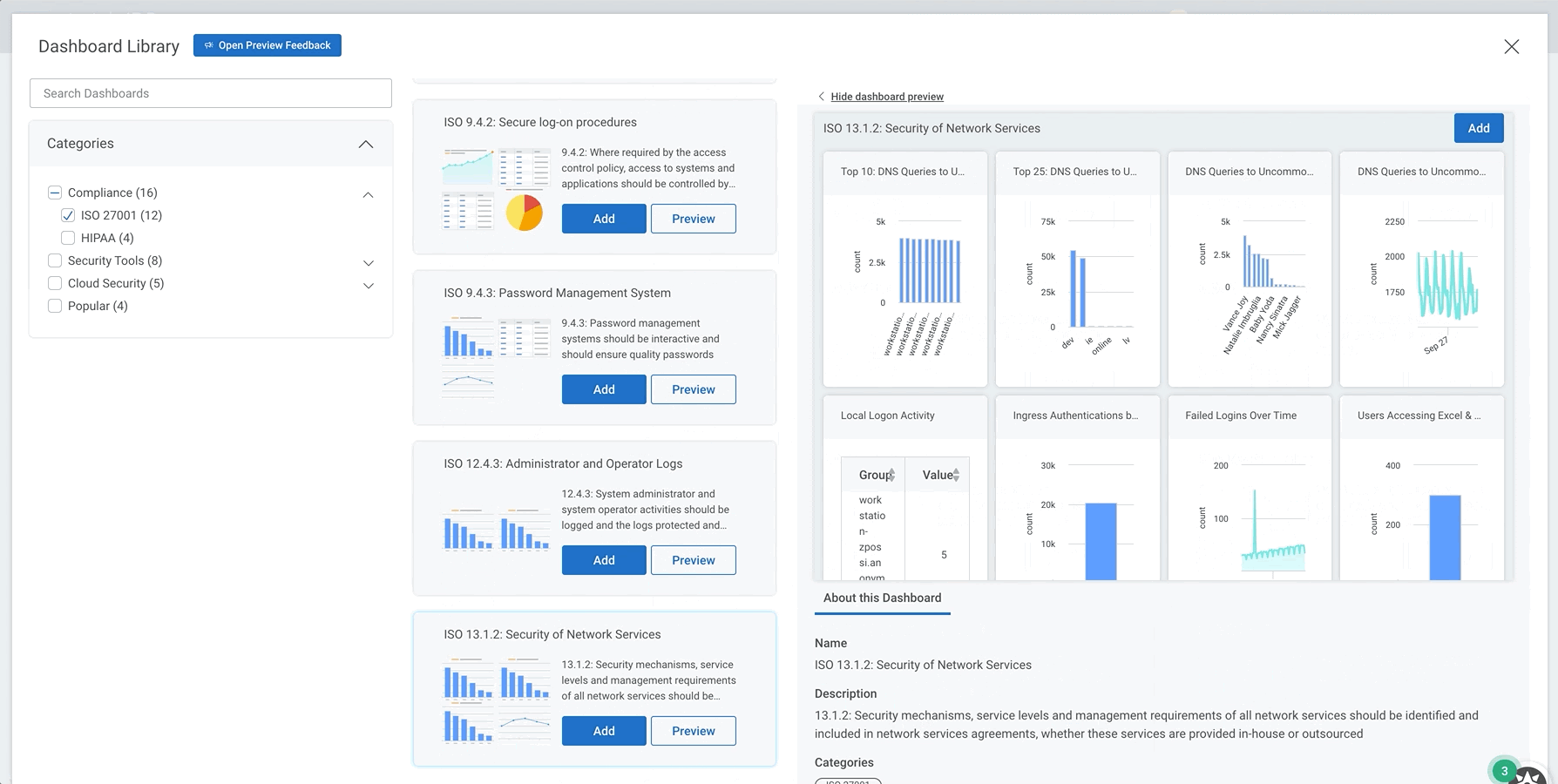
New pre-built dashboards for HIPAA, ISO 27001, and more
We recently introduced a library of pre-built dashboards that make it easier than ever to get insight from your environment. Entire dashboards, created by our Rapid7 experts, can be set up in just a few clicks. Our dashboards cover a variety of topics, including key compliance frameworks like PCI, ISO 27001, and HIPAA; security tools like Zscaler and Okta; and more general dashboards covering Asset Authentication and Firewall activity.
The Lost Bots vlog series
Rapid7's latest vlog series, The Lost Bots, hosted by Detection and Response Practice Advisor and former CISO Jeffrey Gardner, offers a look into the latest and greatest in security. In each episode, Jeffrey talks with fellow industry experts about current events and trends in the security space, best practices, and lessons from our Rapid7 SOC team.
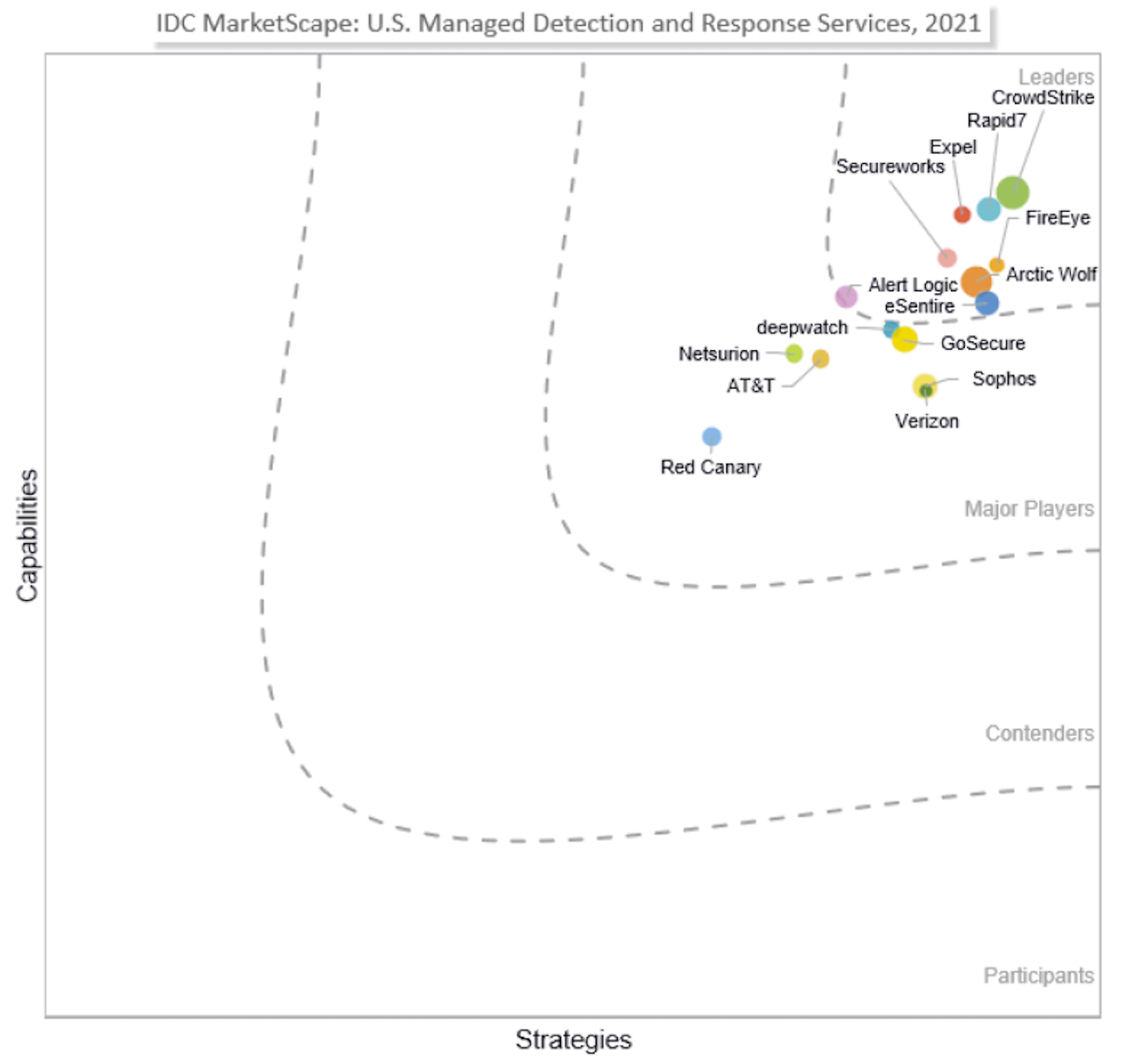
Rapid7 MDR named an IDC MarketScape Leader
We're thrilled that Rapid7's MDR was recognized as a Leader in the IDC MarketScape: Managed Detection and Response 2021 Vendor Assessment. This IDC MarketScape report shows an unbiased look at 15 MDR players in the US market, evaluating each on capabilities. We credit this recognition to customers like you who provide the critical feedback and guidance to improve our service — thank you!
Attack Surface Visibility, now in MDR Essentials
Our goal with Attack Surface Visibility — built exclusively for our MDR Essentials — is to help customers act proactively with a monthly snapshot of how exposed their attack surface looks to an opportunistic attacker. While this certainly is not a replacement for a true vulnerability management program, Attack Surface Visibility lets your team see obvious weak points that attackers may exploit and helps optimize your efforts with clear, prioritized actions to remediate risks and improve your security posture.
Stay tuned!
As always, we're continuing to work on exciting product enhancements and releases throughout the year. Keep an eye on our blog and release notes as we continue to highlight the latest in detection and response at Rapid7.
NEVER MISS A BLOG
Get the latest stories, expertise, and news about security today.
Subscribe
