- Home
- Products
- InsightIDR
- Use Cases
- Automated Containment
insightIDR
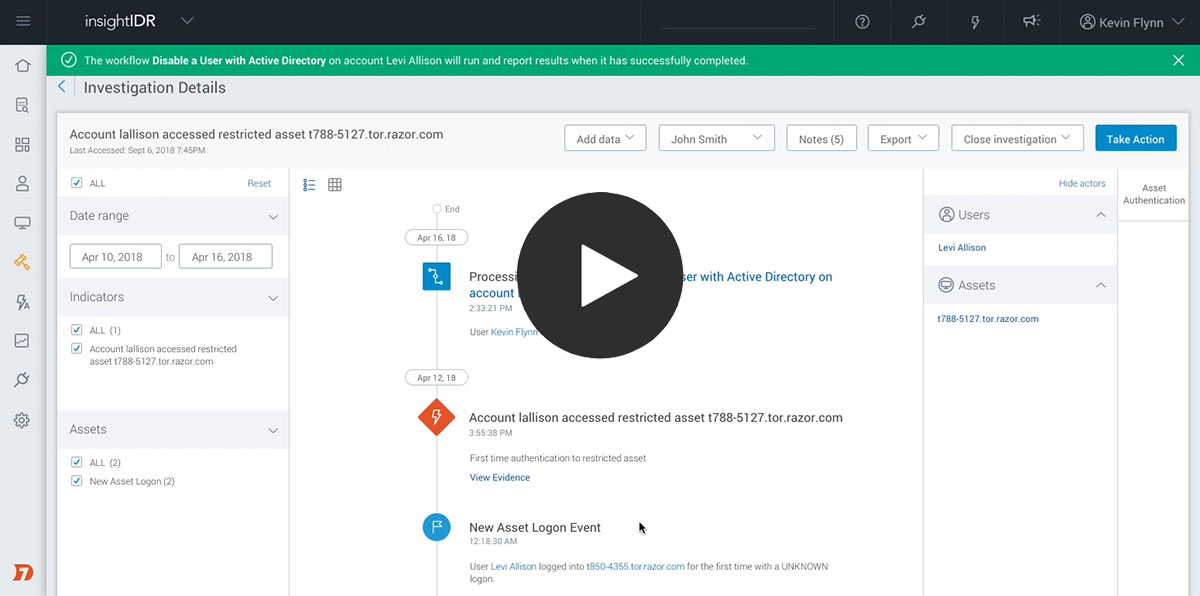
Automatically Contain Compromised Users and Assets
Get a Free Trial
No credit card necessary
Watch Demo
See how it all works
Take immediate steps to contain threats
Save time and lower risk across your entire incident response lifecycle. When investigating threats in InsightIDR, you not only get important context, but you can take immediate steps to contain a threat. With the included Insight Agent, you can kill malicious processes or quarantine infected endpoints from the network. You can also use InsightIDR to take containment actions across Active Directory, Access Management, EDR, and firewall tools. This gives your team the power to directly contain threats on an endpoint, network, and user level.