- Home
- Products
- InsightIDR
- Use Cases
- Identify Evolving Attacker Behavior
insightIDR
Identify Evolving Attacker Behavior
Automatic threat intel and analyst expertise
Between Metasploit, penetration tests, and our 24/7 Managed Detection and Response service, we're investigating a constant stream of attacker behavior. As part of the investigative process, our analysts directly contribute Attacker Behavior Analytics (ABA) detections into InsightIDR, paired with recommendations and adversary context. These detections leverage the real-time user and endpoint data collected by InsightIDR. The result: the alert fidelity you want, filled with the context you need.
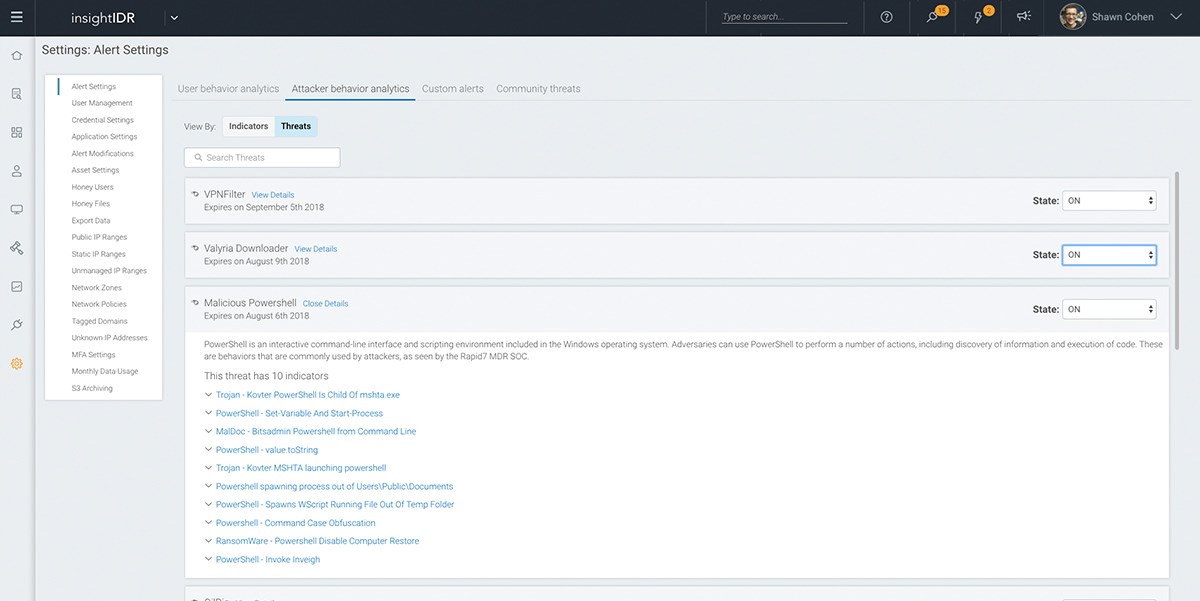

Find attacker techniques with pre-built detections
Fileless malware. Spear phishing. Crypto-jacking. Attackers' techniques for persistence shift, but they remain finite. As our analysts contribute Attacker Behavior Analytics, these detections are tested against the Rapid7 Insight platform to ensure you only get high-fidelity alerts in InsightIDR.