The Metasploit Framework and the commercial Metasploit products have always provided features for assessing the security of network devices. With the latest release, we took this a step further and focused on accelerating the penetration testing process for Cisco IOS devices. While the individual modules and supporting libraries were added to the open source framework, the commercial products can now chain these modules together to quickly compromise all vulnerable devices on the network. The screen shot below gives you an idea of what a successful penetration test can look like:
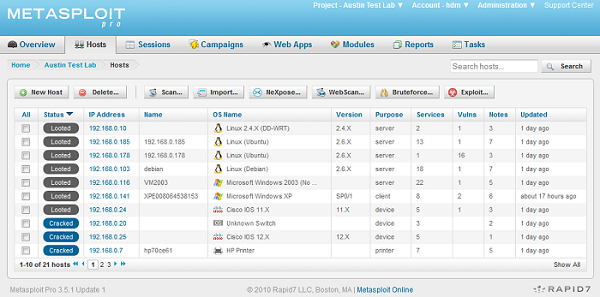
To begin with, I should state that a properly configured Cisco device is a tough target to crack. Vulnerabilities exist in IOS, just like any other piece of software, but only a few folks have managed to leverage memory corruption flaws into code execution. For this reason, the majority of real-world attacks against IOS devices tend to focus on two areas: poor configuration and weak passwords.
Before we dive into the specifics, lets review the current "state of the art" in Cisco IOS security testing. Vulnerability scanners do a great job of identifying out of date IOS installations by comparing version strings. This works well for determining whether a device is patched, but doesn't help a penetration tester who doesn't have a deep background in IOS exploitation. With few exceptions, this leaves a small number of services that are commonly exposed in production environments. These services include SNMP, Telnet, SSH, and HTTP. You may also find Finger running or relay services for media protocols like SIP and H.323. For remote access, the first four are what most of us have to work with, and even then, its rare to find a properly configured router with any of those services exposed to the network at large.
The Cisco IOS HTTP service has a few well-known vulnerabilities on older versions of the operating system. The two we care about as penetration testers both relate to authentication bypass. The first flaw, CVE-2000-0945, relates to missing authentication in the IOS Device Manager interface. This vulnerability allows unauthenticated, often privileged access to the IOS installation through the web interface. The second vulnerability, CVE-02001-0537, allows an attacker to bypass authentication by specifying an authentication level higher than "15" in the request to the HTTP service. This also provides privileged access to the device through the web interface. The open source Metasploit Framework now provides two modules for exploiting these vulnerabilities:
Metasploit Express and Metasploit Pro will automatically recognize Cisco IOS HTTP services during a discovery scan, check for these two flaws, and exploit them to gain access to the running device configuration.
In addition to these two known vulnerabilities, the device password can also be determined through a brute force attack on the HTTP service. The HTTP protocol is relatively quick to brute force, compared to slower, terminal-based services like Telnet and SSH. Metasploit Express and Metasploit Pro will automatically grab the running device configuration after a successful HTTP brute force of an IOS device.
The next service I want to discuss is SNMP. Oddly enough, SNMP is often left exposed on otherwise secure routers. The reason for this may be the general view of what SNMP is and does. The Simple Network Management Protocol is great for polling information across a wide range of systems in a standard format. Regardless of who built your switch or router, just about any SNMP client and monitoring software will work with that device, provided SNMP is enabled and configured.
What many network administrators don't realize, is not only the depth of information exposed by SNMP but the fact that a writeable SNMP community can be leveraged to gain complete control over a device. In the case of Cisco IOS, a writeable SNMP community can be used to download the running device configuration AND modify the running configuration. A router with telnet disabled and a complex serial password can be hijacked nearly instantly through a writeable SNMP community. The Metasploit Framework provides a SNMP brute force tool, written as an auxiliary module, which can leverage a wordlist of common passwords to identify valid communities and determine whether they are read-only or read-write. In addition to the basic brute force module, Metasploit now contains a module (submitted by community contributor "pello"), that can use a writeable SNMP community to download the running device configuration.
Metasploit Express and Metasploit Pro use these two modules to automatically grab the configuration files of vulnerable devices. During a discovery scan, the SNMP brute force tool is launched in the background with a small wordlist of common communities. If any of these passwords work and the community is detected as writeable, the product will configure a local TFTP service and download the running configuration file. Since the SNMP protocol is now integrated into the intelligent brute force component of the product, the same now applies to communities guessed during a brute force run. The brute force component uses a highly tuned list of communities in addition to the dynamically generated passwords for that project. This tuned list is derived from a research project that involved scraping web forms for pasted configuration files, extracting and brute forcing the embedded passwords, and then analyzing the results to determine what passwords are most commonly used, including SNMP communities. The results of this project were surprising, I would never have guessed that "public@es0" and "private@es0" were widely used due to an example configuration included in theCisco documentation.
The last two protocols I want to discuss are Telnet and SSH. These protocols both provide access to a remote command shell on the target device, usually as non-privileged user. The most notable difference from penetration testing perspective, is that SSH often requires knowledge of a remote username and password, where Telnet is often configured with password-only authentication. The Metasploit Framework contains modules for brute forcing both of these protocols and will automatically create an interactive session when the brute force process succeeds.
Metasploit Express and Metasploit Pro have always supported attacks against network devices using the Telnet and SSH protocols, but with the latest release, now leverage the tuned password list from our password analytics research. This results in some unusual passwords floating to the top of the wordlist, but is extremely effective against real-world configurations. Without giving too much away, I can say that some ISPs are notorious for using static passwords to configure customer-owned equipment.
After a session has been established through the Telnet or SSH protocols on a Cisco IOS device, the Evidence Collection feature in the commercial products will automatically grab the version information, active user list, and attempt to brute force the enable password with a list of common passwords. If the collection script is able to gain enable access, it will automatically dump additional information from the system, including the running configuration.
The attacks listed above are not anything new. What is new is the ease that they can be carried out using Metasploit and the ability of the commercial products to chain them together to automatically compromise vulnerable devices. These attacks are just an extension of our existing coverage and a hint of what is on the roadmap for future development of our commercial products.
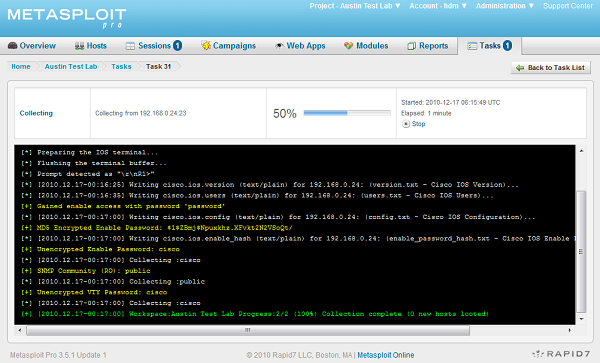
One thing I haven't mentioned so far is what we actually do with the Cisco IOS configuration files after we capture them. These files contain the running configuration of the device, this includes the vty passwords, enable passwords, VPN keys, SSL certifications, and WiFi credentials. Metaspoit will automatically parse these configuration files to scrape out sensitive data and store it as either evidence of a compromise or as stolen authentication credentials. The screen shot below demonstrates the output of brute forcing the Telnet vty password, then the enable password, then dumping and parsing the configuration:
Metasploit Express and Metasploit Pro can automatically recycle credentials obtained from these configuration files to gain access to other devices on the network. If you crack one Cisco device through a weak SNMP community and discover that the vty password is "ciscorules!", you can use the "known-only" profile of the brute force component to automatically try this password, via any protocol, against any other device on the network. Once you gain access to other devices, the configuration files are obtained and the entire process starts again. You can easily apply a password taken from a Cisco router against the login page of an intranet site or leverage a password obtained through a traditional exploit to gain access to a multitude of network devices. One of our development goals is to ensure that our users can always identify and exploit the weakest link on a given network.
That's it for this post, please give the new features a whirl and let us know via comments if you have any questions or suggestions for improvements.
-HD