Since our latest w3af release in mid January, and our new windows installer release a couple of months ago, we've got lots of encouraging words telling us we are going in the right direction. The objective was near and we could almost taste it. Having a stable code-base is no joke, it requires countless hours of writing unit-tests, running w3af scripts and most importantly: fixing bugs. Now, finally we're here!
In this latest release, we bring you a couple of the most important improvements of our framework:
- Stable code base, an improvement that will reduce your w3af crashes to a minimum. We've been working on fixing all of our long-standing bugs, wrote thousands of lines of doctests and various types of automation to make sure we can also keep improving without breaking other sections of the code.
- Auto-Update, which will allow you to keep your w3af installation updated without any effort. Always get the latest and greatest from our contributors!
-
Web Application Payloads, for people that enjoy exploitation techniques, this is one of the most interesting things you'll see in web application security! We created various layers of abstraction around an exploited vulnerability in order to be able to write payloads that use emulated syscalls to read, write and execute files on the compromised web server. Keep an eye on this blog for an entry completely dedicated to this subject! For now, here you have a screenshot of the "tcp" payload extracting open TCP connections only by performing read() syscalls:
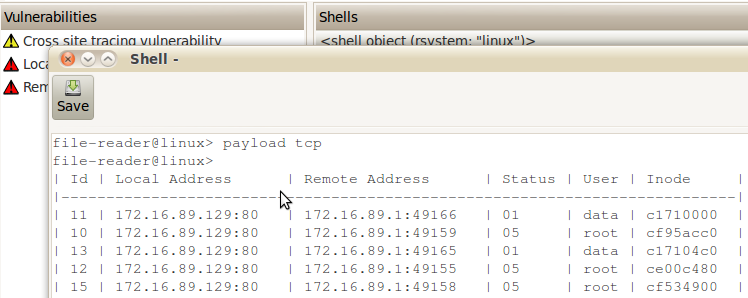
- PHP static code analyzer, as part of a couple of experiments and research projects, Javier Andalia created a PHP static code analyzer that performs tainted mode analysis of PHP code in order to identify SQL injections, OS Commanding and Remote File Includes. At this time you can use this very interesting feature as a web application payload. After exploiting a vulnerability try: "payload php_sca", that will download the remote PHP code to your box and analyze it to find more vulnerabilities!
And many others, such as:
- Refactoring of HTTP cache and GTK user interface code to store HTTP requests only once on disk (5% performance improvement)
- Performance improvement in sqlite database by using indexes (1% performance improvement)
- Huge w3af code-base refactoring on how URLs are handled. Moved away from handling URLs as strings into a url_object model. This reduces the number of times a URL is parsed into its component pieces (protocol, domain, path, query string, etc.) and put back together into a string, which clarifies the code and makes it run faster.
We have a stable release, w00t! Hmmmm.... have we finished? Should we go home? No! We still have work to do; there are still features and capabilities we'd like to add. For example,as you read this, we're working on integrating the multiprocessing module into w3af's code, with the objective of using more than one CPU core at the same time and substantially improve our scanning speed. We're also working on handling of encodings by the use of unicode strings across the whole framework, and making the user experience more intuitive by changing bits and pieces of the graphical user interface.
As usual, you can get our latest installable packages from the w3af.com website! Just download and enjoy our latest improvements!