As a pentester for Rapid7 I use Metasploit a lot. I think one of the most overlooked features in Metasploit is the ability to create resource scripts. What are resource scripts you ask? “A resource file is essentially a batch script for Metasploit; using these files you can automate common tasks – H.D. Moore.”
There are several resource scripts included with Metasploit, one of which is port_cleaner. If you're like me you have had times when, after importing NMAP scan data, a bunch of cruft for closed and filtered ports shows up. Well, port_cleaner cleans the cruft out and makes dealing with the data much easier.
Now to the real reason for this blog post; how to leverage the power of resource scripts. I was on an assessment a while ago where my customer wanted to know which of its web servers were running weak SSL ciphers and the SSLv2 protocol. Like you, SSLScan is usually my go to tool for this task. I wanted to switch things up a bit. I use Metasploit's database as a data repository for anything related to my penetration tests. So I started thinking, how can I get my SSLScan data into Metasploit? My first thought was to write a parser that would take SSLScan's output and import it into Metasploit's database. Well, this approach would help me get to my end goal (having the data in Metasploit), but it would require an additional step to get it there. There had to be a better way. My friends, Resource Scripts are that better way!
The true power of resource scripts lie in the ability to use most, if not all, of the functions available within Metasploit. In my case, @TheLightCosine has already written an awesome SSL scanner class in Metasploit. My goal was to leverage that scanner to identify weak SSL ciphers and protocol versions and dump the data into Metasploit's database for reference and reporting.
My first concern was to figure out how to access the SSL scanner function via my resource script. Because resource scripts run in the context of the framework, you can access functions simply by calling them. The example below shows how this works. From within my resource script, I call the Rex::SSLScan::Scanner which creates a new scanner object for me to work with.
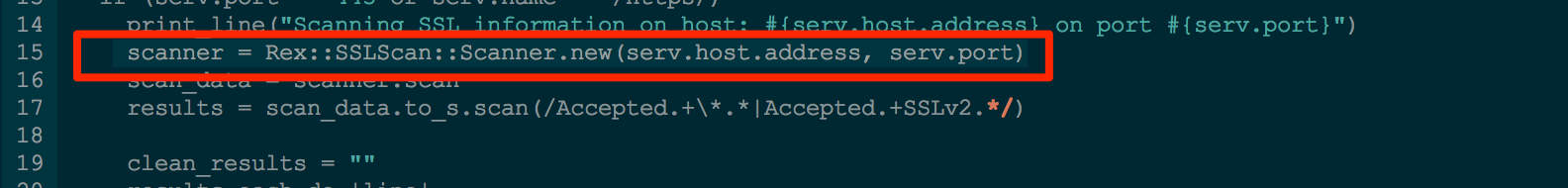
With that figured out, how might I run the scanner against all the hosts in my workspace that have SSL enabled? Never fear framework.db.workspace.services is here. I simply loop over each service entry looking for port 443 or https then sick the scanner on them.
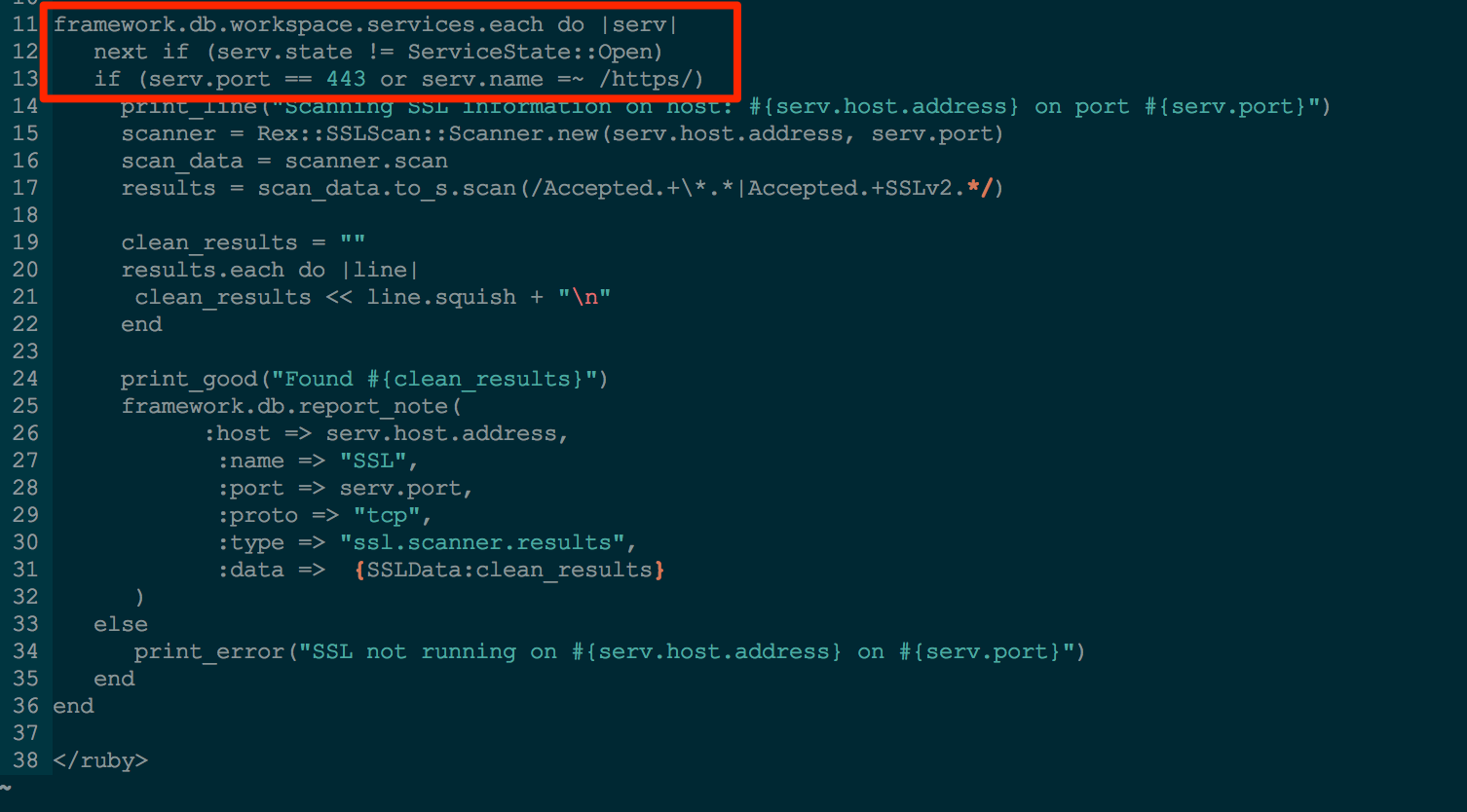
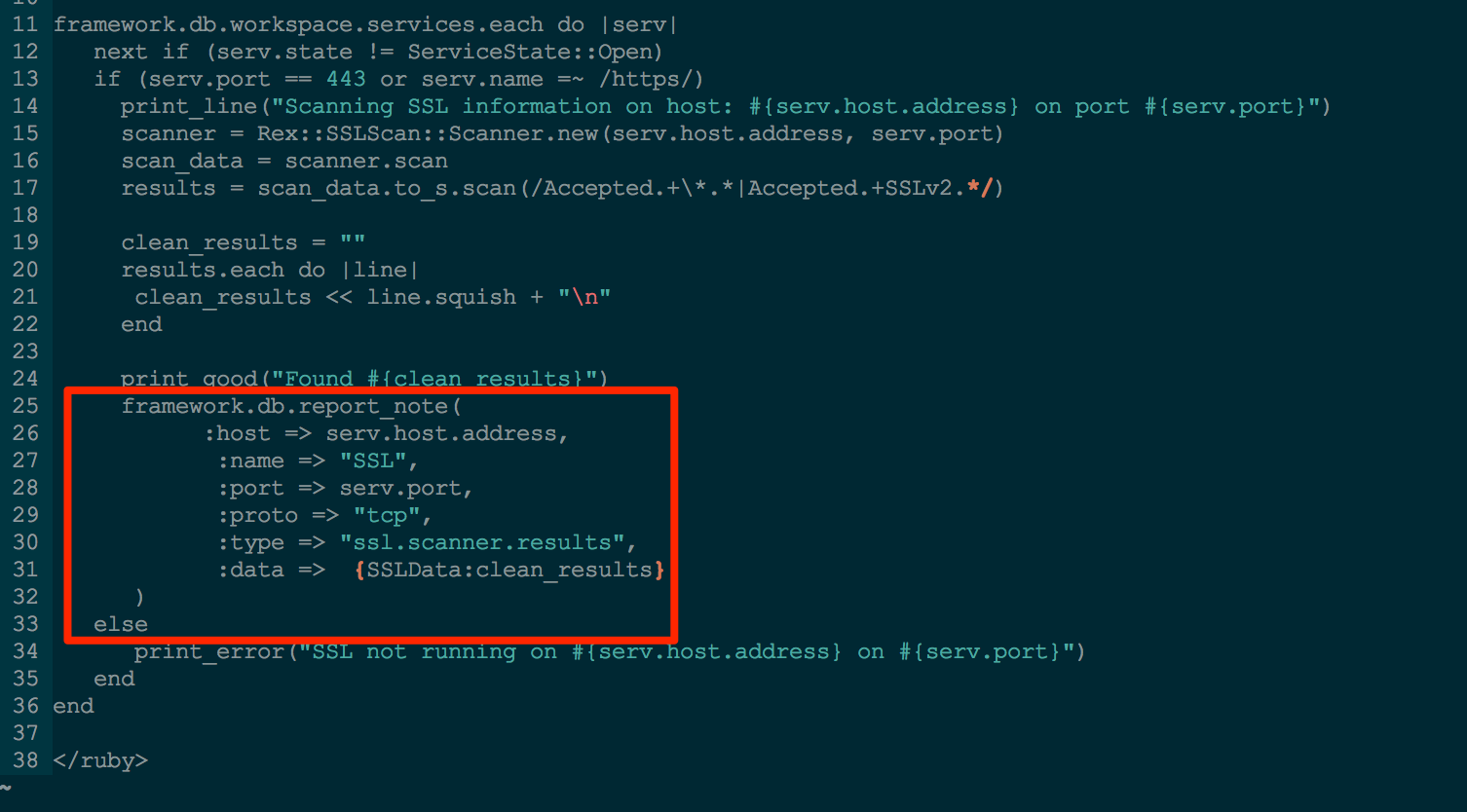
Once I have the results I'm looking for, I use framework.db.report_note to store the data in my workspace. This allows me to later search the notes table for any hosts that have SSL notes associated with them.
I hope this has shown you some of the power you can wield with resource scripts. A 5-minute investment on a resource script can save a ton of time in the end.
Additional references:
My SSL scan resource script-
https://gist.github.com/parzamendi-r7/bf216a71be19025fd51d
List of resource scripts included with Metasploit -
https://github.com/rapid7/metasploit-framework/tree/master/scripts/resource
Six Ways to Automate Metasploit-