
Metasploit, backed by a community of 200,000 users and contributors is the most impactful penetration testing solution on the planet. With it, uncover weaknesses in your defenses, focus on the highest risks, and improve your security outcomes. Your Metasploit Pro console produces a lot of important logs. It is essential to be able to review these logs, alert on them, and keep them secure.
Why should I monitor these logs?
The logs produced by your Metasploit Pro console are helpful when troubleshooting, and also for monitoring the usage of the . Metasploit Pro is impressively powerful, which also makes it crucial to closely monitor the usage. Unfortunately, you must always plan fo the worst possible scenario, including the potential for a Metasploit user to alter the logs created by the console to hide their actions. Sending these logs to a secure central location in real-time, can ensure that they remain unaltered and easy to review.
What and where are the Metasploit Pro Logs?
The list below details all of the logs created by your Metasploit Pro console and where they are saved. Your installation root directory may vary; by default the installation root for Linux is: /opt/metasploit and for Windows: C:\metasploit
- $INSTALL_ROOT/apps/pro/nginx/logs/error.log – Console web server error log
- $INSTALL_ROOT/apps/pro/nginx/logs/access.log – Console web server access log
- $INSTALL_ROOT/apps/pro/ui/log/production.log – Rails (ruby) log
- $INSTALL_ROOT/apps/pro/engine/config/logs/framework.log – Metasploit Framework log
- $INSTALL_ROOT/apps/pro/engine/prosvc_stdout.log – Metasploit RPC output log
- $INSTALL_ROOT/apps/pro/engine/prosvc_stderr.log – Metasploit RPC error log
- $INSTALL_ROOT/apps/pro/tasks – Task logs
- $INSTALL_ROOT/apps/pro/engine/license.log – License log
As a best practice, all of the above logs should be sent to a secure, off-site, location for storage and analysis. For the purposes of this post we will focus on the three most imperative logs:
- tasks
- framework.log
- access.log
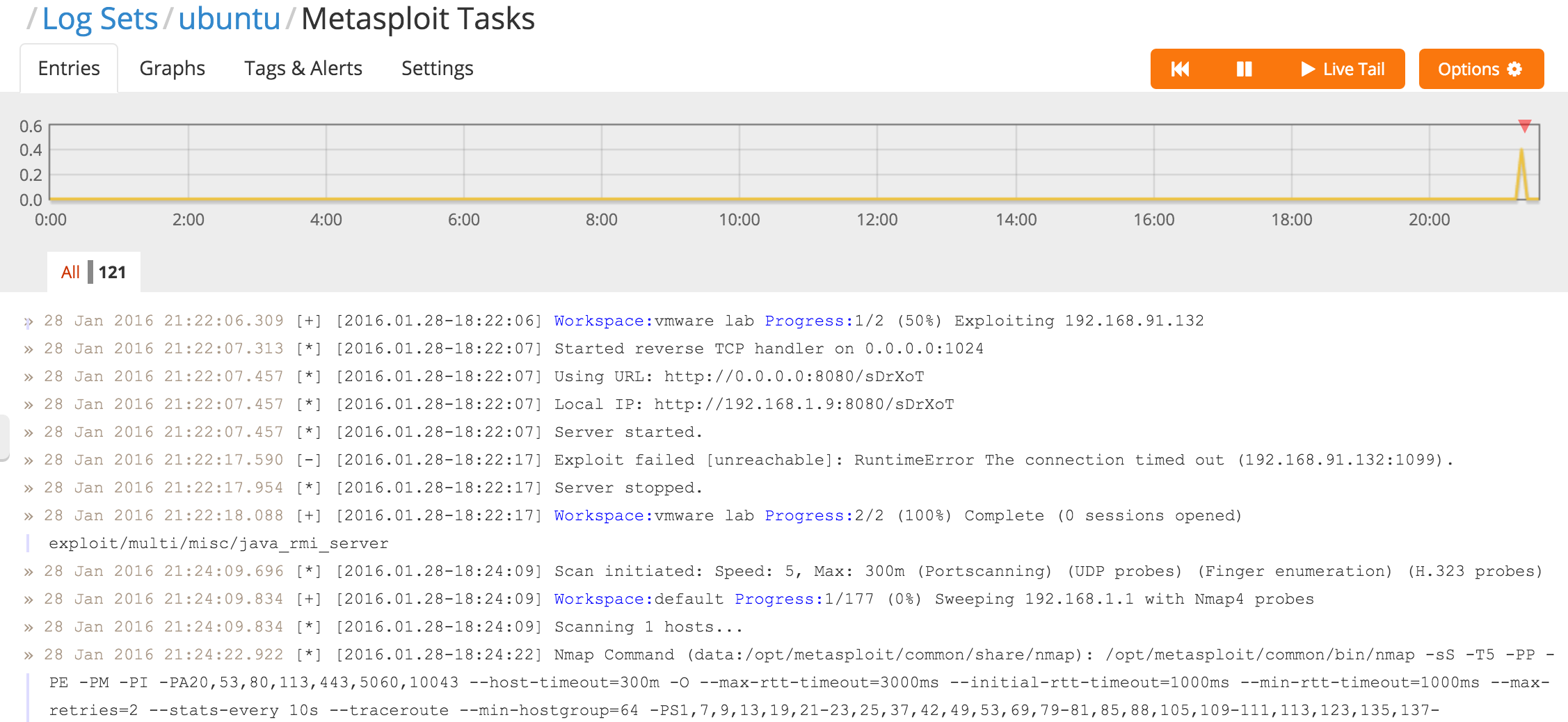
The tasks directory
The tasks directory provides text files detailing all of the actions taken by all Metasploit users. It will record any exploit that is run, the creation of a listener, establishment of a pivot, and any other action taken through the console.
Configure the Logentries Agent
To capture the log data saved to the tasks directory first ensure that you have installed the appropriate Logentries Agent on the Metasploit Console machine. The Logentries Agent can automatically identify and forward the newest log file written to a directory by using a wildcard configuration. For the Linux Agent issue the following command to follow the tasks directory:
sudo le follow '/opt/metasploit/apps/pro/tasks/*.txt'
and with the Windows Agent:
AgentService.exe follow c:\metasploit\apps\pro\tasks\*.txt
Always remember to restart the Logentries service after making changes to its configuration.
View in Logentries
Now as new tasks are written to the directory on your console server you can see them stream into Logentries in real time, creating an immutable offsite backup of these important audit trails.
framework.log
framework.log is your best friend when you are trying to troubleshoot an issue you are encountering with Metasploit. All the logged errors are saved here. When you dig into this log you will gain insight into which exploits failed, and for what reasons, as well as general stack traces.
Configure the Logentries Agent
In this case, because framework.log is just a single file, there is no need for special configuration. The command to follow this file with the Linux Agent would simply be:
sudo le follow /opt/metasploit/apps/pro/engine/config/logs/framework.log
access.log
The final log discussed here is the NGINX access.log produced by the Metasploit console. The information available in this log is imperative to maintain complete audit trails of all actions taken in the console. This log will contain every request made to the web interface including the ip address of the requester, making it invaluable in an investigation.
Metasploit's NGINX server is configured to log in combined log format, and as a result Logentries will be able to perform in-depth analysis on these logs with ease. The video below provides a tutorial on using the advanced search functionalities of Logentries to query an Apache access.log, all the same features and functionality will be available with this NGINX access.log.