Hey, I didn’t see you there (had my cameras and microphones turned off). Olivia here for week three of my month of extreme security diets for National Cyber Security Awareness Month. So far, I’ve taken Tod Beardsley’s advice for the most secure version recommendations, given it the ol’ college try (ie: decided some things were just not worth it), and netted out with a realistic version of the advice. Catch up on week one on maintenance here, and week two on travel and social sharing here.
For week three, I’ve taken on Privacy. “What does that even mean, Olivia?!” I imagine you’re shouting to your computer (my microphones are off, I can’t hear you, remember?). For the purpose of this diet, we’ve considered privacy to encompass location sharing, microphones, cameras, and taking a good, hard look at the sheer number of businesses who have my personal information (hint: woah).
Oh, the places you’ve been.
Before even volunteering for this experiment, I read this Fast Company article on anonymized location data. Let’s put aside the fact that if an attacker compromised my phone or car, location data would be just one element of the information about me they’d have. Unsurprisingly, even so-called “anonymous” location data still paints a pretty immediate and substantial picture of a life. Check out the article for just how easy it is to reverse engineer your whole life purely from the places you go.
For this week, I turned location data off entirely on my phone. Virtually all of my apps—LevelUp food-type apps, weather, Uber, ZipCar, sports, music, events, you name it—request location data, though many were already disabled. Most use location for the sake of personalization in the form of recommended concerts, food delivery area, local weather, etc. Social apps, as discussed last week, primarily use location for geo-tagging and geo-filters, although the marketing personalization is a factor there as well.
Google Maps, as a pedestrian in the city, was the most impactful for me this week. Like any sane person, you probably have location enabled at least here. (Should also note that I am notoriously bad at following directions, while somehow also overconfident in my directional instincts.) For the sake of science! I also tried to keep my goings-on normal—i.e., not avoiding things that would be complicated by having no idea where I was. Without it, I could still put in my location and destination and get standard directions in the form of a pirate map. However, like a ship on the high seas, I also had no actual idea where I was in relation to the ‘X’ if I took a wrong turn.
(pause here for my favorite pirate joke)
What’s a pirate’s favorite letter of the alphabet?
(pause for you to say “ARRRRGHHHHH,” my microphone’s still off, but hoping the outburst startled your neighbor)
Ahh, ya think it’s an ARRR but it’s really the SEA!
(pause for laughter, applause at my uncanny pirate accent)
Multiple wrong turns later, a kind friend commandeered the navigating with a location-enabled phone.
That said, the off-the-grid feeling that I got from knowing that none of my apps knew where I was combined with the plethora of “turn on location services” messages I got and ignored, felt goooood.
No photos, please.
Camera has a much shorter list of apps that request access—the obvious ones like Instagram and Snapchat, as well as several payment ones that use the camera to “scan” a credit card. Ease of use! Disabling camera was pretty low impact for me, but here’s a fun tidbit that muddies the waters on the location settings piece: privacy > camera handles how apps can use your camera, but location > camera handles whether your camera geotags all your photos. So even if your downloaded apps don’t use location or camera, the photos that you take can tell a location story as well. Just cancel that. (Ed note: if you’re interested in exactly how your stored photos can be used to track you, check out KrauseFx’s demo iPhone app).
Microphone’s list was shorter still—just Instagram, Snapchat, and Google Maps (voice commands?). I assume I’m not alone in noticing and reading about the creepiness of Instagram ads appearing immediately after having a verbal conversation about something, without any prior written mention/searches/clicks. In fact, it happened twice just days before beginning this exercise. Had a quick conversation about a meal delivery service and the exact service showed up in a friend’s Instagram feed, then later had an equally fleeting conversation about a personal shopping service and immediately got an ad for it that evening.
If the microphone targeting is that good/creepy, there’s no knowing what else is done with the other background conversations that aren’t identified as a product need/ marketing opportunity. It felt good knowing (thinking) that the microphone was off for the week, but definitely botched an intense carpool karaoke recording.
Unsubscribe.
Let me set the scene here by letting you know that prior to this week I had 35k+ emails in my personal inbox and 20k+ in my business email. I am neither a Categorizer nor am I (even close to) an Inbox-Zeroer, although I might argue that my inbox number has more zeroes in it, so who’s really winning?
Apart from the oxymoronic idea of a serene inbox, what are the security implications of having so many emails? Once again, it’s part preparation for worst-case scenario, and part thwart-the-evil-marketers. First, if your email is compromised, the more emails you have, the more material the attacker has to work with. Who emails you often, what kind of emails do you open and click on, what business do you conduct over email? All of these can be used to phish you—like fishing-with-an-f, attackers bait you into clicking/entering info by making a convincing replica of an email you’d expect to get. Boom, phish bait.
Second, the more emails you have the easier you are to market to. You’ve obviously subscribed to the communications that you receive from companies, and email clicks lead to more targeting around the internet and on other social media. Email services like Gmail also use all data collected while you’re logged into the Gsuite to target ads to you.
I am (admittedly, still working through) unsubscribing from email lists that I honestly don’t ever open. Deleting old ‘real’ emails, the ones with real information about me—not just where I like to shop or read the news—made a lower impact on my inbox number, but has an arguably higher impact on my security. While I don’t dream of having a skinny inbox in the foreseeable future… unsubscribing, deleting, and retiring anything older than two years is giving me that juice cleanse glow.
Backups and Downs
I promised that I would, as a demonstration of my commitment to this diet, factory reset my phone just for funsies/ to test my backups. Read more about why this step is important to your security maintenance back in week one. As expected, this was particularly nerve wracking—which is maybe a good indicator of how important it is to test your backups.
First, despite automatically backing up to iCloud the night prior, I did a manual back-up and logged into iCloud on my laptop to check on my contacts and photos especially. Still, the anxiety of tapping “erase all data and settings” and “are you sure?” and “P.S. this is permanent” and “enter your password so we really know you’re doing this on purpose” was akin to jumping out of a perfectly good airplane just to use a parachute (except I’d much rather do that again than this). Riding the high of adrenaline from the reset, started getting into the meat of the backup process...
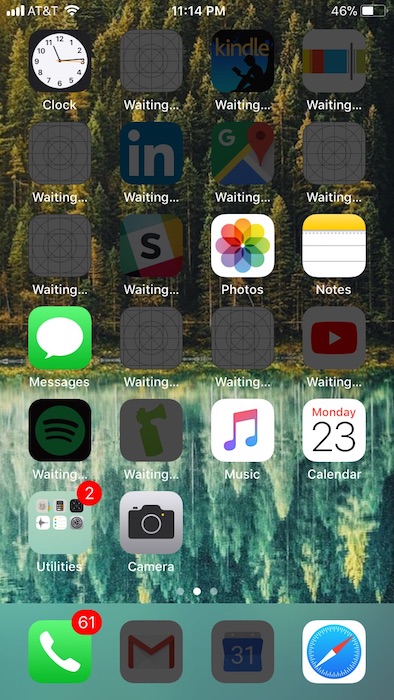
Learn from my mistakes
- When asked to create a password, I just entered my previous password. Bad idea. When I got to the decrypting my iCloud passwords step, my old iPhone password was required. Since my new and old password were the same, the poor little guy got very confused and I had to RE-reset. Two resets later, the “enter old iPhone password” is still getting tripped up.
- Wouldn’t recommend using this downtime for teeth whitening. You /will/ want a very large glass of red wine.
After I got through the steps of the restoration, it was just a wait-and-see as all my apps and data downloaded. Woke up several times during the night to check on it, continued panicking that my photos were the absolute last thing to appear, and yes, I do have 61 missed calls/voicemails. In the AM, opened Spotify (already logged in!) and had a quick celebration dance break that all my apps, texts, and photos were right where I left them. Take-away: as a key exercise, but something that’s definitely not for the faint of heart, consider this the cardio portion of the security diet.
Pop Quiz, Hot Shot
You don’t have to be going 50 mph+ to take it, in fact, it’d probably be safer if you weren’t. Your call, but speaking of speed, the quiz is super fast and word on the street is that Keanu is phish bait. Take our How Hackable Are You quiz here, in partnership with NBC’s The Today Show, to see how you compare. I’m a discerning technologist, nbd, no photos, please.