The most vulnerable moment for attackers is when they first gain internal access to your corporate network. In order to determine their next step, intruders must perform reconnaissance to scout available ports, services, and assets from which they can pivot and gain access to customer databases, credit card data, source code, and more. These initial moments are arguably your best opportunities to catch attackers before critical assets are breached, but unfortunately, it can be very challenging to detect them at this stage of the attack chain.
In this post, we’ll walk you through why this is a pivotal moment and how to detect and investigate attacker reconnaissance in our SIEM solution, InsightIDR.
Reconnaissance and deception: Tracking their every move
The moment attackers gain internal network access, their next objective is to scan for promising next steps—any way that allows them to pivot toward valuable assets. Or, perhaps they’ve been able to install malware that allows for remote command and control. Either way, they’re looking for an easy way to secure privileged and persistent access to your network.
This is also the most crucial time for you to find them, when they’re exposed and before real damage is done. An increasingly popular countermeasure is to deploy deception technology, like honeypots. A honeypot is a machine that sits on your network, waiting for a connection request from an attacker. In order to lure attackers, these dummy machines may be set up with vulnerabilities or default configurations to make them an easy, appealing target.
When attackers reach out to the honeypot, either when scanning the network or attempting access with stolen/default credentials, they end up only activating your tripwire. The moment the honeypot detects a network scan, it generates an alert to your team while simultaneously misinforming the attackers, leading them to think they’re still in the system executing their plan.
To show you how this works, we’ll use our deception technology inside InsightIDR as an example. The below investigations page shows alerts generated from our deception suite, which includes honeypots, honey users, honey credentials, and honey files.
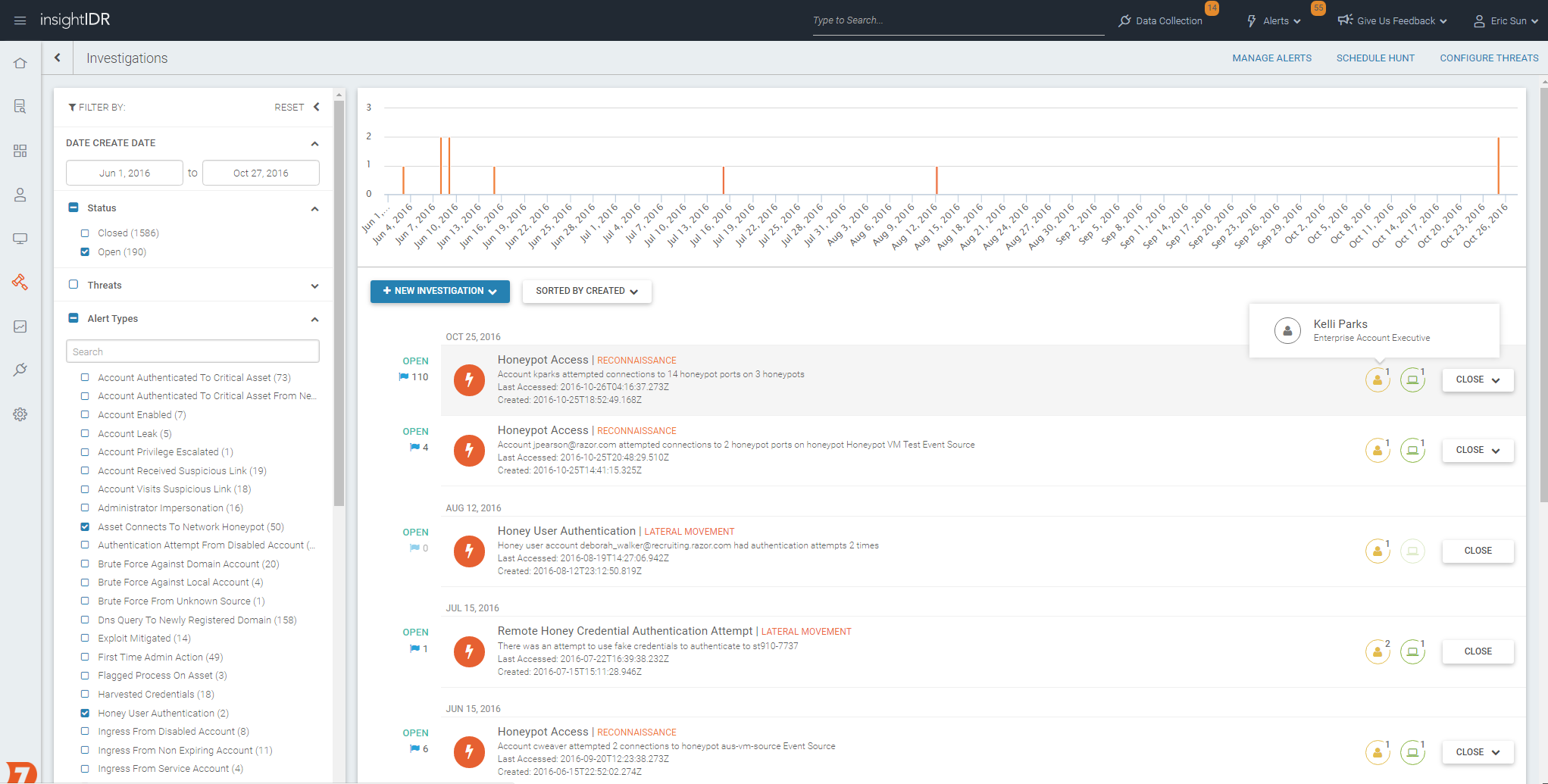
In our InsightIDR interactive product tour, you can learn about the different layers of deception, which work together to detect stealthy behaviors that often go unnoticed with log analysis alone.
Gather alerts in context
Attackers often succeed because they’re skilled at covertly sneaking in through bypassing common alert thresholds. With the rich level of data collection in InsightIDR, you’ll be able to track malicious behavior across the attack chain.
Each time you investigate an alert in InsightIDR, notable user and asset behavior is automatically highlighted so you can see what affected users were doing around the time of the alert.
In this example, a honeypot alert triggered on both March 27 and March 30. Since these alerts involved the same user, the data is automatically correlated. Here, you can see step-by-step what an attacker was trying to do, where, and when, giving you access to all notable behavior in one view. For example, you see above that a few virus alerts were triggered, as well as a connection to another country. You can also see what happened before and after each of these events to give you a more complete picture. Once the honeypot alert is triggered, this information is displayed in the visual timeline, accelerating the investigation and helping to make sense of the attack faster.
Because attackers often steal credentials and impersonate company employees (or privileged service accounts), it’s important to see activity across a user’s endpoint, network, and even cloud services. Through the user profile pages in InsightIDR, you can easily drill into any user in your organization.
Event activity, like if the user clicked on a spear phishing URL or if that user’s password was breached, is reported in the profile so you can trace back how the account may have been compromised and what happened before and after. Every employee’s behavior is automatically baselined using user behavior analytics, helping you quickly pinpoint suspicious activity that may indicate a user account has been compromised.
Profiles also include details on the user’s endpoint, which InsightIDR collects in real time via our included Insight Agent. This includes visibility into all running processes and local authentications, and helps expose insider threats and shadow IT, programs installed without IT oversight.
Generate evidence to round out your case
Like any good investigator, you need to have sufficient and accurate information in order to take action against the offender. The InsightIDR investigation interface includes an evidence pane which provides more context, such as the port, type of traffic, and IP address associated with the traffic.
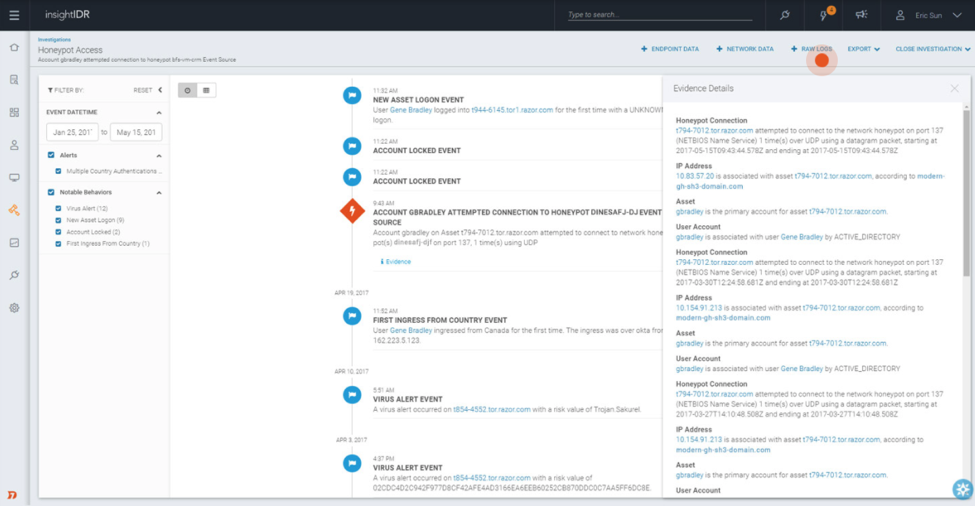
Viewing data from multiple endpoints in your network helps you see the full picture, and with InsightIDR you can query your endpoints in real time, as well as search across network data and raw logs. With easy access to this information, your team can make faster, better decisions.
Digging deeper with contextual data
Having the right information, presented in the right way, is the key to a fast and accurate response. An automated timeline that combines data from all endpoints and users into a single view can give you deep,rich insights that show you the who, what, when, and where of a potential attack so you can more effectively put a stop to it.