No matter whether you're taking your first steps with Metasploit or if you're already a pro, you need to practice, practice, practice your skillz. Setting up a penetration testing lab can be time-consuming and expensive (unless you have the hardware already), so I was very excited to learn about a new, free service called Hack A Server, which offers vulnerable machines for you to pwn in the cloud. The service only required that I download and launch a VPN configuration to connect to the vulnerable machines. Since I already had my Metasploit instance set up on BackTrack, it only took minutes to get started. Once you're up and running, you can choose from a large number of vulnerable machines, including Metasploitable.
This How-to will use BackTrack5 R3, which is available from backtrack-linux.org, but you should also be able to use any other Linux distribution. I did not see any way on the Hack-A-Server website to get their VPN client working on Windows, so I'd recommend you stick to Linux. I already pre-registered my version of Metasploit on BackTrack for the quick penetration test in the latter part of this post. If you need help, check out this blog post on activating Metasploit on BackTrack5 R3.
If you'd like to use the service, go to Hack A Server's website and sign up for a free account. Once you're signed up, choose Training Area in the toolbar:
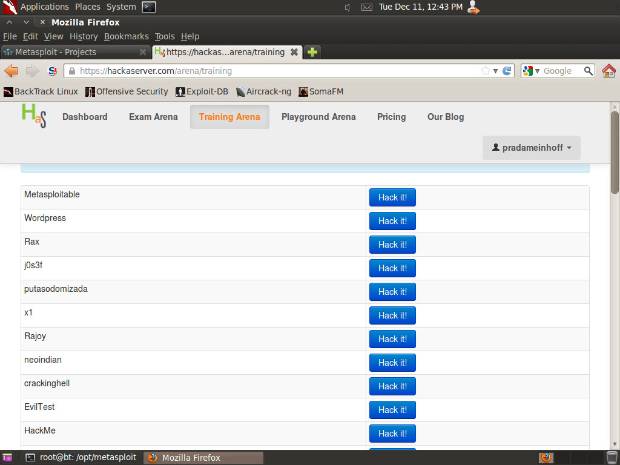
As you can see, they have a ton of vulnerable machines available on the service. For the purpose of this test, we're going to choose Metasploitable. Click on the Hack it! button.
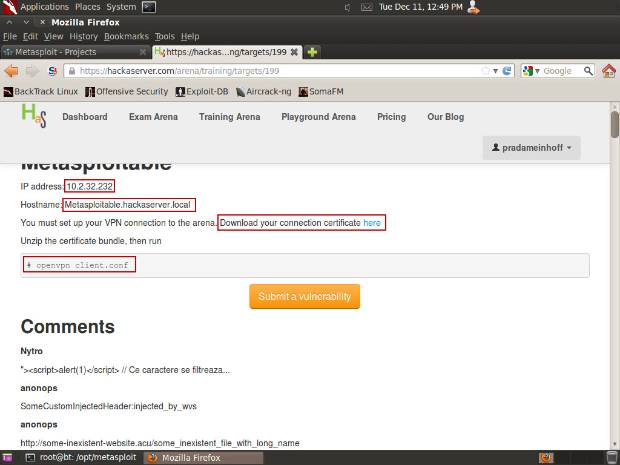
Download the connection certificate to root, then run the following commands:
unzip pradameinhoff-connectionpack.zip
openvpn client.conf
Note: The zip file will have a different name (pradameinhoff is my username on HackAServer.com). Type ls to view how it looks in your directory.
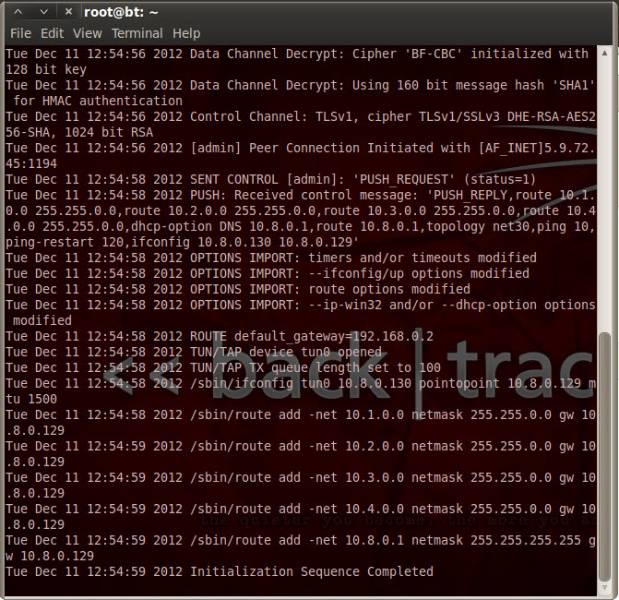
If your VPN client has started correctly, you should now see something like this on the screen:
Open a second terminal window and ping the Metasploitable server on 10.2.32.232 (this was listed on the HTML page earlier).
ping 10.2.32.232
You should be seeing something like this on your screen:
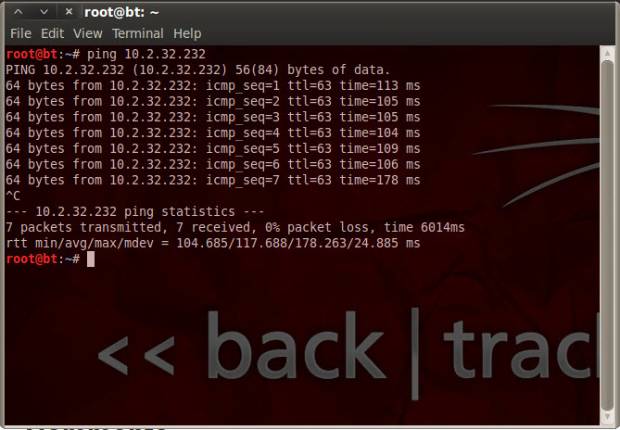
This proves that you have a network connection to the Metasploitable machine. Congratulations!
Now let's exploit the machine with Metasploit Pro:
- Open your Firefox browser to https://localhost:3790
- Go into the default project and click on the Scan button. Enter 10.2.32.232 and click Launch Scan
-
Once the scan has completed, go to the Analysis menu and choose the Hosts option. You should now see the host in the list:
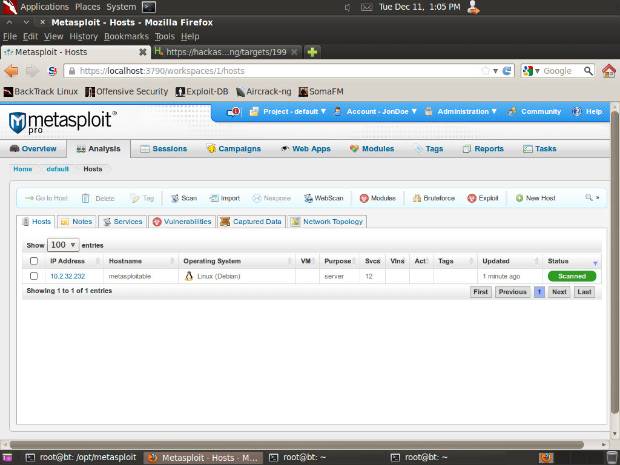
- Select the checkbox next to the Metasploitable machine and click the Exploit button in the toolbar.
-
On the next screen, click Exploit on the bottom right:
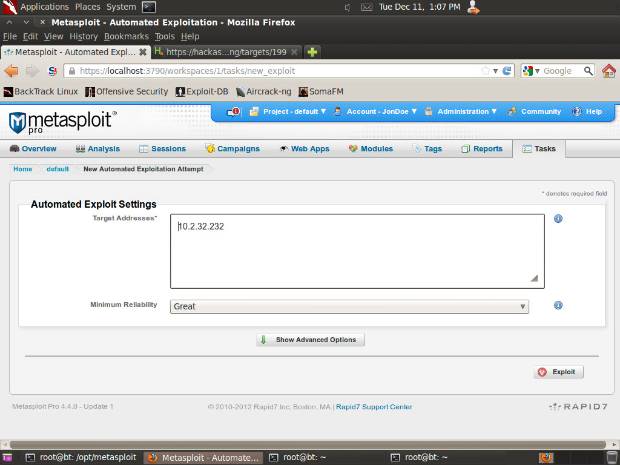
- Metasploit Pro will now match up the right exploits with the operating system and services fingerprinted on the Metasploitable machine and then launch the smart exploitation process. For Metasploitable, it will likely be successful with exploit/unix/misc/distcc_exec. (If you are using Metasploit Community, you can manually choose this exploit since this edition doesn't support the smart exploitation process).
-
Once the smart exploitation process has completed, click on the Sessions button in the toolbar. You should see one open session:
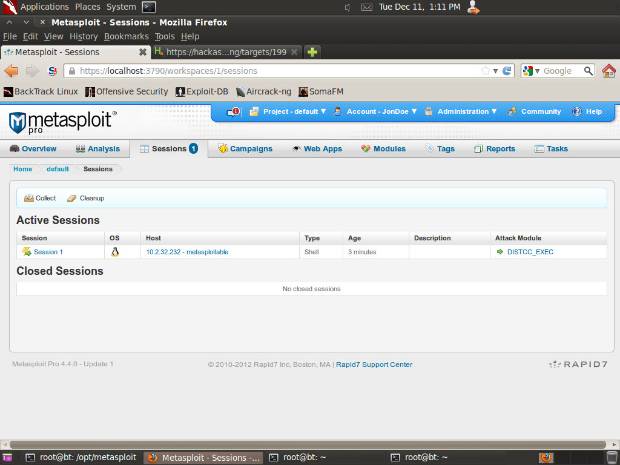
-
Click on Collect, check the box next to Session 1, and click the Collect System Data button on the bottom right.
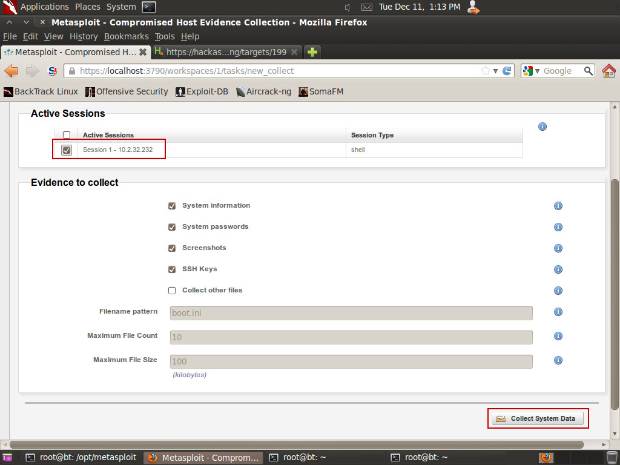
-
Metasploit Pro will now collect passwords, screenshots, and other evidence from the machine. Going back to the Hosts screen in the Analysis menu, you'll see that the machine is marked as looted:
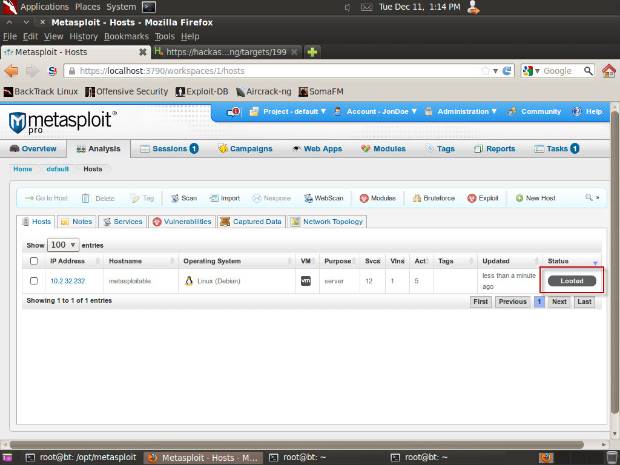
Congratulations again - you've compromised your first machine. Now you can also check out some other vulnerable machines on the same network, which you can also reach through the same VPN connection provided by the Hack-a-Server website.
I'd be interested to hear how you find the service and whether it worked as seamlessly for you as it did for me. Please log in and leave your comment below!