Easily share these animated iOS Security tips with friends and relatives!
While iOS is generally considered to be quite secure, a few configuration items can improve its security.
Some changes have very little functionality impact, while others are more visible but probably only needed in specific environments.
This guide contains some of the most important, obvious ones, and contains a GIF for each configuration step to be taken.
If you already know everything about iOS security, use this as a way to easily explain to friends and relatives how certain configurations are changed. As most of our readers are in the security field, we actually expect this to be more useful as a way for you to help your friends and relatives.
Why GIFs?
- They are awesome.
- They can lead to entertaining discussions about why it is wrong to pronounce GIF with a soft G.
- Because while you, awesome reader, may know how to perform these configuration changes, you may not know the steps by heart or want to walk your friends through step-by-step. Just re-gif these! (Pun intended. I am sorry).
Steps
Do not Jailbreak it
This is our first step, and we are already cheating. There is nothing for you to do.
While jailbreaking can be very useful for testing the security of iOS applications or iOS itself, jailbreaking a "day to day" phone is dangerous, as it disables many of the protections of iOS.
Software Updates
iOS
iOS will regularly check for new versions, but if this is a new device, or one that hasn't been used in a while, you should check manually.

Application Updates
Applications need to be updated too. Sometimes for bug fixes, and sometimes for security patches.
Fortunately, iOS allows automated patching, making it painless.

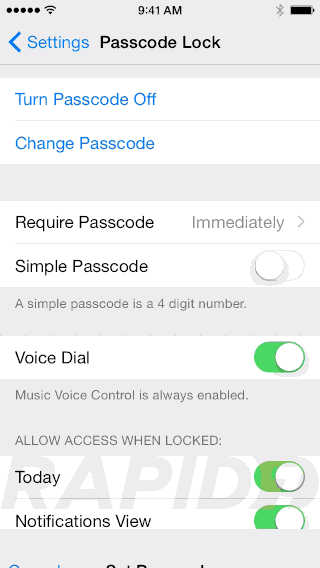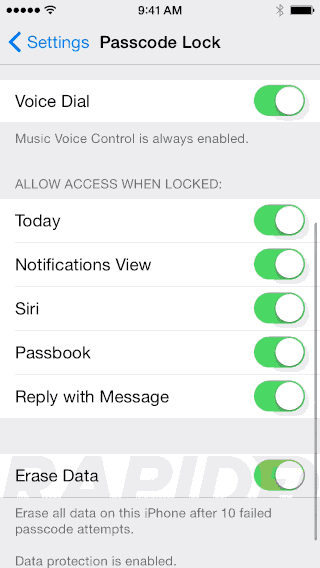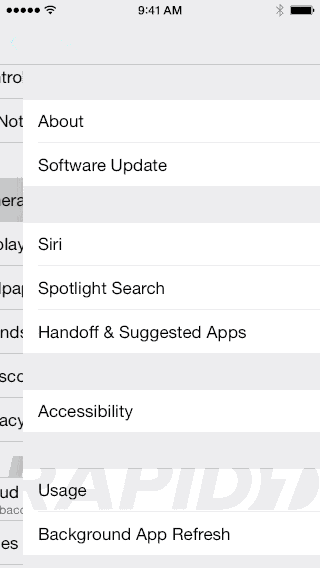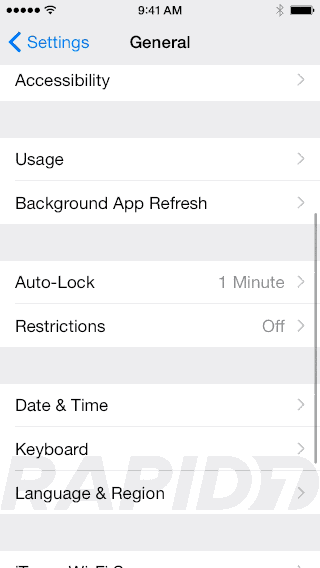
Give it a good passcode, enable auto-lock and “Erase Data”
Note: If your phone is TouchID equipped, using a longer password with different types of characters can add security without being too painful, as you will rarely use the password.
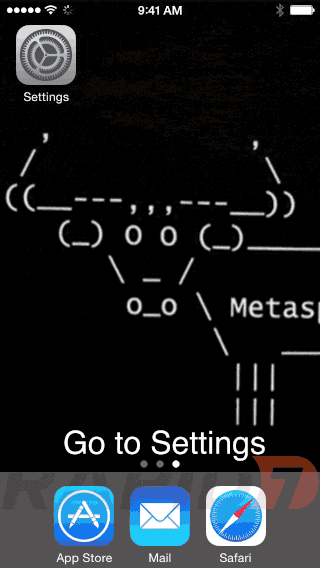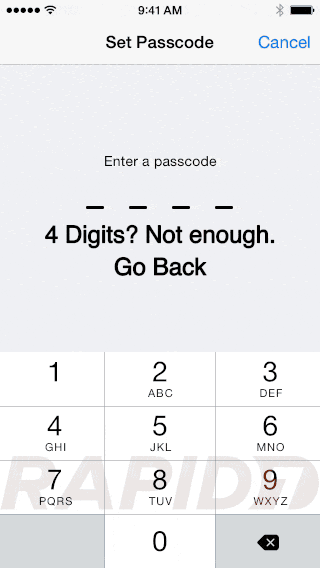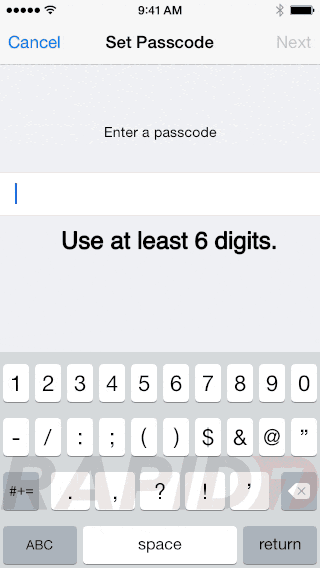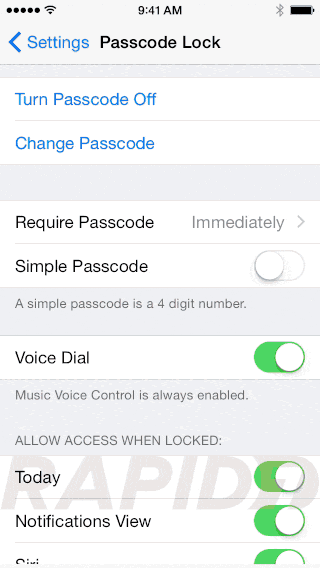
I personally set auto-lock to lock my devices instantly, because with TouchID allows me to unlock it so fast.
I know that if I forgot my phone on a table or in a cab, I would feel better knowing there was no time window where someone could snoop through my stuff easily.
The "Erase Data" feature ensures that the phone is wiped after too many failed attempts.
WiFi
WiFi: Ensure WiFi doesn't ask to join potentially insecure networks
iOS has an option to prompt you to join networks automatically. Let's make sure it's off.

Safari
Safari has various options to request that sites do not track you (which sites may or may not honor), to only accept cookies from the site you are visiting and more.

Additional privacy measures can be taken with Safari, such as ensuring search engine suggestions are not used, that the top hit is not reloaded and more. These have an impact on usability and are more subtle in the protection they provide.
While storing passwords in a browser is typically a bad idea, we recommend that you read this article by Rich Mogull before dismissing iCloud Keychain completely. It certainly beats not using a password management tool at all.
Find my iPhone
A lost phone can mean having to buy a new one, and we know these devices are expensive. It can also mean someone has access to your data, email account and more.
By having a good passcode on your phone, you greatly limit the odds that someone who found your phone could use it.
By enabling Find my iPhone, you can make sure that they can't wipe it and enable it for themselves and you can display a message on the screen, asking the person who found it to contact you.
Two settings exist for Find my iPhone. The first one enables it, which is very simple. From that moment, you can login to iCloud to set your phone as lost, and see its location and send a message to it. Apple receives the device location when that lost mode is enabled.
The second option allows your phone to send its location before running out of battery. This can be very useful if you lose your phone in a location where nobody finds it, and it runs out of battery before you notice.
Be aware that enabling that second option means Apple will receive the phone's location even when you have not set it as lost yet.
Edit: As mentioned by reader @ClausHoumann on Twitter, network connectivity is required for Find my iPhone to work. This means that if you are traveling without a data plan and roaming enabled (because it is expensive in a lot of areas), Find my iPhone will not work. It will still prevent activation of your phone. Thank you Claus!

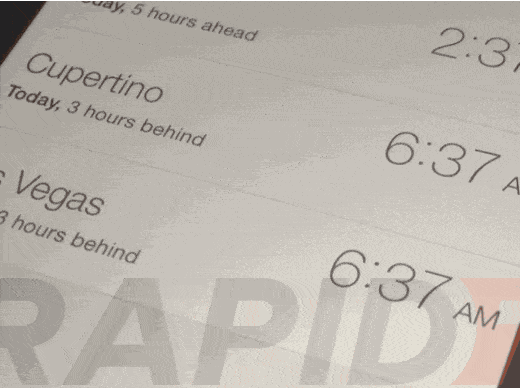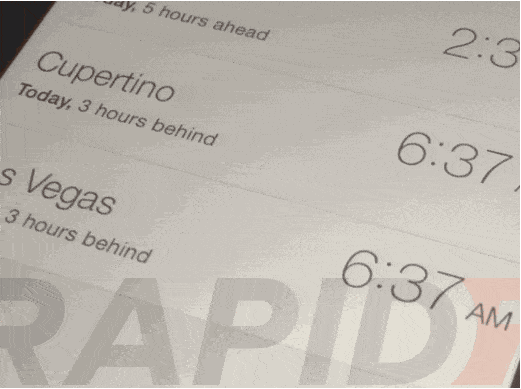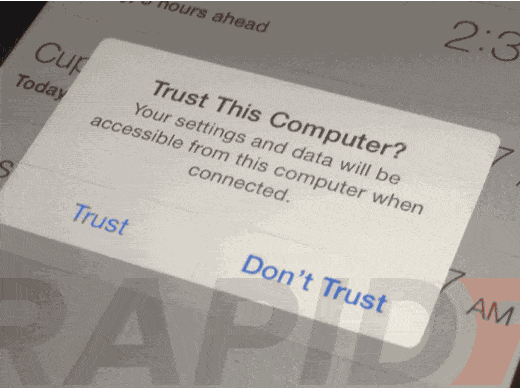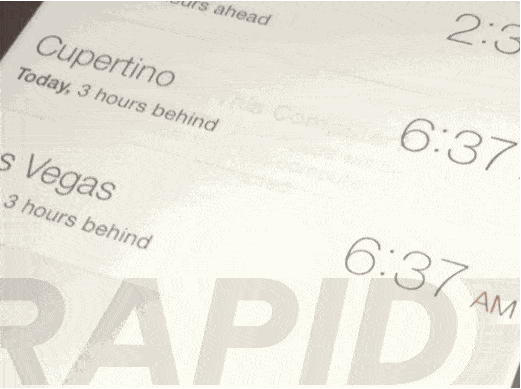
Never trust computers or devices you do not own
If you ever connect your phone to a device you do not own, and see this screen, never trust it.
If you have trusted a device or computer by mistake, follow the steps in this knowledge base article to remove the trusted relationship from your iOS device.
Trusted devices can access data on your phone to back it up, sync data to it. Only your own computer should be trusted by your phone.
Note: Charging your phone on an untrusted computer, or even a USB charger that is not yours can carry some risk. If you see this prompt when using what should be a "dumb" USB charger, consider it suspicious.
If you are at a security conference, do not trust any USB charger provided by people with black t-shirts.
Avoid receiving images from weird strangers during your commute
AirDrop is very useful, but if left open to everyone, can lead to [bizarre interactions](/blog/(http:/www.theverge.com/tldr/2014/11/10/7171345/the-best-use-for-apple-airdrop-is-space-sloths).

Enable iCloud "Two-Step Verification"
Last, but not least, ensure you enable this feature on your iCloud Account.
For this last recommendation, we cheat and do not provide a GIF. Simply go to Apple's Knowledge Base for more information.
Enabling this will require you to link your trusted iOS device(s), and to provide a 4 digit PIN sent to one of them when you login to iCloud or AppleID related services.
This will significantly reduce the odds of bad things happening to your iCloud account, data or devices linked to iCloud if your password was compromised.
Save your Recovery Key safely, as if you lose it and your password or devices at the same time, you might be in trouble!