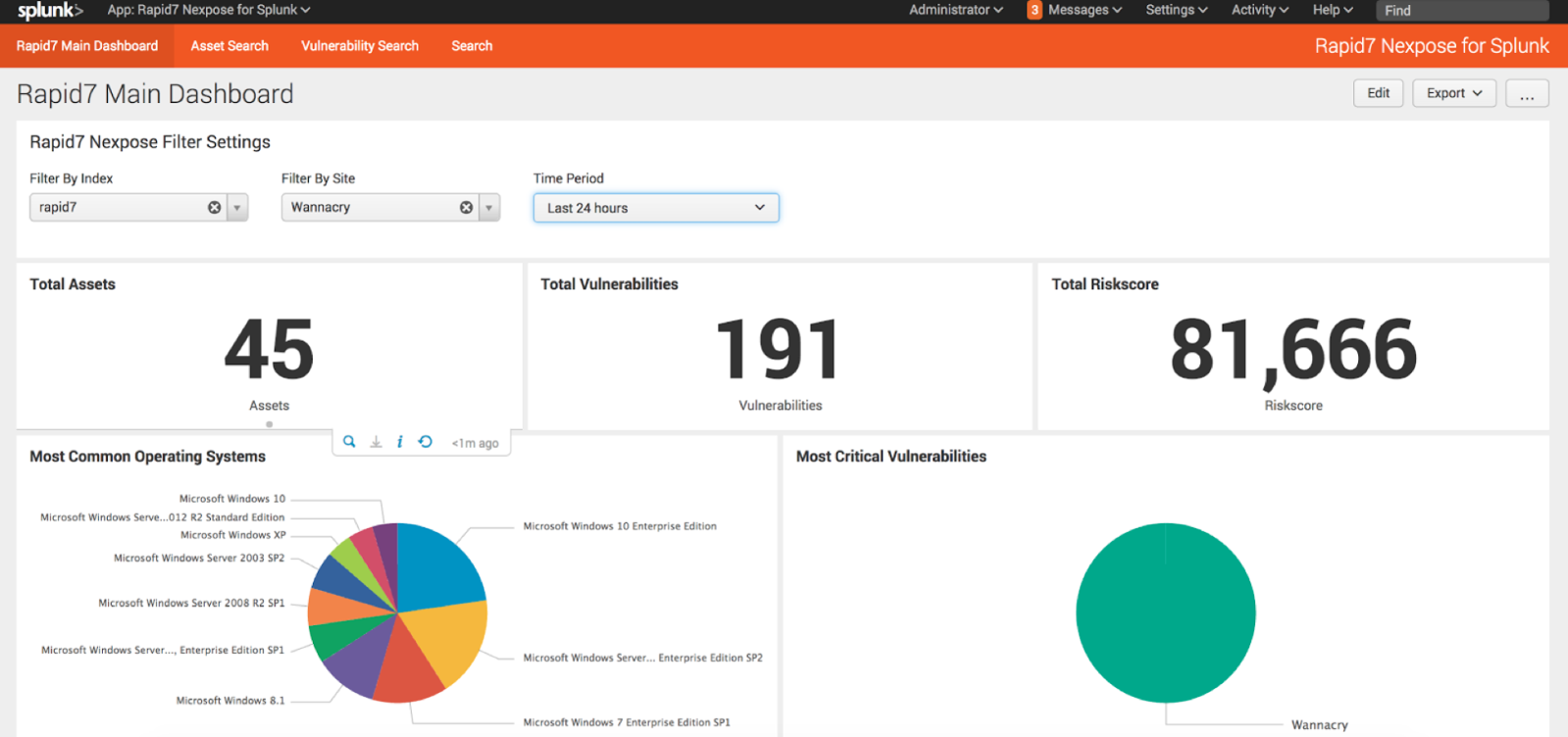
Do you want to see your WannaCry vulns all in one dashboard in Splunk? We've got you covered.
Before you start, make sure you have these two apps installed in your Splunk App:
Steps
1. Follow the directions in this blog post to create a custom scan template.
2. Scan your targets with the scan template as shown in the blog above.
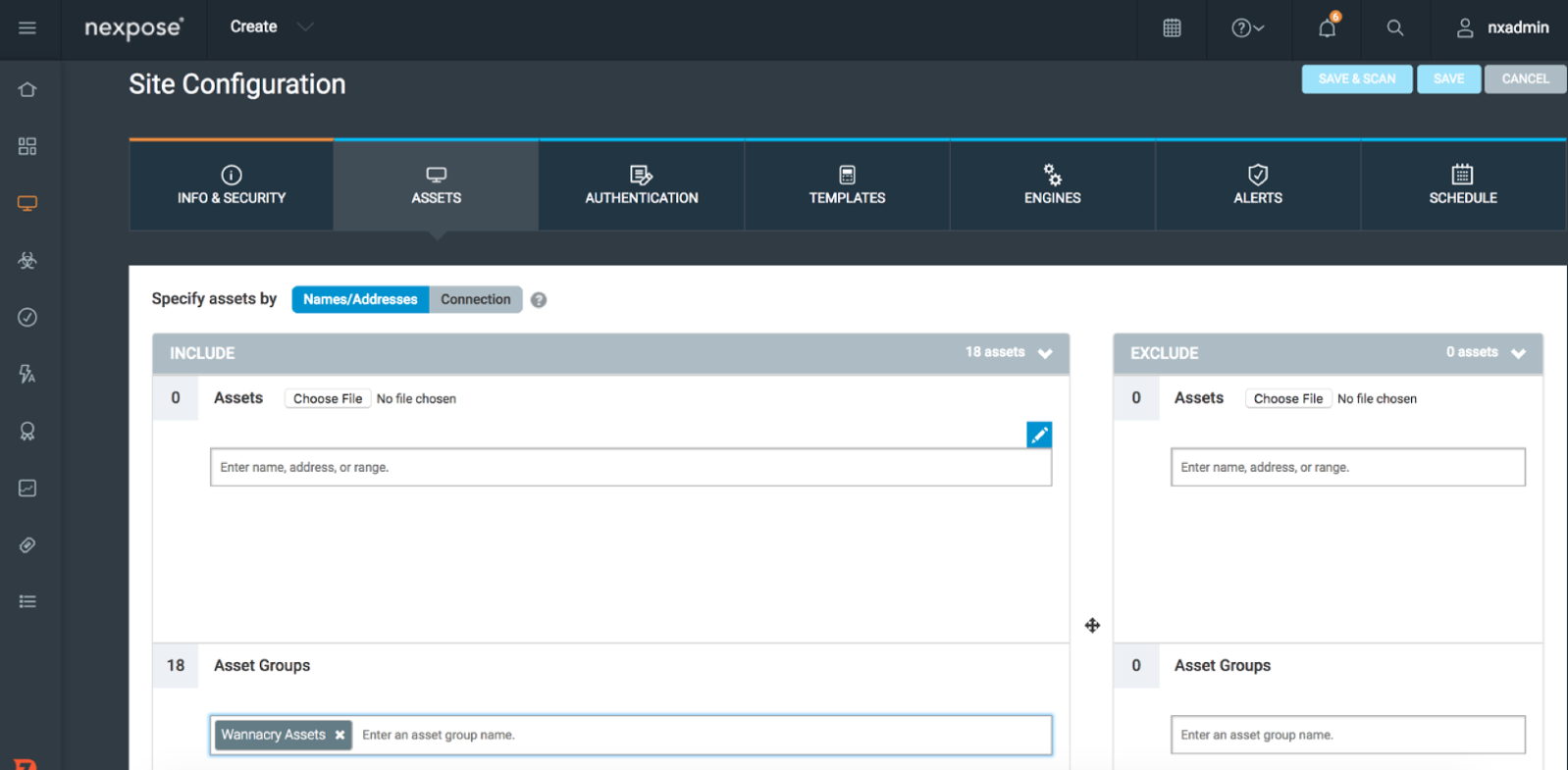
3. Create a Dynamic Asset Group (DAG) containing the 8 CVEs (as shown in the blog post). In this example I called the Asset Group “Wannacry Assets.”
4. Create a Site in InsightVM or Nexpose, for Assets use Asset Groups and select the DAG you just made.
5. Let your InsightVM or Nexpose to Splunk sync occur (this happens at 4am by default).
6. Use Filter on Rapid7 Dashboard to pick that site! In this example I called the Site: Wannacry.
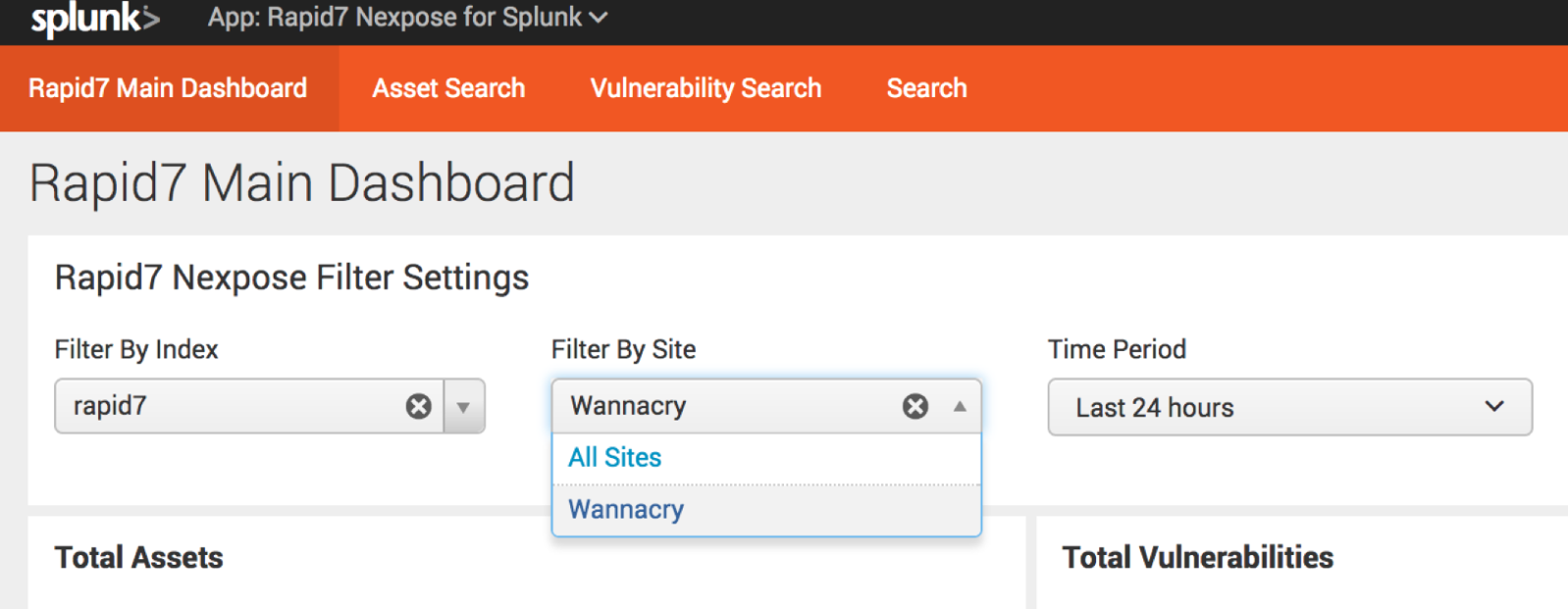
And there you have it: a dashboard of your WannaCry vulns in Splunk, as found by Nexpose or InsightVM. You can also export the dashboard as a PDF report if you would like to share it. Not a customer of ours? Download a free trial of InsightVM to get started.
If you're a Splunk customer concerned about security, we can help. InsightIDR, our incident detection and response solution, uses your existing data sources—including Splunk—to identify stealthy attacks and prioritize risk across your environment. Discover how InsightIDR can help your team solve multiple security use cases without worrying about rising data costs or maintaining custom rules and queries.
