This is the third in a three-part series discussing common threats, key data sources, and how the Rapid7 portfolio can help you secure cloud environments. Be sure to check out Part 1, “Securing Your Cloud Environments with InsightIDR, Part 1: Microsoft Azure” and Part 2, "Securing Your Cloud Environments with InsightIDR, Part 2: Amazon Web Services (AWS)."
As companies continue to move more of their infrastructure and software into the cloud, their security teams are tasked with a new set of challenges. With a growing threat surface, they now need visibility into disparate environments, the ability to detect attacks and anomalous behavior, and the means to ultimately respond.
In this post, we’ll show you firsthand how helps teams accelerate their response to cloud-based threats.
Accelerating the investigation of compromised credentials with SOAR
One of the most common attacks targeting cloud environments is compromised credentials. As an organization, you may be seeing a multitude of events that could indicate compromised credentials, but each of these events requires varying levels of triage and investigation before you can ultimately respond to them. Combine that work with everything else your team is balancing, and it’s easy to see how these types of incidents fall through the cracks.
To illustrate how SOAR can accelerate your team’s response time to this kind of attack, we’ll look at an automated workflow that leverages the new integration between Rapid7’s security orchestration and automation (SOAR) solution, InsightConnect and AWS’s Security Hub.
First, you or a member of your team receives an alert in Security Hub notifying of a user adding a highly permissive policy to themselves and essentially escalating their privileges. This alert alone may not be enough to immediately quarantine the account, but it definitely warrants an investigation.
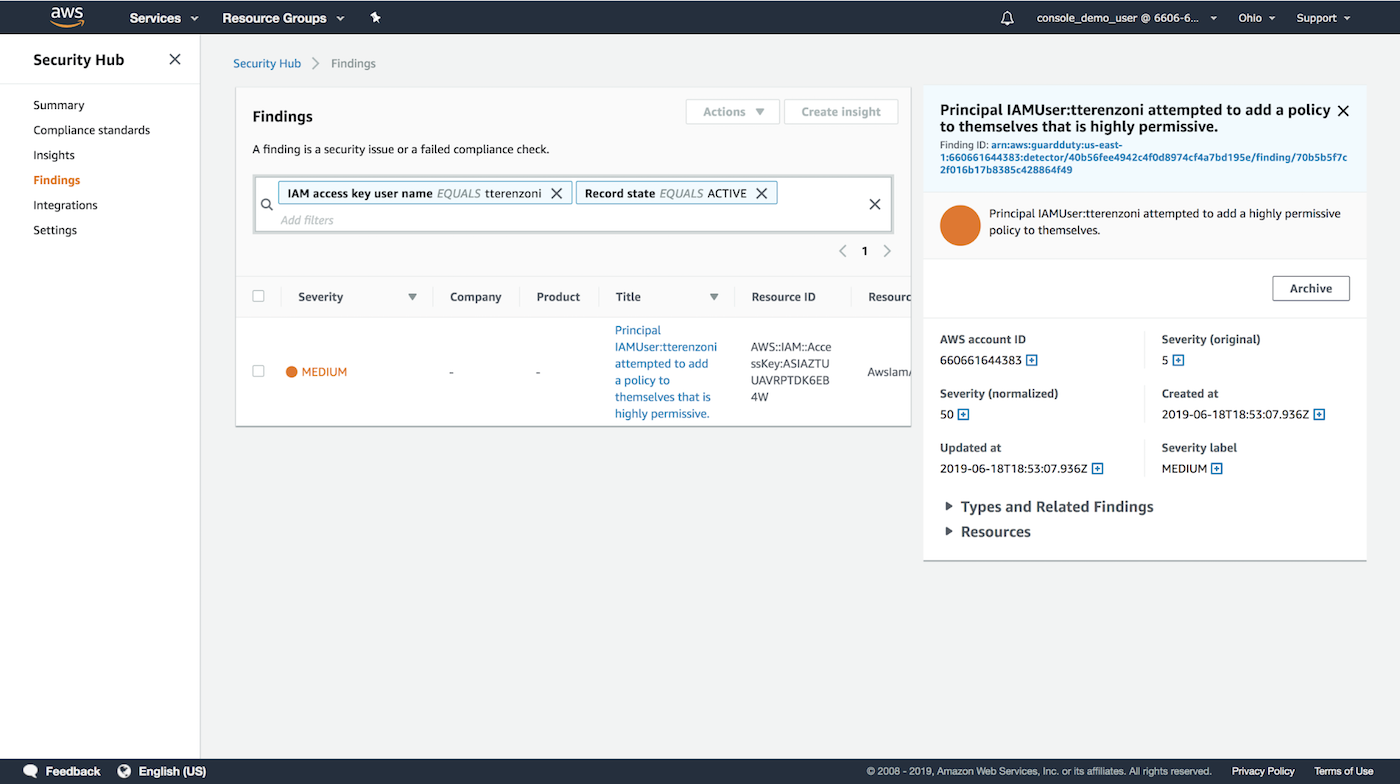
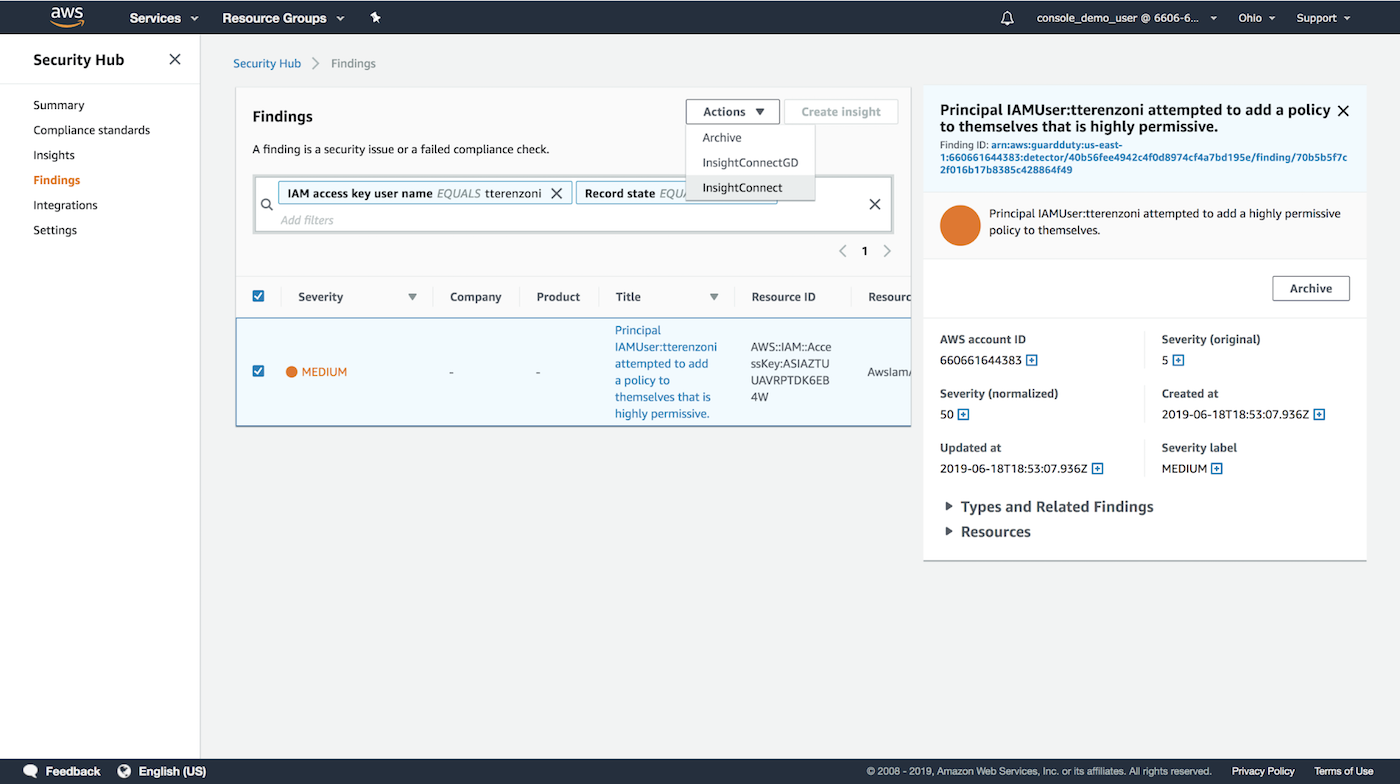
Leveraging InsightConnect’s integration with AWS Security Hub, you can easily kick off an automated workflow for this investigation right from the Security Hub console.
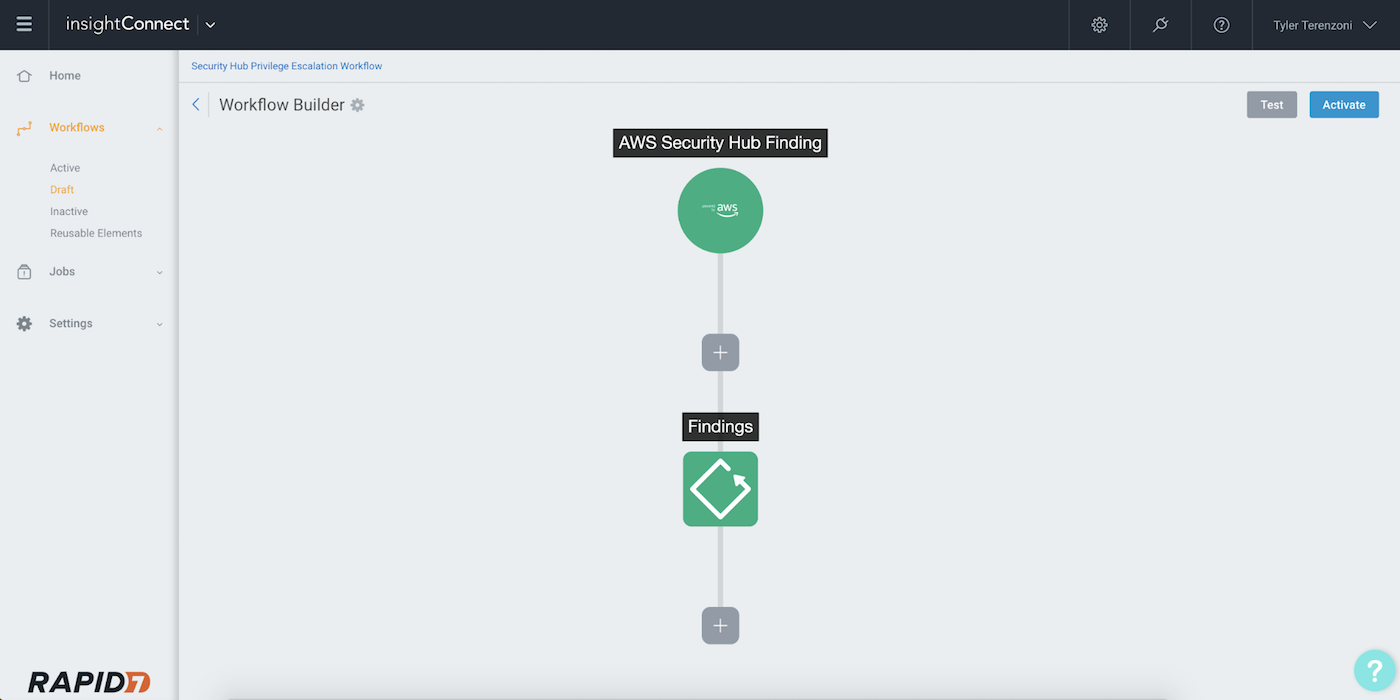
Let’s dive a little deeper into the workflow. Sending the Security Hub finding to InsightConnect will trigger the workflow which, in turn, will start evaluating the details of the finding. The goal of the workflow is to enable employees within your organization to become an extension of your security team by utilizing the InsightConnect ChatOps feature and using the feedback provided by the user as an enrichment source to power decisions in the workflow.
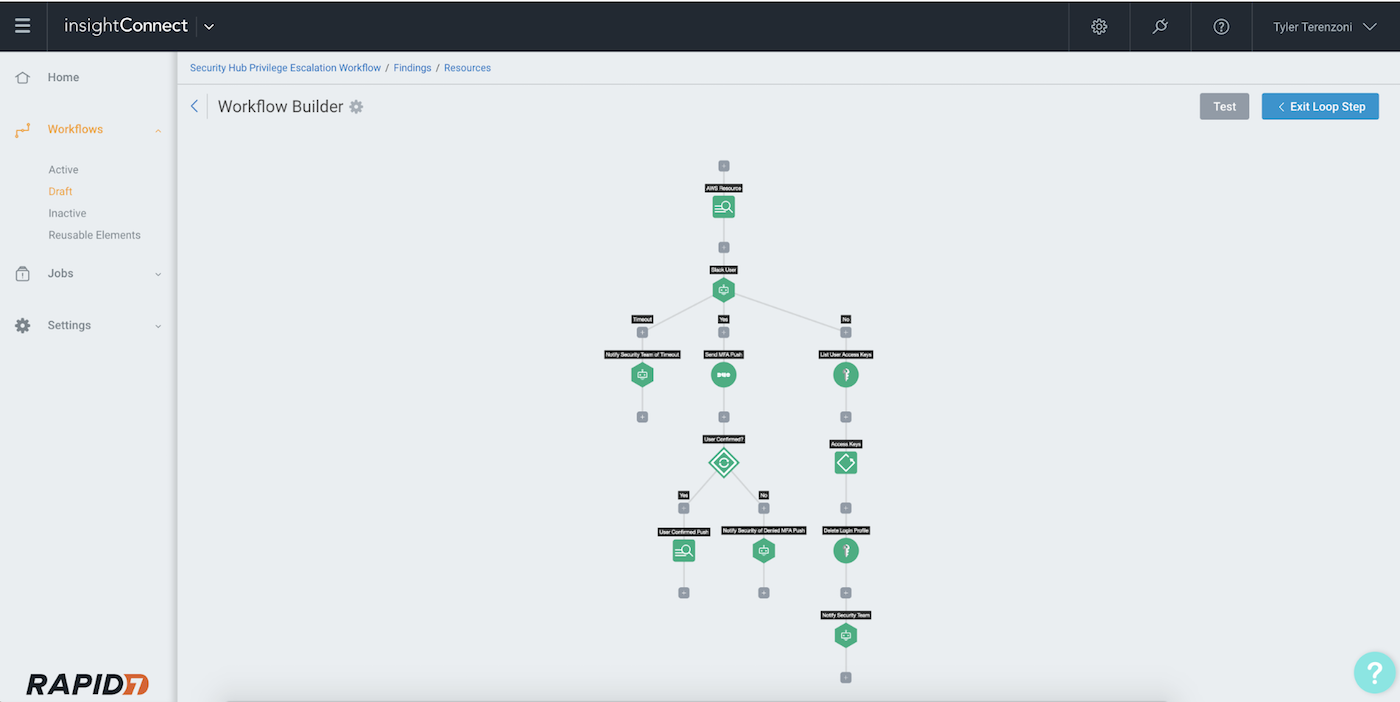
For the finding that we are evaluating, InsightConnect can parse out details of the event, including the username of the account in question. Using the ChatOps feature, InsightConnect can now message the user with details of the event and ask them to confirm or deny the activity that was seen as abnormal.
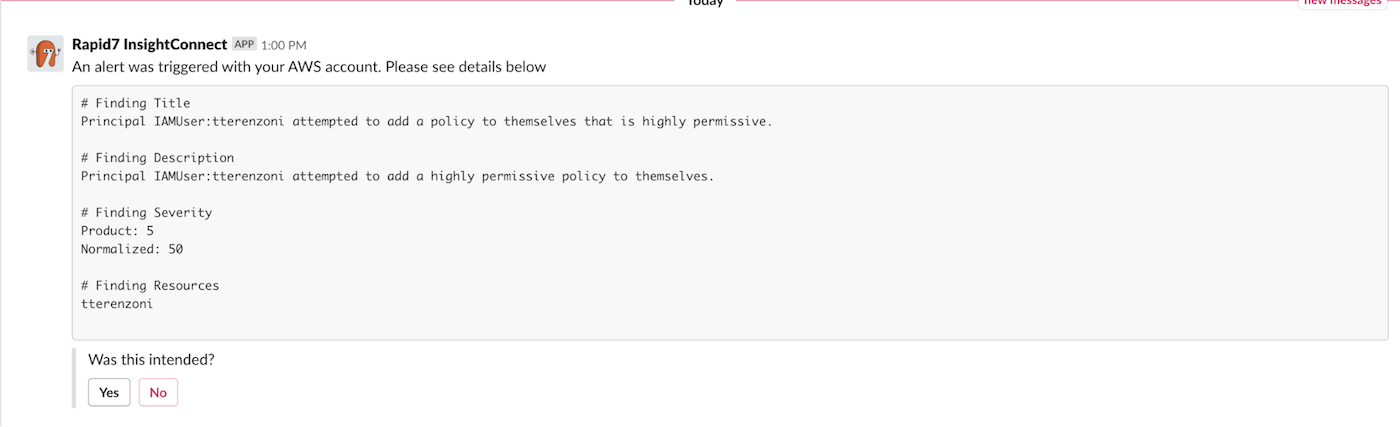
If the user responds that the event was them and was intentional, the workflow will send them a multi-factor authentication (MFA) push to confirm their identity and the incident will be closed. If they decline the event, the workflow will disable the user’s console access to AWS, as well as any additional access keys they might have. It will then notify the security team of the threat.
If the user does not respond to the Slack query, the security team will be notified.
Takeaways
This is just one example of how InsightConnect’s integration with AWS Security Hub can help you secure your AWS cloud environment. And did we mention that all of this automation can be done without anyone from the security team getting involved?
By sharing Security Hub findings with other systems and triggering automatic reactions to specific types of findings, InsightConnect ensures SecOps teams have the complete picture without getting bogged down responding to alerts.
