More context and customization around detections and investigations, expanded dashboard capabilities, and more.
This post offers a closer look at some of the recent releases in InsightIDR, our extended detection and response (XDR) solution, from Q4 2021. Over the past quarter, we delivered updates to help you make more informed decisions, accelerate your time to respond, and customize your detections and investigations. Here's a rundown of the highlights.
More customization options for your detection rules
InsightIDR provides a highly curated detections library, vetted by the security and operations center (SOC) experts on our managed detection and response (MDR) team — but we know some teams may want the ability to fine tune these even further. In our Q3 wrap-up, we highlighted our new detection rules management experience. This quarter, we've made even more strides in leveling up our capabilities around detections to help you make more informed decisions and accelerate your time to respond.
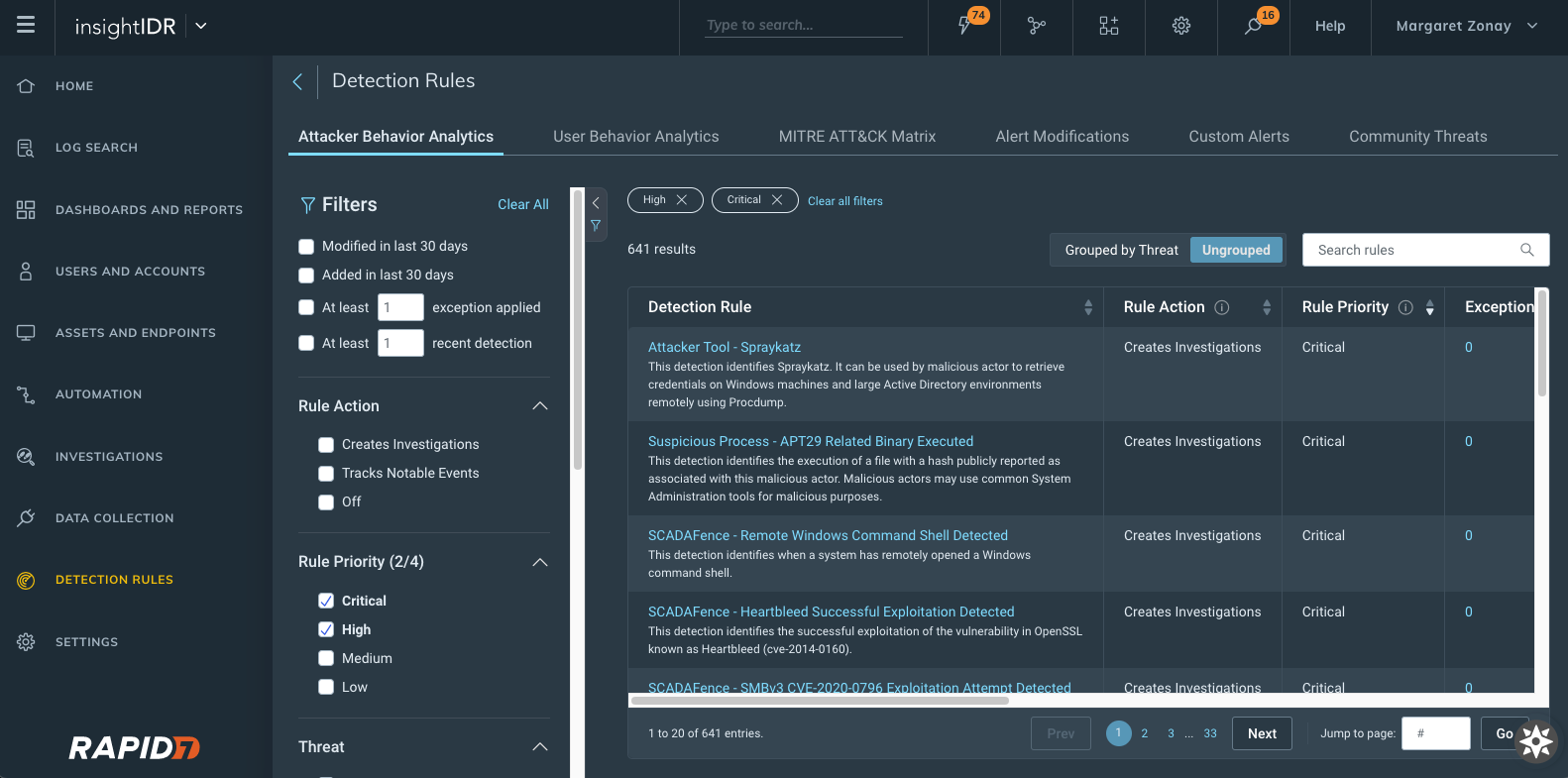
- New detection rules management interface: With this new interface, you can see a priority field for each detection provided by InsightIDR with new actions available.
- Change priority of detections and exceptions that are set to Creates Investigation as the Rule Action.
- View and sort on priority from the main detection management screen.
- More details on our detection rules experience can be found in our help docs, here.
- Customizable priorities for UBA detection rules and custom alerts: Customers can now associate a rule priority (Critical, High, Medium, or Low) for all of their UBA and custom alert detection rules. The priority is subsequently applied to investigations created by a detection rule.
- A simplified way to create exceptions: We added a new section to detection rule details within "create exception" to better inform on which data to write exceptions against. This will show up to the 5 most recent matches associated with that said detection rule — so now, when you go to write exceptions, you have all the information you may need all within one window.
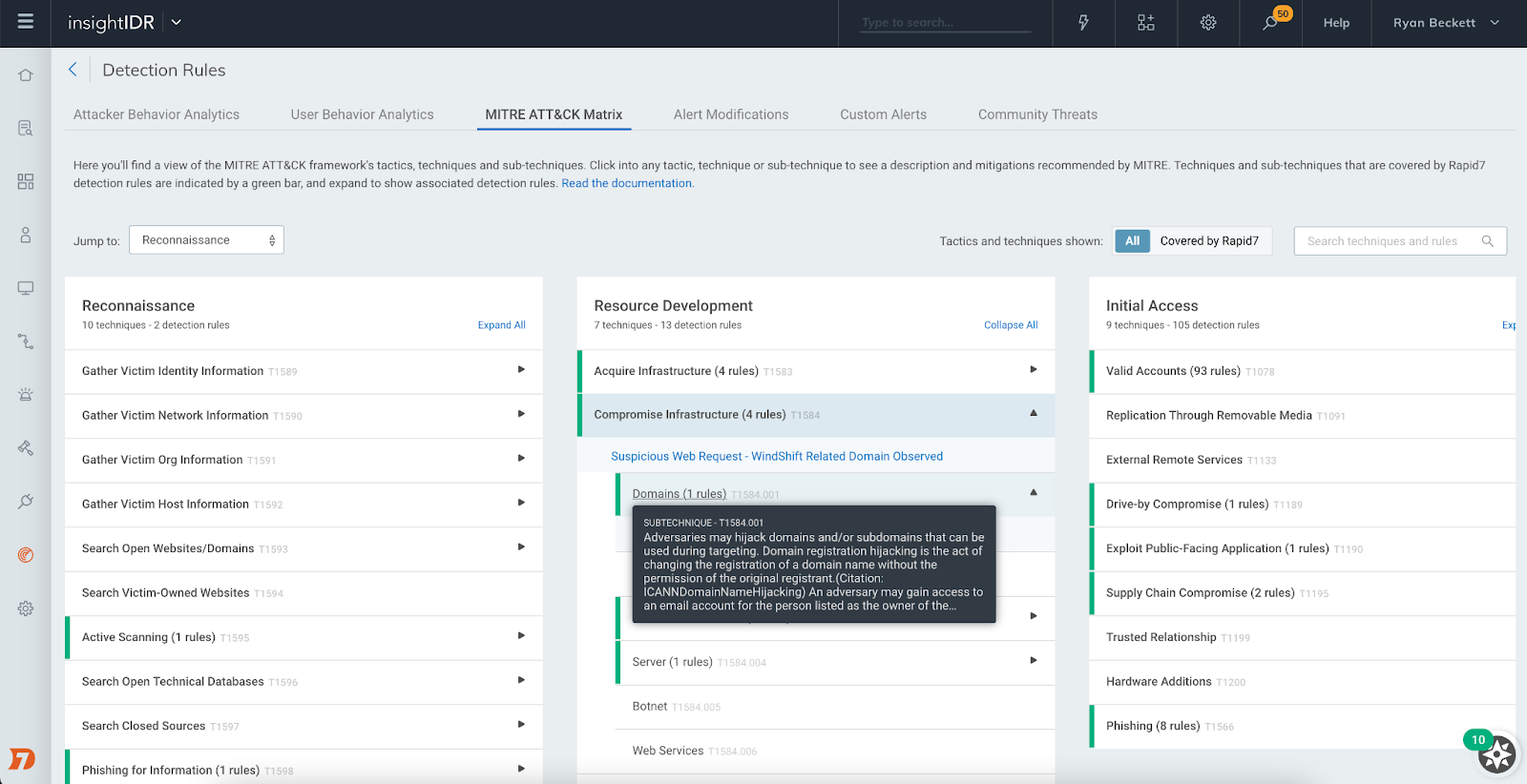
MITRE ATT&CK Matrix for detection rules
This new view maps detection rules to MITRE tactics and techniques commonly used by attackers. The view lets you see where you have coverage with Rapid7's out-of-the-box detection rules for common attacker use cases and dig into each rule to understand the nature of that detection.
Investigation Management reimagined
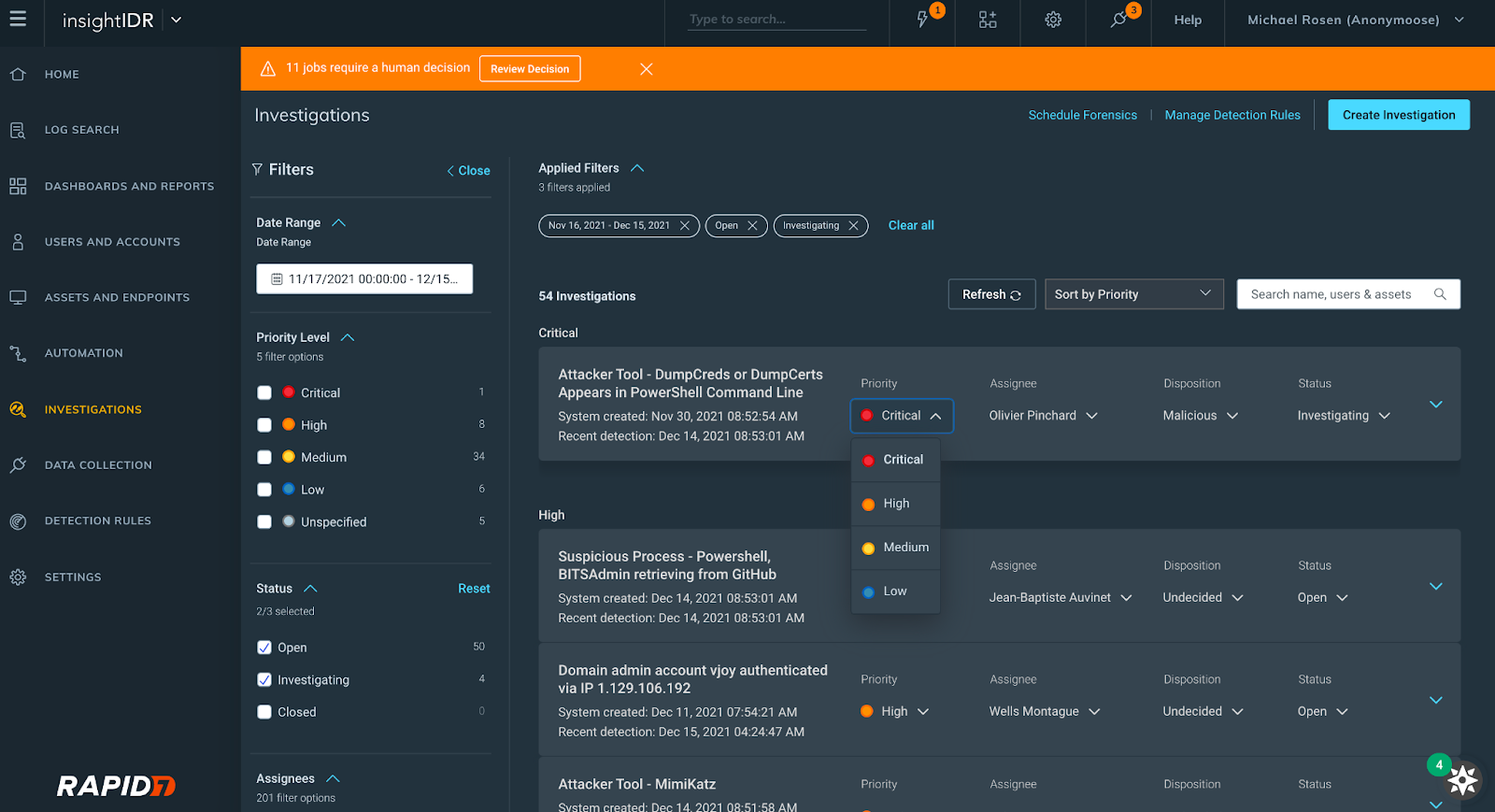
At Rapid7, we know how limited a security analyst's time is, so we reconfigured our Investigation Management experience to help our users improve the speed and quality of their decision-making when it comes to investigations. Here's what you can expect:
- A revamped user interface with expandable cards displaying investigation information
- The ability to view, set, and update the priority, status, or disposition of an investigation
- Filtering by the following fields: date range, assignee, status, priority level
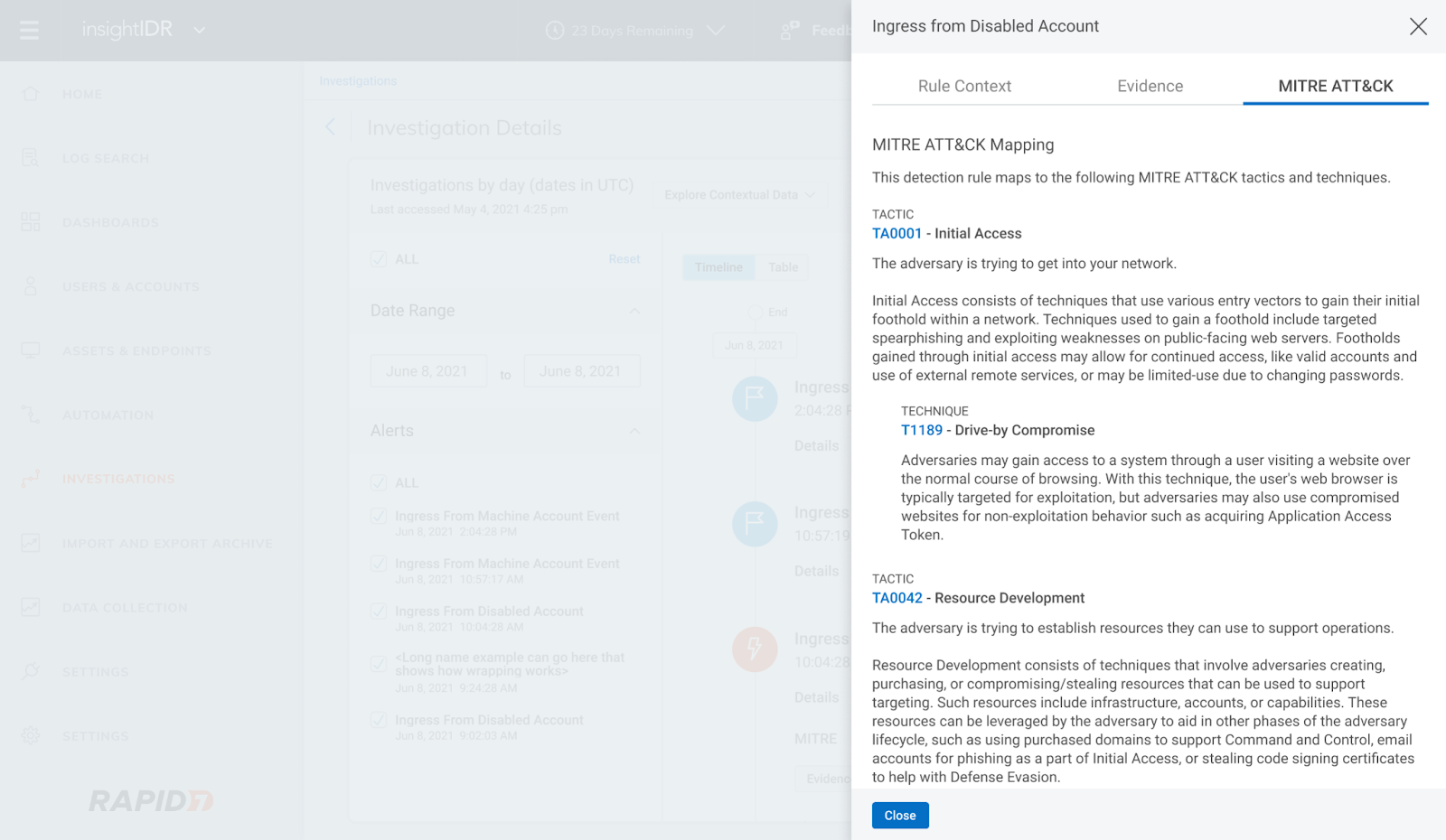
We also introduced MITRE-driven insights in Investigations. Now, you can click into the new MITRE ATT&CK tab of the Evidence panel in Investigation to see descriptions of each tactic, technique, and sub-technique curated by MITRE and link out to attack.mitre.org for more information.
Rapid7's ongoing emergent threat response to Log4Shell
Like the rest of the security community, we have been internally responding to the critical remote code execution vulnerability in Apache's Log4j Java library (a.k.a. Log4Shell).
Through continuous collaboration and ongoing threat landscape monitoring, our Incident Response, Threat Intelligence and Detection Engineering, and MDR teams are working together to provide product coverage for the latest techniques being used by malicious actors. You can see updates on our InsightIDR and MDR detection coverage here and in-product.
Stay up to date with the latest on Log4Shell:
- View Log4Shell AttackerKB for our analysis
- Check out The Everyperson's Guide to Log4Shell
A continually expanding library of pre-built dashboards
InsightIDR's Dashboard Library has a growing repository of pre-built dashboards to save you time and eliminate the need for you to build them from scratch. In Q4, we released 15 new pre-built dashboards covering:
- Compliance (PCI, HIPAA, ISO)
- General Security (Firewall, Asset Authentication)
- Security Tools (Okta, Palo Alto, Crowdstrike)
- Enhanced Network Traffic Analysis
- Cloud Security
Additional dashboard and reporting updates
- Updates to dashboard filtering: Dashboard Filtering gives users the ability to further query LEQL statements and the data across all the cards in their dashboard. Customers can now populate the dashboard filter with Saved Queries from Log Search, as well as save a filter to a dashboard, eliminating the need to rebuild it every session.
- Chart captions: We've added the ability for users to write plain text captions on charts to provide extra context about a visualization.
- Multi-group-by queries and drill-in functionality: We've enabled Multi-group-by queries (already being used in Log search) so that customers can leverage these in their dashboards and create cards with layered data that they can drill in and out of.
Updates to Log Search and Event Sources
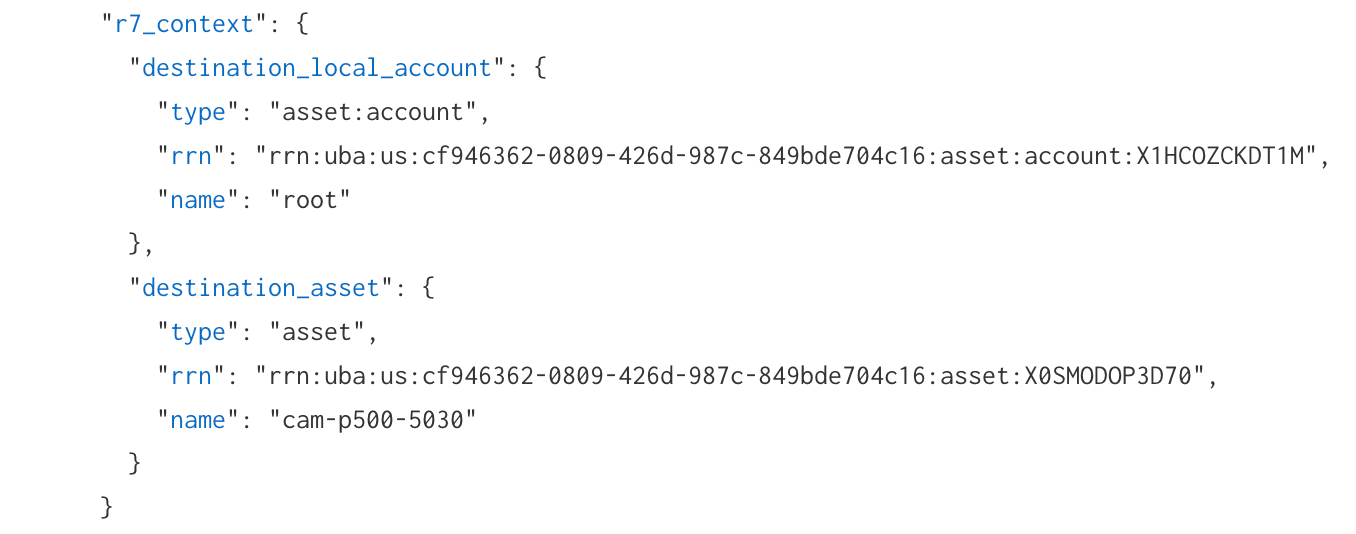
We recently introduced Rapid7 Resource Names (RRN), which are unique identifiers added to users, assets, and accounts in log search. An RRN serves as a unique identifier for platform resources at Rapid7. This unique identifier will stay consistent with the resource regardless of any number of names/labels associated with the resource.
In log search, an “R7_context" object has been added for log sets that have an attributed user, asset, account, or local accounts. Within the “R7_context" object, you will see any applicable RRNs appended. You can utilize the RRN as a search in log search or in the global search (which will link to users and accounts or assets and endpoints pages) to assist with more reliable searches for investigation processes.
Event source updates
- Log Line Attribution for Palo Alto Firewall & VPN, Proofpoint TAP, Fortinet Fortigate: When setting up an event source you now have an option to leverage information directly present in source log lines, rather than relying solely on InsightIDR's traditional attribution engine.
- Cylance Protect Cloud event source: You can configure CylancePROTECT cloud to send detection events to InsightIDR to generate virus infection and third-party alerts.
Updates to Network Traffic Analysis capabilities
Insight Network Sensor optimized for 10Gbs+ deployments: We have introduced a range of performance upgrades that make high-speed traffic analysis more accessible using off-the-shelf hardware, so you're able to gain east-west and north-south traffic visibility within physical, virtual and cloud based networks. If you want to take full advantage of these updates check out the updated sensor requirements here.
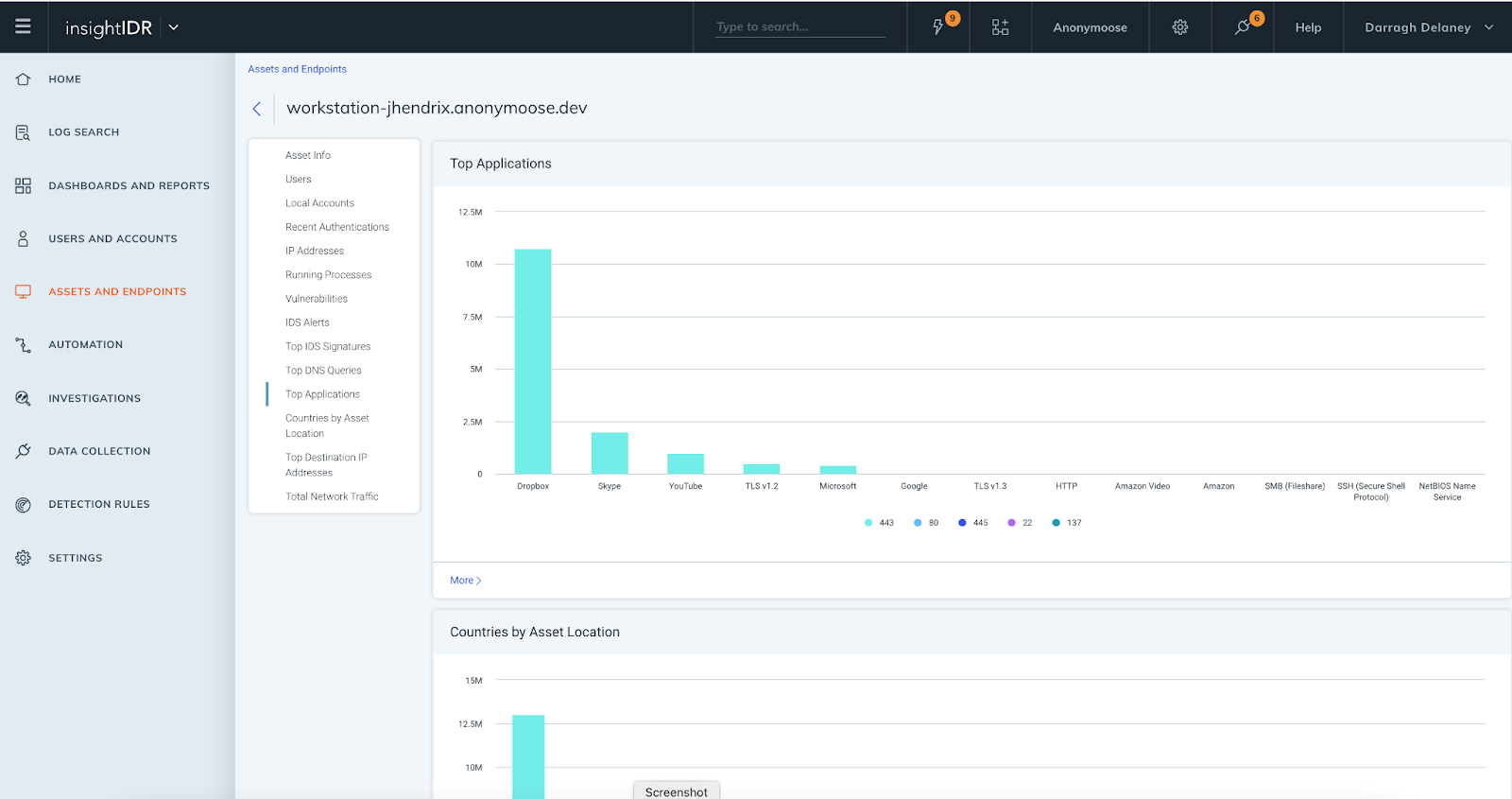
InsightIDR Asset Page Updates: We have introduced additional data elements and visuals to the Assets page. This delivers greater context for investigations and enables faster troubleshooting, as assets and user information is in one location. All customers have access to:
- Top IDS events triggered by asset
- Top DNS queries
For customers with Insight Network Sensors and ENTA, these additional elements are available:
- Top Applications
- Countries by Asset Location
- Top Destination IP Addresses
Stay tuned!
As always, we're continuing to work on exciting product enhancements and releases throughout the year. Keep an eye on our blog and release notes as we continue to highlight the latest in detection and response at Rapid7.

