We were presented with a remarkably rich source of intelligence with the leaked communications from the Conti ransomware group.
It’s a compelling and insightful read. The leaked information contains details on messages, including information on timestamps, sender, receiver, and the actual body of the message itself.
While the messages themselves are revealing, the messaging patterns provide another dimension of insight into the Conti organization.
Analyzing the Conti Ransomware messages
Graph analysis as an analytical method enables us to extract information about the structure and behaviors of the organization.
When we say “graph analysis” in this case, we’re not referring to just looking at interesting pictures of data (though interesting pictures are certainly a possible output); we are referring to a body of mathematical study that focuses on distinct entities and their interconnections.
The distinct entities in this case are the unique communicators represented in the Conti leaks. The interconnections are the messaging paths between those communicators.
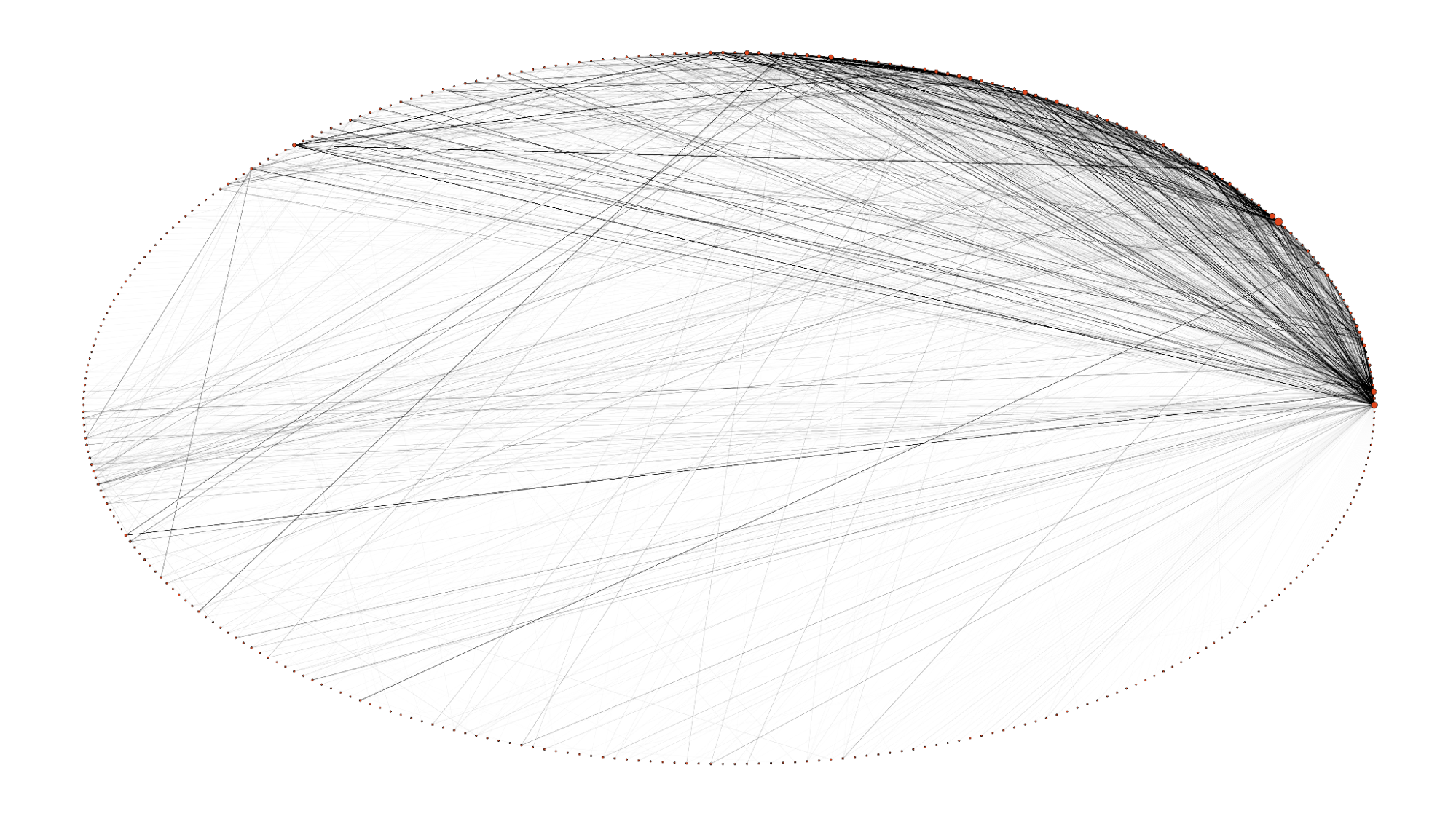
Without labels, this visual in of itself seems obscure, but this represents the communication network of the Conti ransomware group. The little dots – the nodes – forming an ellipse represent individual communicators. The lines – the edges – connecting those nodes represent shared messages. The darkness of the edges represents a degree measure, or the frequency of communication in this case.
What they might tell us
There are a lot of calculations happening behind the scenes, and the visual conveys a sense that communication within Conti doesn’t happen uniformly, which quite frankly is probably representative of most organizations.
We see here that there are certain nodes that are very frequently communicated with. Why might that be the case? Hard to say without going into further analysis, but it’s likely due to those nodes being very loquacious and gregarious, or perhaps the nodes represent key figures in the organization that are frequently being consulted and are issuing guidance and directives.
We can restructure this graph into an arc diagram and cut down on the noise with some admittedly arbitrary filters to get a cleaner view of the overall picture. In this case, we’re looking only at the communications from 2022, and we further limited the set of nodes that appear to those with a high frequency of communication measure.
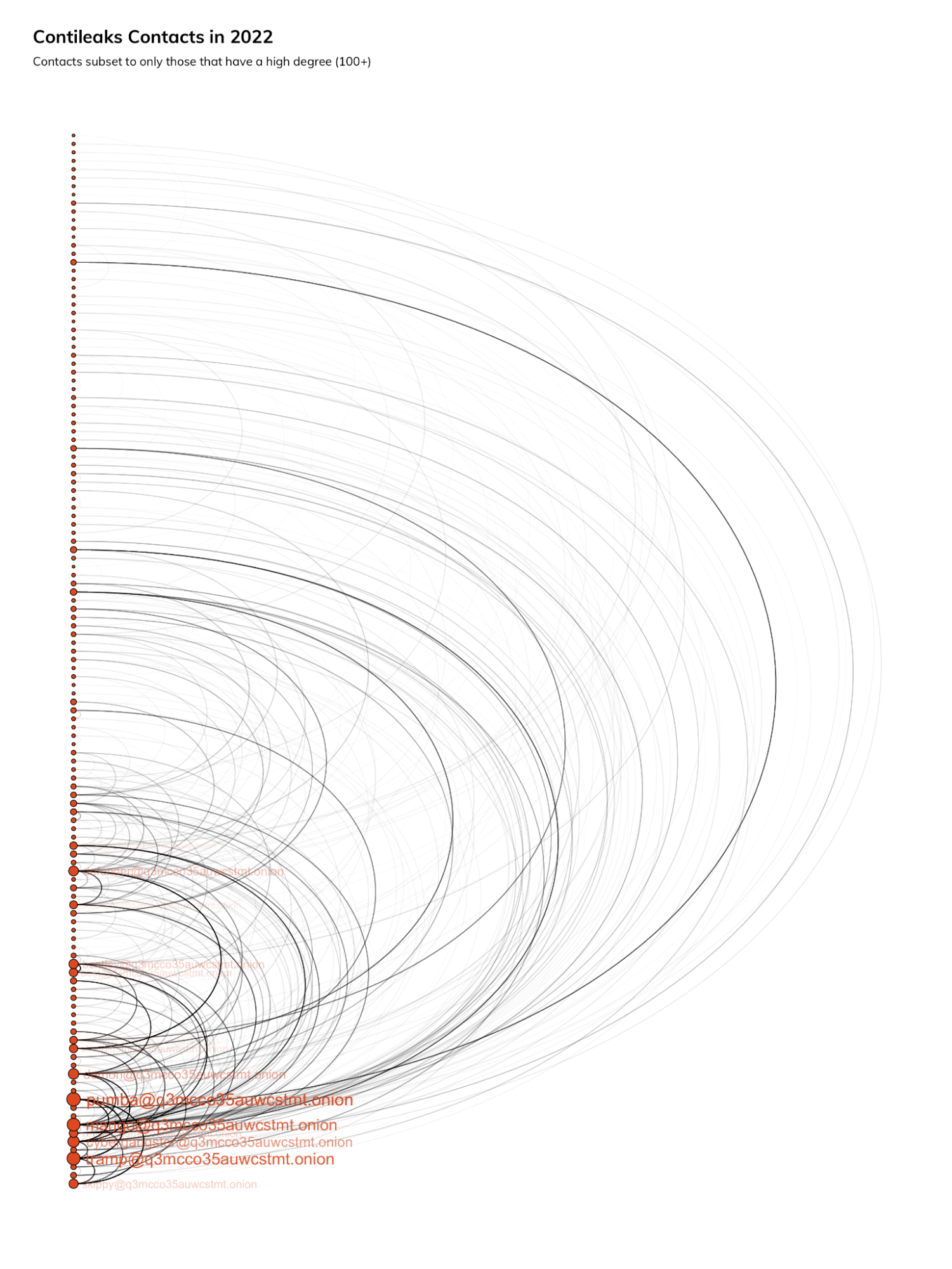
From this approach, we can get a sense of the set of recently most active communicators within Conti. Whether these prominent individuals are just chatty or leaders is unclear, but whatever the case, a lot of communications -- and presumably intelligence – is going to and from them. If they are relays, then a lot of information is going through them.
If we’re talking about relays, then what we’re really looking for is a measure of betweenness centrality, which typically represents the amount of influence specific nodes have on the flow within a graph structure.
In other applications, such as for corporate entities or criminal organizations, the individuals that are characterized by high betweenness centrality are oftentimes key linchpins of the organization. Their removal from the organization often manifests as severe disruptions to the organization.
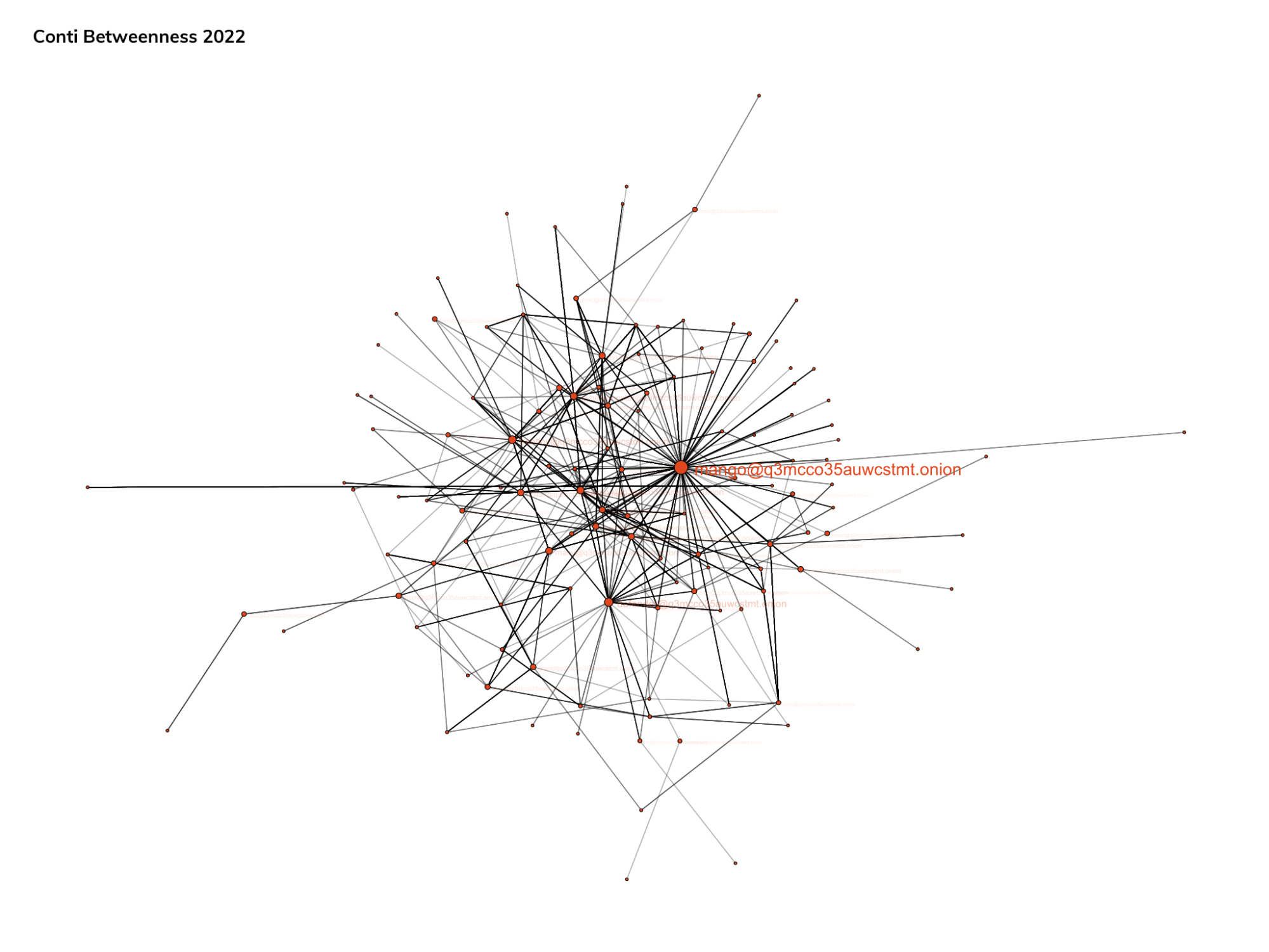
Upon deeper review of the text, it appears one communicator in particular, “buza”, is highly referenced by other communicators in decision-making contexts, though “buza” themselves is not an active communicator, relatively speaking. From this, we might surmise that “buza” is a leading figure within the organization.
If we focus only on adjacent nodes, the nodes that are directly connected to “buza”, we arrive at a view that could include “buza” at the center and the lieutenants of the organization surrounding it in a fairly classic spoke and wheel pattern. The size of the different contacts reflect how frequently they communicate with “buza,” which might in turn suggest their significance within the organization.
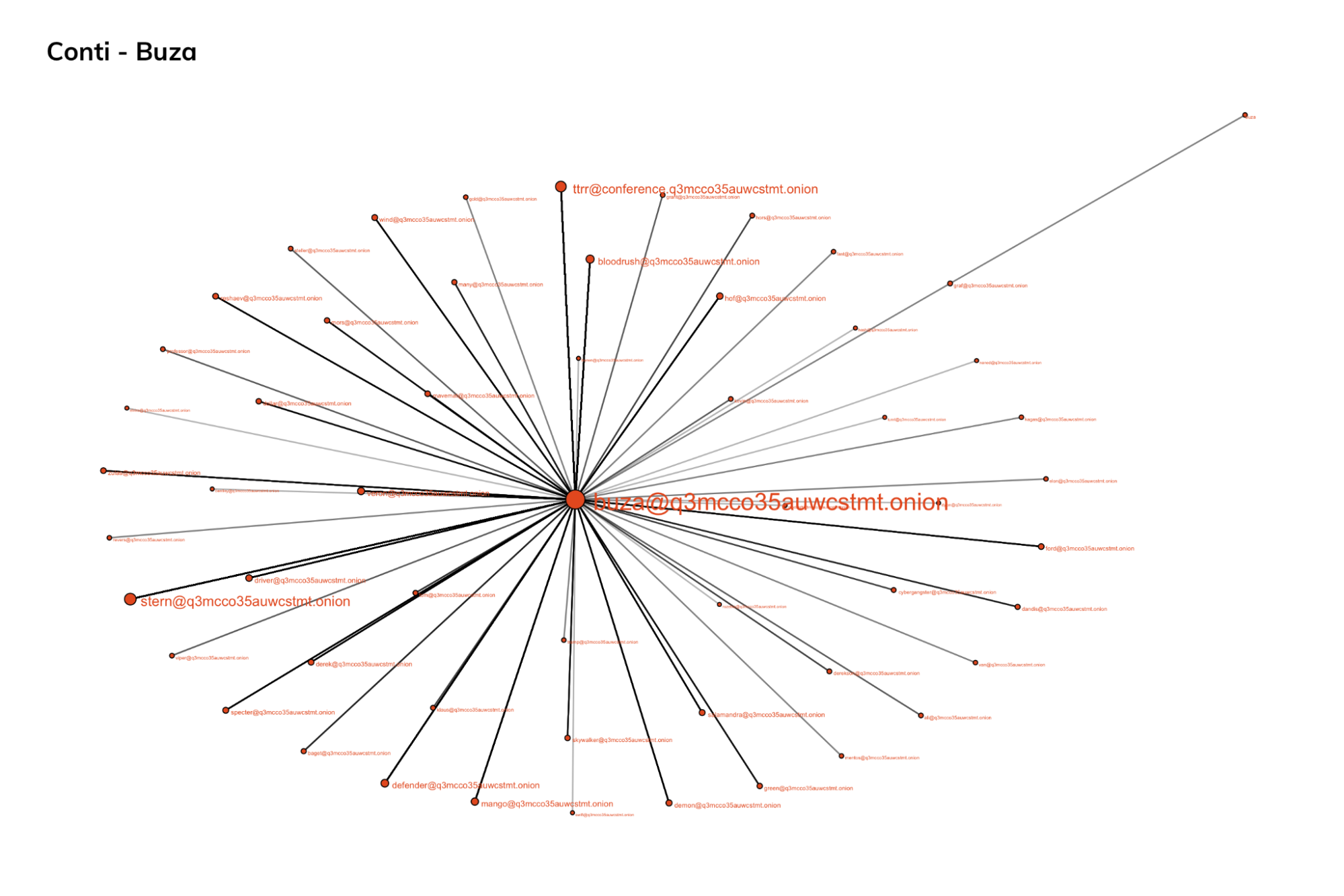
This graph analysis approach so far is really just scratching the surface of what’s possible. With further analysis, possibly combined with more in-depth text analysis methods, we can extract even more revelations about the Conti group, their areas of focus, and from there we can perhaps derive effective intelligence that can better enable defenders to secure their own organizations from similar threats.
Additional reading:
- Conti Ransomware Group Internal Chats Leaked Over Russia-Ukraine Conflict
- Russia/Ukraine Conflict: What Is Rapid7 Doing to Protect My Organization?
- Staying Secure in a Global Cyber Conflict
- Prudent Cybersecurity Preparation for the Potential Russia-Ukraine Conflict
NEVER MISS A BLOG
Get the latest stories, expertise, and news about security today.
Subscribe